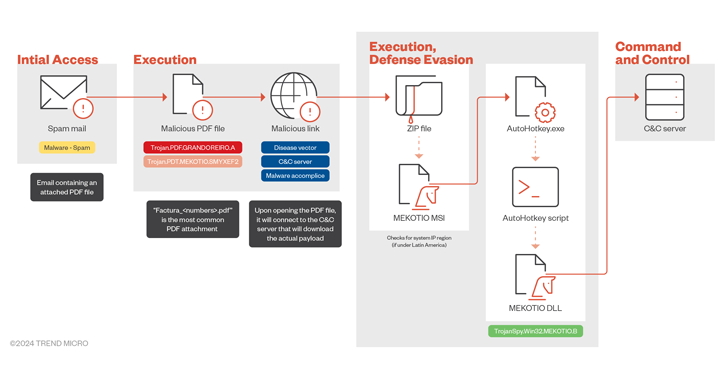
Jul 08, 2024NewsroomMalware / Cyber Threat Financial institutions in Latin America are being threatened by a banking trojan called Mekotio (aka Melcoz). That’s according to findings from Trend Micro, which said it recently observed a surge in cyber attacks distributing the Windows malware. Mekotio, known to be actively put to use since 2015, is known…
Read MoreJul 08, 2024NewsroomVulnerability / Software Security Four unpatched security flaws, including three critical ones, have been disclosed in the Gogs open-source, self-hosted Git service that could enable an authenticated attacker to breach susceptible instances, steal or wipe source code, and even plant backdoors. The vulnerabilities, according to SonarSource researchers Thomas Chauchefoin and Paul Gerste, are…
Read MoreJul 08, 2024NewsroomPrivacy / Internet Censorship Apple removed a number of virtual private network (VPN) apps in Russia from its App Store on July 4, 2024, following a request by Russia’s state communications watchdog Roskomnadzor, Russian news media reported. This includes the mobile apps of 25 VPN service providers, including ProtonVPN, Red Shield VPN, NordVPN…
Read MoreTechnical debt can be described as an accumulation of fixes and outdated systems badly in need of updating. And infrastructure, because of the size and cost of building and maintaining public and private projects such as water systems, electrical grids, telecommunications systems, and transportation systems, is particularly prone to an accumulation of such debt. “Technical…
Read MoreMedia Room
by nlqip
https://videos.tenable.com/watch/m8EtzyMKC32EeEbrxMEZyz Source link lol
Read MoreE-commerce platform Shopify denies it suffered a data breach after a threat actor began selling customer data they claim was stolen from the company’s network. “Shopify systems have not experienced a security incident,” Shopify told BleepingComputer. “The data loss reported was caused by a third-party app. The app developer intends to notify affected customers.” This statement…
Read MoreEuropol is proposing solutions to avoid challenges posed by privacy-enhancing technologies in Home Routing that hinder law enforcement’s ability to intercept communications during criminal investigations. The agency has previously highlighted in its Digital Challenges series that law enforcement problem of end-to-end encryption on communication platforms is a hurdle when it comes to collecting admissible evidence. The case…
Read MoreFriday Squid Blogging: Newly Discovered Vampire Squid A new vampire squid species was discovered in the South China Sea. Blog moderation policy. Tags: squid Posted on July 5, 2024 at 5:39 PM • Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreThe researchers notified Intel of their research in February and the company has also notified other hardware and software vendors. The company already a mitigation for Spectre-like attacks in 2018 called the indirect branch predictor barrier (IBPB). While this in theory can be used to mitigate the new Indirector attack techniques, it would have to…
Read MoreInternet giant Cloudflare reports that its DNS resolver service, 1.1.1.1, was recently unreachable or degraded for some of its customers because of a combination of Border Gateway Protocol (BGP) hijacking and a route leak. The incident occurred last week and affected 300 networks in 70 countries. Despite these numbers, the company says that the impact was “quite…
Read MoreRecent Posts
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks