

Jul 05, 2024The Hacker NewsCloud Security / Attack Surface The attack surface isn’t what it once was and it’s becoming a nightmare to protect. A constantly expanding and evolving attack surface means risk to the business has skyrocketed and current security measures are struggling to keep it protected. If you’ve clicked on this article, there’s…
Read MoreJul 05, 2024NewsroomSEO Poisoning / Cyber Attack, The malware known as GootLoader continues to be in active use by threat actors looking to deliver additional payloads to compromised hosts. “Updates to the GootLoader payload have resulted in several versions of GootLoader, with GootLoader 3 currently in active use,” cybersecurity firm Cybereason said in an analysis…
Read MoreVideo Social media sites are designed to make their users come back for more. Do laws restricting children’s exposure to addictive social media feeds have teeth or are they a political gimmick? 04 Jul 2024 Social media platforms have become a near-constant presence in our daily lives. They are a great tool to stay connected…
Read MoreWhat does a logic bomb attack do? As the Stuxnet example demonstrates, a logic bomb attack gets its name because the malicious code activates when some logical condition, or trigger, is satisfied: It can be explained as an if-then statement. There are two forms a logic bomb’s trigger can take: positive or negative. A positive trigger goes off if something happens, whereas…
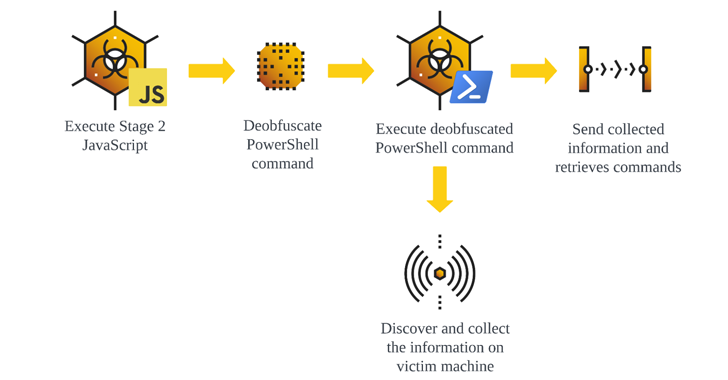
Read MoreJul 05, 2024NewsroomSupply Chain Attack / Malware The supply chain attack targeting widely-used Polyfill[.]io JavaScript library is wider in scope than previously thought, with new findings from Censys showing that over 380,000 hosts are embedding a polyfill script linking to the malicious domain as of July 2, 2024. This includes references to “https://cdn.polyfill[.]io” or “https://cdn.polyfill[.]com”…
Read MoreJul 05, 2024NewsroomNetwork Security / Cyber Attack Cybersecurity researchers have uncovered a new botnet called Zergeca that’s capable of conducting distributed denial-of-service (DDoS) attacks. Written in Golang, the botnet is so named for its reference to a string named “ootheca” present in the command-and-control (C2) servers (“ootheca[.]pw” and “ootheca[.]top”). “Functionally, Zergeca is not just a…
Read MoreA threat actor compromised Ethereum’s mailing list provider and sent to over 35,000 addresses a phishing email with a link to a malicious site running a crypto drainer. Ethereum disclosed the incident in a blog post this week and said that it had no material impact on users. Attack details The attack occurred on the…
Read MoreWhat’s happening? Security researchers have warned that a new ransomware group has taken an unusual twist on the traditional method of extorting money from its corporate victims. So what’s different this time? Whereas many ransomware attacks see a company’s company’s data exfiltrated by attackers, and the threat made that stolen data will be sold to…
Read MoreHackers are targeting older versions of the HTTP File Server (HFS) from Rejetto to drop malware and cryptocurrency mining software. Threat researchers at security company AhnLab believe that the threat actors are exploiting CVE-2024-23692, a critical-severity security issue that allows executing arbitrary commands without the need to authenticate. The vulnerability affects versions of the software up to and including 2.3m.…
Read MoreSince September 2021, Europol’s European Cybercrime Centre (EC3) assisted the operation with analytical and forensic support and enabled information exchange among all partners. Additionally, law enforcement operated a “malware information sharing platform,” inviting private partners to add real-time threat intelligence to the effort. “Over the span of the whole investigation, over 730 pieces of threat…
Read MoreRecent Posts
- Palo Alto Networks warns of critical RCE zero-day exploited in attacks
- Microsoft just killed the Windows 10 Beta Channel for good
- Cybersecurity Snapshot: Five Eyes Rank 2023’s Most Frequently Exploited CVEs, While CSA Publishes Framework for AI System Audits
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says





![Polyfill[.]io Attack Impacts Over 380,000 Hosts, Including Major Companies](https://kartwheelnewz.info/wp-content/uploads/2024/07/Polyfillio-Attack-Impacts-Over-380000-Hosts-Including-Major-Companies.png)




