The Medusa banking trojan for Android has re-emerged after almost a year of keeping a lower profile in campaigns targeting France, Italy, the United States, Canada, Spain, the United Kingdom, and Turkey. The new activity has been tracked since May and relies on more compact variants that require fewer permissions and come with fresh features…
Read MoreThe modern web browser has undergone a profound transformation in recent years, becoming an indispensable tool in today’s digital age. It facilitates online communication and provides unparalleled productivity, especially as organizations continue to transition to hybrid work models and embrace cloud-based operations. Unfortunately, security infrastructures haven’t evolved as fast as they should, making these browsers…
Read MoreLuxury retailer Neiman Marcus confirmed it suffered a data breach after hackers attempted to sell the company’s database stolen in recent Snowflake data theft attacks. In a data breach notification filed with the Office of the Maine Attorney General, the company says that the breach impacted 64,472 people. “In May 2024, we learned that, between April…
Read Moreffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt…
Read MoreAI is in the news, it’s on our devices–it makes organizations run better, it can help you get into college or land a new job, and scammers increasingly use AI to swindle people more efficiently, but what else can it do? We asked two experts this week: What’s the ultimate AI crime? Cybersecurity and privacy…
Read MoreThe FBI is warning of cybercriminals posing as law firms and lawyers that offer cryptocurrency recovery services to victims of investment scams and steal funds and personal information. The latest alert is an update to similar warning from the agency’s Internet Crime Complaint Center (IC3) that alerted of an increase in scams involving fake services for…
Read MoreHere’s a look at 10 data science and machine learning tools that solution and service providers should be aware of. Deep Thoughts Data science and machine learning technologies have long been important for data analytics tasks and predictive analytical software. But with the wave of artificial intelligence and generative AI development in 2023, the importance…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/the-role-of-cybersecurity-in-modern-construction-and-manufacturing” on this server. Reference #18.cad7ce17.1719322963.1e8b3450 https://errors.edgesuite.net/18.cad7ce17.1719322963.1e8b3450 Source link lol
Read MoreUnderstanding Customer Managed Encryption Keys (CMKs) in AWS, Azure and GCP: A Comparative Insight
by nlqip
Explore critical differences in handling customer-managed encryption keys (CMKs) across AWS, Azure, and GCP to avoid security misconfigurations and protect your data effectively. Why are we here? A customer-managed encryption key (CMK) is an encryption key created, managed, and owned by the customer. This gives the customer control over its access management—that is, determining who…
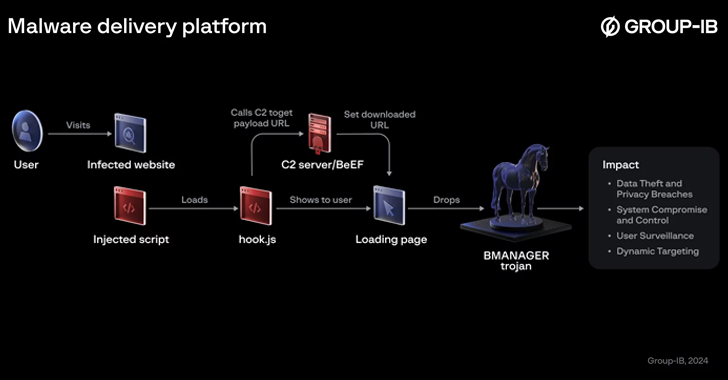
Read MoreJun 25, 2024NewsroomData Theft / Web Security A previously undocumented threat actor dubbed Boolka has been observed compromising websites with malicious scripts to deliver a modular trojan codenamed BMANAGER. “The threat actor behind this campaign has been carrying out opportunistic SQL injection attacks against websites in various countries since at least 2022,” Group-IB researchers Rustam…
Read MoreRecent Posts
- Hacker gets 10 years in prison for extorting US healthcare provider
- Hackers use macOS extended file attributes to hide malicious code
- The true (and surprising) cost of forgotten passwords
- ChatGPT allows access to underlying sandbox OS, “playbook” data
- CISA Releases Nineteen Industrial Control Systems Advisories | CISA