Jul 10, 2024NewsroomCybersecurity / Phishing Attack Google on Wednesday announced that it’s making available passkeys for high-risk users to enroll in its Advanced Protection Program (APP). “Users traditionally needed a physical security key for APP — now they can choose a passkey to secure their account,” Shuvo Chatterjee, product lead of APP, said. Passkeys are…
Read MoreA covert Russian government-operated social media bot farm that used generative AI to spread disinformation to global users has been disrupted by a joint FBI-international cybersecurity forces operation. Affiliates of a Russian state-sponsored media organization Russia Today (RT), used Meliorator — an AI-enabled bot farm generation and management software–to set up over 1000 X (formerly…
Read MoreGoogle announced today that passkeys are now available for high-risk users when enrolling in the Advanced Protection Program, which provides the strongest level of account security. The Advanced Protection Program is a free service that protects the accounts of users such as activists, journalists, business leaders, and political teams, who are at a higher risk of…
Read MoreA large-scale fraud campaign with over 700 domain names is likely targeting Russian-speaking users looking to purchase tickets for the Summer Olympics in Paris. The operation offers fake tickets to the Olympic Games and appears to take advantage of other major sports and music events. Researchers analyzing the campaign are calling it Ticket Heist and…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/digital-forensics-in-the-age-of-cryptocurrency-investigating-blockchain-and-crypto-crimes” on this server. Reference #18.e6d7ce17.1720605955.746b0c73 https://errors.edgesuite.net/18.e6d7ce17.1720605955.746b0c73 Source link lol
Read MoreJul 10, 2024NewsroomOnline Scam / Blockchain Cryptocurrency analysts have shed light on an online marketplace called HuiOne Guarantee that’s widely used by cybercriminals in Southeast Asia, particularly those linked to pig butchering scams. “Merchants on the platform offer technology, data, and money laundering services, and have engaged in transactions totaling at least $11 billion,” Elliptic…
Read MoreScams Scammers gonna scam scam scam, so before hunting for your tickets to a Taylor Swift gig or other in-demand events, learn how to stop fraudsters from leaving a blank space in your bank account 09 Jul 2024 • , 5 min. read Thanks to advances in technology, buying tickets to your favorite show has…
Read MoreDespite the SBOM’s conceptual attractiveness as a simple tool for spotting potentially problematic software components, its value is still too limited to be helpful. “What I’m seeing is that SBOM is too nascent for department and agency proactive use,” Rebecca McWhite, cyber supply chain risk management technical Lead at NIST, said during the CISA conference.…
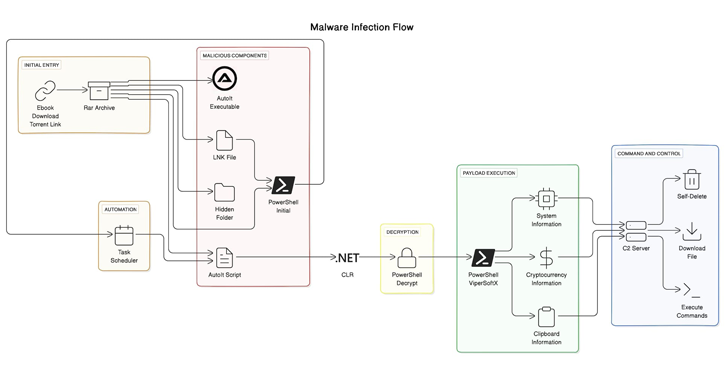
Read MoreJul 10, 2024NewsroomEndpoint Security / Threat Intelligence The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks over torrents. “A notable aspect of the current variant of ViperSoftX is that it uses the Common Language Runtime (CLR) to dynamically load and run PowerShell commands, thereby creating a PowerShell environment within AutoIt for…
Read MoreHe believes these dual-title roles can provide a more direct reporting line to the CEO or board, which is important for risk reporting. It gives the CISO greater autonomy to report to the board and helps them understand business risk because the CISO is looking across all the different parts of the organization. “It’s not…
Read MoreRecent Posts
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption