John Tavares tells CRN he plans to double down on channel partners as part of a growth push at the cloud security unicorn. Cloud security unicorn Orca Security announced Tuesday it has named Dell Technologies veteran John Tavares as its new channel chief, with an aim toward doubling down on partners as part of a…
Read MoreEvolve Bank & Trust (Evolve) is sending notices of a data breach to 7.6 million Americans whose data was stolen during a recent LockBit ransomware attack. In June, LockBit published false claims that it breached the U.S. Federal Reserve. It was later determined that the leaked data actually belonged to Evolve Bank & Trust. Evolve confirmed…
Read MoreThere was a video chat, phone messages and a lot of back and forth before Beau’s cousin began to wonder if he was thinking straight, and called to see if we thought he was being scammed. This week we get a rare look at a pig butcher in action. It’s not always easy to tell…
Read MoreBased on user posts to Microsoft-owned social network LinkedIn, the cuts have hit a variety of managers, engineers and other job titles in Microsoft. Microsoft’s new fiscal year has started with a round of layoffs and some changes in its partner program, especially around requirements for specializations. Layoffs aren’t unusual for Microsoft this time of…
Read MoreJul 09, 2024NewsroomVulnerability / Network Security Cybersecurity researchers have discovered a security vulnerability in the RADIUS network authentication protocol called BlastRADIUS that could be exploited by an attacker to stage Mallory-in-the-middle (MitM) attacks and bypass integrity checks under certain circumstances. “The RADIUS protocol allows certain Access-Request messages to have no integrity or authentication checks,” InkBridge…
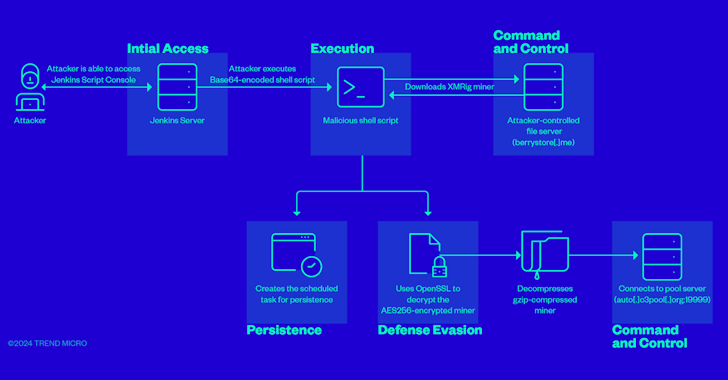
Read MoreJul 09, 2024NewsroomCI/CD Security / Server Security Cybersecurity researchers have found that it’s possible for attackers to weaponize improperly configured Jenkins Script Console instances to further criminal activities such as cryptocurrency mining. “Misconfigurations such as improperly set up authentication mechanisms expose the ‘/script’ endpoint to attackers,” Trend Micro’s Shubham Singh and Sunil Bharti said in…
Read MoreJul 09, 2024Newsroom Military personnel from Middle East countries are the target of an ongoing surveillanceware operation that delivers an Android data-gathering tool called GuardZoo. The campaign, believed to have commenced as early as October 2019, has been attributed to a Houthi-aligned threat actor based on the application lures, command-and-control (C2) server logs, targeting footprint,…
Read MoreClear Web vs. Deep Web vs. Dark Web Threat intelligence professionals divide the internet into three main components: Clear Web – Web assets that can be viewed through public search engines, including media, blogs, and other pages and sites. Deep Web – Websites and forums that are unindexed by search engines. For example, webmail, online…
Read More“Typically, after successful initial access APT40 focuses on establishing persistence to maintain access on the victim’s environment,” said the advisory. “However, as persistence occurs early in an intrusion, it is more likely to be observed in all intrusions regardless of the extent of compromise or further actions taken.” A concerning trend identified in the advisory…
Read MoreJul 09, 2024NewsroomCyber Espionage / Threat Intelligence Cybersecurity agencies from Australia, Canada, Germany, Japan, New Zealand, South Korea, the U.K., and the U.S. have released a joint advisory about a China-linked cyber espionage group called APT40, warning about its ability to co-opt exploits for newly disclosed security flaws within hours or days of public release.…
Read MoreRecent Posts
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks