“The malicious code dynamically generates payloads based on HTTP headers, activating only on specific mobile devices, evading detection, avoiding admin users and delaying execution,” according to c/side. Some of the doctored JavaScript files include a fake Google analytics link that redirects users to sports or pornography websites. As c/side warns, the content being served up…
Read More‘HP’s transformation over the past eight years has been extraordinary to watch, and I look forward to working with a stellar team of professionals to advance the shared goal of creating long-term sustainable growth,’ says Karen Parkhill, who has been Medtronic’s CFO since 2016. HP Inc. has appointed Medtronic executive Karen Parkhill as its new…
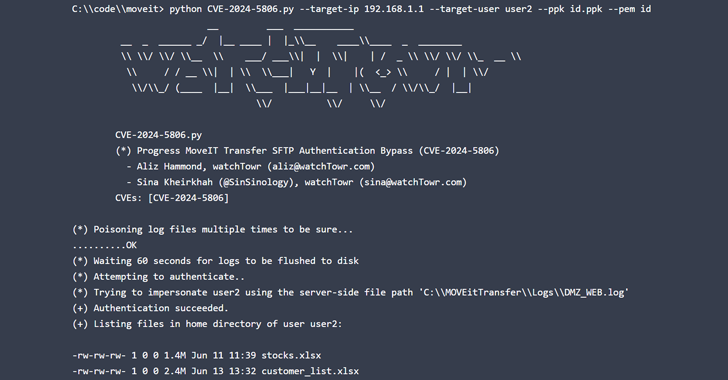
Read MoreProgress disclosed the authentication bypass vulnerability Tuesday and ‘very shortly after’ began seeing attempted exploits, according to Shadowserver researchers. Progress disclosed a critical new vulnerability in MOVEit Transfer Tuesday and “very shortly after” began seeing attempted exploits by hackers, according to researchers at Shadowserver. The disclosure comes just over a year after widespread attacks targeted…
Read More‘I was impressed by Auvik’s ability to innovate while creating a product that is easy to implement, as well as their proven track record of delivering exceptional customer value and placing the customer first,’ says Mark Ralls, Auvik’s new president. Auvik Wednesday said it appointed a new president and a new chief sales officers to…
Read MoreJun 26, 2024NewsroomVulnerability / Data Protection A newly disclosed critical security flaw impacting Progress Software MOVEit Transfer is already seeing exploitation attempts in the wild shortly after details of the bug were publicly disclosed. The vulnerability, tracked as CVE-2024-5806 (CVSS score: 9.1), concerns an authentication bypass that impacts the following versions – From 2023.0.0 before…
Read MoreThe maker of software used by thousands of car dealerships says June 30 is likely to be the soonest it will be able to recover from last week’s cyberattacks. CDK Global said Tuesday that it expects to need at least through the weekend to recover in the wake of a pair of cyberattacks, with June…
Read MoreThe June 2024 optional update for Windows 11 is now available. The latest update, KB5039302, is for Windows 11 version 22H2 and newer and brings several new features and fixes. Since this is an optional update, it doesn’t introduce major new features but focuses on improving quality and fixing bugs. This update advances Windows 11…
Read MoreCyera, Glean and xAI are among the recently founded AI companies capturing major investor attention. A data security platform powered by artificial intelligence, a provider of AI agents and assistants founded on company data, and Elon Musk’s mysterious AI company are among the most well-funded startups so far in 2024. Cyera, Glean and xAI are…
Read MoreThreat actors are already trying to exploit a critical authentication bypass flaw in Progress MOVEit Transfer, less than a day after the vendor disclosed it. MOVEit Transfer is a managed file transfer (MFT) solution used in enterprise environments to securely transfer files between business partners and customers using the SFTP, SCP, and HTTP protocols. The…
Read MoreCISA and Partners Release Guidance for Exploring Memory Safety in Critical Open Source Projects | CISA
by nlqip
Today, CISA, in partnership with the Federal Bureau of Investigation, Australian Signals Directorate’s Australian Cyber Security Centre, and Canadian Cyber Security Center, released Exploring Memory Safety in Critical Open Source Projects. This guidance was crafted to provide organizations with findings on the scale of memory safety risk in selected open source software (OSS). This joint…
Read MoreRecent Posts
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption