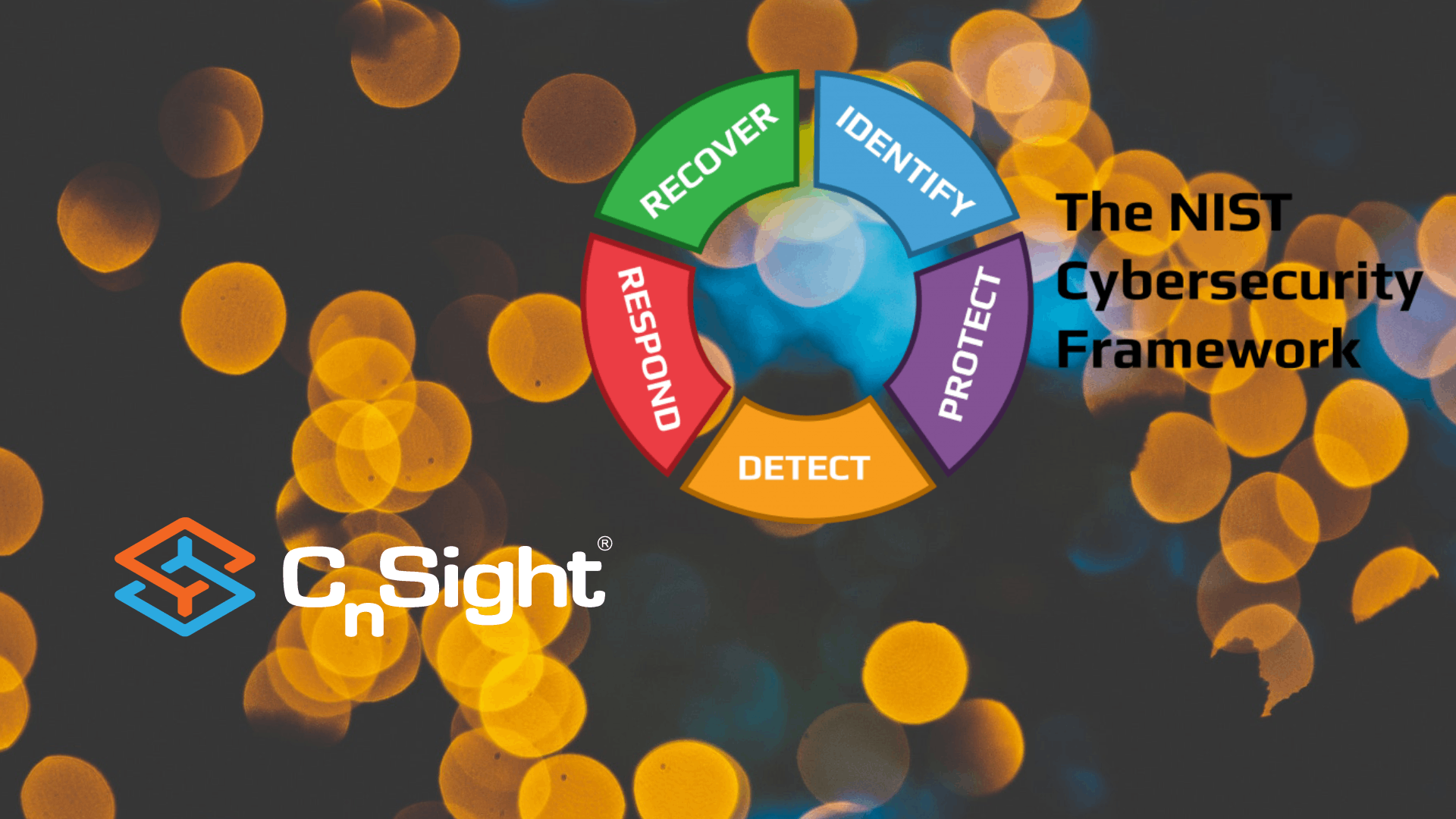
Cybersecurity Performance Management Awareness Month – How CPM helps you satisfy NIST CSF “Respond” controls – CnSight.io – Cybersecurity Performance Improvement
by nlqip
To celebrate Cyber Awareness Month, we’re releasing a series of posts outlining ways Cybersecurity Performance Management (CPM)TM can help you improve your cyber performance, reduce risk, and increase cyber ROI—all through the lens of the NIST Cybersecurity Framework (CSF). Last week, we talked about the “Detect” Security Function, which you can find here. We’ll take you…
Read MoreCybersecurity Performance Management Awareness Month – How CPM helps you satisfy NIST CSF “Recover” controls – CnSight.io – Cybersecurity Performance Improvement
by nlqip
To celebrate Cyber Awareness Month, we’re releasing a series of posts outlining ways Cybersecurity Performance Management (CPM)TM can help you improve your cyber performance, reduce risk, and increase cyber ROI—all through the lens of the NIST Cybersecurity Framework (CSF). Last week, we talked about the “Recover” Security Function, which you can find here. We’ll take…
Read MoreCybersecurity Performance Management Awareness Month – How CPM aligns with the new “Govern” Security Function – CnSight.io – Cybersecurity Performance Improvement
by nlqip
To celebrate Cyber Awareness Month, we’ve been releasing a series of posts outlining ways Cybersecurity Performance Management (CPM)TM can help you improve your cyber performance, reduce risk, and increase cyber ROI—all through the lens of the NIST Cybersecurity Framework (CSF). Last week, we talked about the “Recover” Security Function, which you can find here. Today…
Read MoreSafeguarding Your Business: Strategies to Combat Rapid Vulnerability Exploitation – CnSight.io – Cybersecurity Performance Improvement
by nlqip
In recent years, businesses have struggle in the face of an ever-growing threat from cybercriminals. The increased sophistication and automation of malware distribution has resulted in an arms race between malware developers and system owners, who need to be on top of their game in remediating flaws as they become known. Rapid vulnerability exploitation has…
Read MoreComputer hardware maker Zotac has exposed return merchandise authorization (RMA) requests and related documents online for an unknown period, exposing sensitive customer information. Zotac, known for its range of compact and mini PCs, high-performance graphics cards, motherboards, and computer accessories, has misconfigured the web folders that hold RMA data, resulting in them being indexed by…
Read MoreEnhancing Cybersecurity with CISA’s Cross-Sector Cybersecurity Performance Goals – CnSight.io – Cybersecurity Performance Improvement
by nlqip
In today’s cybersecurity landscape, ensuring the implementation of best practices is essential for a resilient critical infrastructure where negative public impact is minimized when an event occurs. The Cybersecurity and Infrastructure Security Agency (CISA) has developed Cross-Sector Cybersecurity Performance Goals (CPGs) to help organizations prioritize their cybersecurity efforts. In this post we’ll take a closer…
Read MoreIn an ongoing extortion campaign against Ticketmaster, threat actors have leaked almost 39,000 print-at-home tickets for 150 upcoming concerts and events, including Pearl Jam, Phish, Tate McCrae, and Foo Fighters. The tickets were leaked by a threat actor known as ‘Sp1derHunters,’ who is selling data stolen in recent data theft attacks from Snowflake accounts. In April,…
Read MoreA May 2024 data breach disclosed by American luxury retailer and department store chain Neiman Marcus last month has exposed more than 31 million customer email addresses, according to Have I Been Pwned founder Troy Hunt, who analyzed the stolen data. Hunt’s findings come after the company filed a breach notification with the Office of…
Read MoreThe Internet of Things (IoT) has revolutionized how we interact with technology, but it has also brought significant cybersecurity challenges. As IoT devices proliferate, from smart homes to industrial systems, they create numerous entry points for cyber threats. The sensitive data these devices handle and their integration into critical infrastructure underscore the need for robust…
Read More‘I’ve been out preaching this for well over a year now, that data center capacity is going to be an issue in this industry. … Trying to go out and find any capacity for this, of any meaningful size right now, it’s impossible. It doesn’t exist,’ Applied Digital CEO Wes Cummins tells CRN. Data center…
Read MoreRecent Posts
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks