Friday Squid Blogging: Newly Discovered Vampire Squid A new vampire squid species was discovered in the South China Sea. Blog moderation policy. Tags: squid Posted on July 5, 2024 at 5:39 PM • Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreThe researchers notified Intel of their research in February and the company has also notified other hardware and software vendors. The company already a mitigation for Spectre-like attacks in 2018 called the indirect branch predictor barrier (IBPB). While this in theory can be used to mitigate the new Indirector attack techniques, it would have to…
Read MoreInternet giant Cloudflare reports that its DNS resolver service, 1.1.1.1, was recently unreachable or degraded for some of its customers because of a combination of Border Gateway Protocol (BGP) hijacking and a route leak. The incident occurred last week and affected 300 networks in 70 countries. Despite these numbers, the company says that the impact was “quite…
Read MoreWith growing concern over the recently disclosed regreSSHion vulnerability, we’re explaining here what it is, why it’s so significant, what it could mean for your cloud environment and how Tenable Cloud Security can help. The newly discovered CVE-2024-6387 vulnerability in OpenSSH, named “regreSSHion,” is a critical remote code execution (RCE) flaw resulting from a race…
Read MoreHackers have leaked what they claim is Ticketmaster barcode data for 166,000 Taylor Swift Eras Tour tickets, warning that more events would be leaked if a $2 million extortion demand is not paid. In May, a well-known threat actor named ShinyHunters began selling data on 560 million Ticketmaster customers for $500,000. Ticketmaster later confirmed the…
Read MoreA new ransomware-as-a-service (RaaS) called Eldorado emerged in March and comes with locker variants for VMware ESXi and Windows. The gang has already claimed 16 victims, most of them in the U.S., in real estate, educational, healthcare, and manufacturing sectors. Researchers at cybersecurity company Group-IB monitored the Eldorado’s activity and noticed its operators promoting the malicious service on…
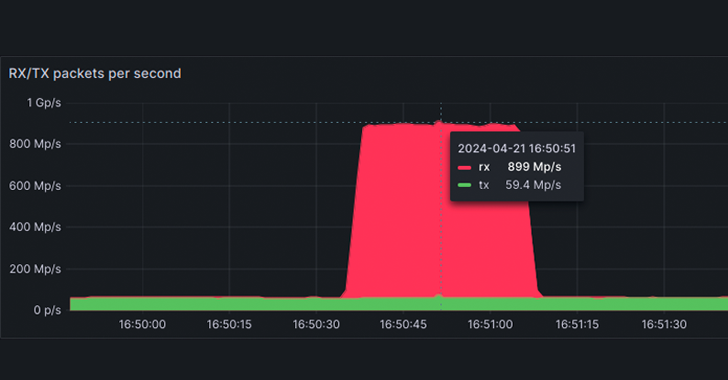
Read MoreJul 05, 2024NewsroomNetwork Security / DDoS Attack French cloud computing firm OVHcloud said it mitigated a record-breaking distributed denial-of-service (DDoS) attack in April 2024 that reached a packet rate of 840 million packets per second (Mpps). This is just above the previous record of 809 million Mpps reported by Akamai as targeting a large European…
Read MoreJul 05, 2024The Hacker NewsCybersecurity / Identity Protection Identity theft isn’t just about stolen credit cards anymore. Today, cybercriminals are using advanced tactics to infiltrate organizations and cause major damage with compromised credentials. The stakes are high: ransomware attacks, lateral movement, and devastating data breaches. Don’t be caught off guard. Join us for a groundbreaking…
Read MoreCybersecurity Snapshot: Malicious Versions of Cobalt Strike Taken Down, While Microsoft Notifies More Orgs About Midnight Blizzard Email Breach
by nlqip
Check out the results of a multinational operation against illegal instances of Cobalt Strike. Plus, more organizations are learning that Midnight Blizzard accessed their email exchanges with Microsoft. Meanwhile, Carnegie Mellon has a new report about how to fix and mitigate API vulnerabilities. And two new reports shed light on cyber insurance trends. And much…
Read MoreWhen matched, the company said it found 81 email addresses in the exported mailing list that were not part of the threat actor’s own list. Phished to a crypto drainer The phishing emails posed as an announcement claiming that the Ethereum Foundation had teamed up with the Lido decentralized autonomous organization (LidoDAO) to provide a…
Read MoreRecent Posts
- Palo Alto Networks warns of critical RCE zero-day exploited in attacks
- Microsoft just killed the Windows 10 Beta Channel for good
- Cybersecurity Snapshot: Five Eyes Rank 2023’s Most Frequently Exploited CVEs, While CSA Publishes Framework for AI System Audits
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says