ASUS has released a new firmware update that addresses a vulnerability impacting seven router models that allow remote attackers to log in to devices. The flaw, tracked as CVE-2024-3080 (CVSS v3.1 score: 9.8 “critical”), is an authentication bypass vulnerability allowing unauthenticated, remote attackers to take control of the device. ASUS says the issue impacts the following router…
Read MoreImage: Midjourney A newly discovered Linux malware dubbed ‘DISGOMOJI’ uses the novel approach of utilizing emojis to execute commands on infected devices in attacks on government agencies in India. The malware was discovered by cybersecurity firm Volexity, which believes it is linked to a Pakistan-based threat actor known as ‘UTA0137.’ “In 2024, Volexity identified a…
Read MoreJun 15, 2024Newsroom Pakistan has become the latest target of a threat actor called the Smishing Triad, marking the first expansion of its footprint beyond the E.U., Saudi Arabia, the U.A.E., and the U.S. “The group’s latest tactic involves sending malicious messages on behalf of Pakistan Post to customers of mobile carriers via iMessage and…
Read MoreJun 15, 2024NewsroomCyber Espionage / Malware A suspected Pakistan-based threat actor has been linked to a cyber espionage campaign targeting Indian government entities in 2024. Cybersecurity company Volexity is tracking the activity under the moniker UTA0137, noting the adversary’s exclusive use of a malware called DISGOMOJI that’s written in Golang and is designed to infect…
Read MoreJun 14, 2024NewsroomPrivacy / Ad Tracking Google’s plans to deprecate third-party tracking cookies in its Chrome web browser with Privacy Sandbox has run into fresh trouble after Austrian privacy non-profit noyb (none of your business) said the feature can still be used to track users. “While the so-called ‘Privacy Sandbox’ is advertised as an improvement…
Read MoreJun 15, 2024NewsroomArtificial Intelligence / Privacy Meta on Friday said it’s delaying its efforts to train the company’s large language models (LLMs) using public content shared by adult users on Facebook and Instagram in the European Union following a request from the Irish Data Protection Commission (DPC). The company expressed disappointment at having to put…
Read MoreESET Research The I-SOON data leak confirms that this contractor is involved in cyberespionage for China, while Iran-aligned groups step up aggressive tactics following the Hamas-led attack on Israel in 2023 14 Jun 2024 • , 2 min. read In this episode of the ESET Research Podcast, we dissect the most interesting findings of the…
Read MoreHow Arid Viper spies on Android users in the Middle East – Week in security with Tony Anscombe
by nlqip
Video The spyware, called AridSpy by ESET, is distributed through websites that pose as various messaging apps, a job search app, and a Palestinian Civil Registry app 14 Jun 2024 This week, ESET researchers released their findings about five campaigns that used trojanized apps to target Android users in Egypt and Palestine. Initiated in 2022,…
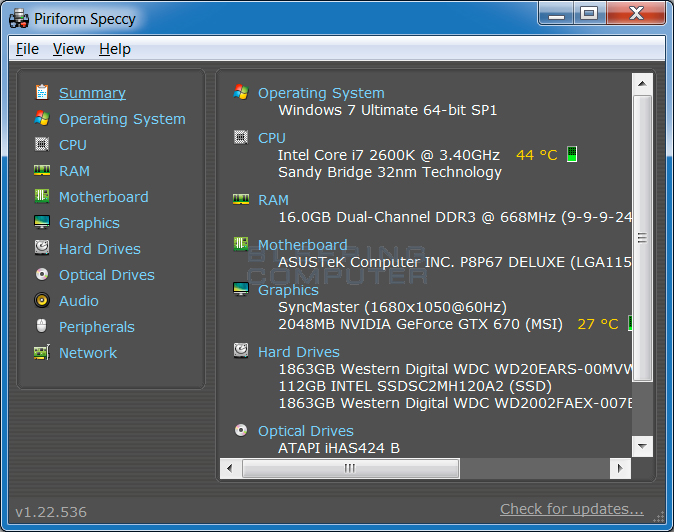
Read MoreScreenshots for Speccy BleepingComputer Review: Speccy is a tool that provides detailed information about the hardware components and operating system of the computer it is run on. This information is extremely valuable when you want to upgrade existing hardware, find out what specific hardware is installed on your computer, and whether or not the current…
Read MoreThe last 12 months have witnessed a rapid-fire round of innovation and adoption of new technologies. Powerful new identities, environments and attack methods are shaping the quickly changing cybersecurity threat landscape, rendering it more complex and causing the diffusion of risk reduction focus. New CyberArk research indicates the rise of machine identities and the increasing…
Read MoreRecent Posts
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks