Antivirus company Avast have discovered a weakness in the cryptographic scheme of the DoNex ransomware family and released a decryptor so victims can recover their files for free. The company says it has been working with law enforcement to privately provide the decryptor to DoNex ransomware victims since March 2024. Cybersecurity vendors commonly distribute decryptors in…
Read MoreMicrosoft reminded customers today that multiple editions of Windows 11, version 22H2, will reach the end of servicing (EOS) in three months, on October 8, 2024. This applies to Windows 11 22H2 Home, Pro, Pro Education, and Pro for Workstations editions released on September 20, 2022. “The upcoming October 2024 security update, to be released…
Read More‘Data centers have been built the way they have been built for the last 30 years. That isn’t going to get us to the next 30 years. That is going to have to change,’ Arthur Lewis, president of Dell’s Infrastructure Solutions Group, tells CRN. Arthur Lewis, president of Dell Technologies’ Infrastructure Solutions Group, said the…
Read MoreOn the CSRB’s Non-Investigation of the SolarWinds Attack ProPublica has a long investigative article on how the Cyber Safety Review Board failed to investigate the SolarWinds attack, and specifically Microsoft’s culpability, even though they were directed by President Biden to do so. Tags: cyberattack, cyberespionage, DHS, Microsoft, national security policy, Russia Posted on July 8,…
Read MoreMicrosoft has finally released a spell check and autocorrect feature in Notepad for all Windows 11 users, forty-one years after the program was introduced in 1983. The new features have been tested by Windows Insiders since March but have started to roll out to all Windows 11 users over the past couple of days. With…
Read MoreApple has removed 25 virtual private network (VPN) apps from the Russian App Store at the request of Roskomnadzor, Russia’s telecommunications watchdog. Roskomnadzor confirmed to Interfax that the order targets multiple apps (including NordVPN, Proton VPN, Red Shield VPN, Planet VPN, Hidemy.Name VPN, Le VPN, and PIA VPN) used to gain access to content tagged…
Read MoreJul 08, 2024NewsroomCyber Espionage / Cloud Security A previously undocumented advanced persistent threat (APT) group dubbed CloudSorcerer has been observed targeting Russian government entities by leveraging cloud services for command-and-control (C2) and data exfiltration. Cybersecurity firm Kaspersky, which discovered the activity in May 2024, the tradecraft adopted by the threat actor bears similarities with that…
Read MoreA remote code execution vulnerability in the Ghostscript document conversion toolkit, widely used on Linux systems, is currently being exploited in attacks. Ghostscript comes pre-installed on many Linux distributions and is used by various document conversion software, including ImageMagick, LibreOffice, GIMP, Inkscape, Scribus, and the CUPS printing system. Tracked as CVE-2024-29510, this format string vulnerability…
Read MoreHPE has filed with the European regulatory commissions for approval to purchase Juniper Networks. Here’s the timeline for the blockbuster $14 billion merger. Hewlett Packard Enterprise has filed with the European Commission for regulatory approval of its blockbuster $14 billion acquisition of Juniper Networks. European regulators now have until August to either approve HPE’s deal…
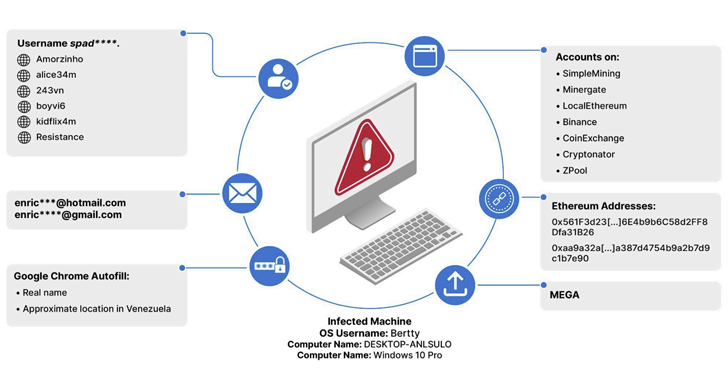
Read MoreJul 08, 2024NewsroomDark Web / Cyber Crime An analysis of information-stealing malware logs published on the dark web has led to the discovery of thousands of consumers of child sexual abuse material (CSAM), indicating how such information could be used to combat serious crimes. “Approximately 3,300 unique users were found with accounts on known CSAM…
Read MoreRecent Posts
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks