CISA has added three new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-32896 Android Pixel Privilege Escalation Vulnerability CVE-2024-26169 Microsoft Windows Error Reporting Service Improper Privilege Management Vulnerability CVE-2024-4358 Progress Telerik Report Server Authentication Bypass by Spoofing Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors…
Read MoreCISA released twenty Industrial Control Systems (ICS) advisories on June 13, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-24-165-01 Siemens Mendix Applications ICSA-24-165-02 Siemens SIMATIC S7-200 SMART Devices ICSA-24-165-03 Siemens TIA Administrator ICSA-24-165-04 Siemens ST7 ScadaConnect ICSA-24-165-05 Siemens SITOP UPS1600 ICSA-24-165-06 Siemens TIM 1531 IRC ICSA-24-165-07 Siemens…
Read More6. No big deal? The OMB made a big deal of one incident involving a bad actor gaining access to the login credentials of just one employee for just 15 hours — maybe because that person worked for the Office of the Inspector General (OIG), which has full access to all records and materials available…
Read MoreThe US Cybersecurity and Infrastructure Security Agency (CISA) has warned that scammers are impersonating its employees in an attempt to commit fraud. In an alert posted on the CISA website, the organisation warned that so-called impersonation scams are on the rise. An impersonation scam is any type of fraud where a criminal pretends to be…
Read MoreFrom the editors of CSO, this enterprise buyer’s guide helps security IT staff understand what cloud access security brokers (CASBs) can do for their organizations and how to choose the right solution. Source link lol
Read MoreYouTube reportedly now injects ads directly into video streams to make it more difficult for ad blockers to block advertisements. The report comes from SponsorBlock, a third-party browser extension that crowdsources data about which video segments contain sponsored content and skips them. SponsorBlock reports that server-side ad injection will break its functionality, though solutions are…
Read MoreJun 13, 2024NewsroomThreat Intelligence / Mobile Security The threat actor known as Arid Viper has been attributed to a mobile espionage campaign that leverages trojanized Android apps to deliver a spyware strain dubbed AridSpy. “The malware is distributed through dedicated websites impersonating various messaging apps, a job opportunity app, and a Palestinian Civil Registry app,”…
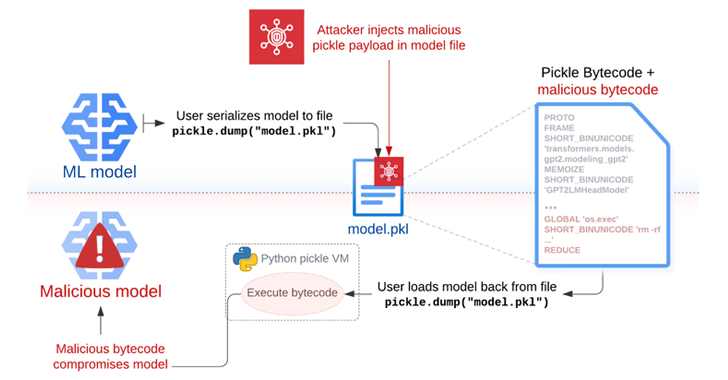
Read MoreJun 13, 2024NewsroomVulnerability / Software Security The security risks posed by the Pickle format have once again come to the fore with the discovery of a new “hybrid machine learning (ML) model exploitation technique” dubbed Sleepy Pickle. The attack method, per Trail of Bits, weaponizes the ubiquitous format used to package and distribute machine learning…
Read MoreSplunk Unveils Advanced AI Capabilities Throughout Its Security, Observability And IT Service Intelligence Software
by nlqip
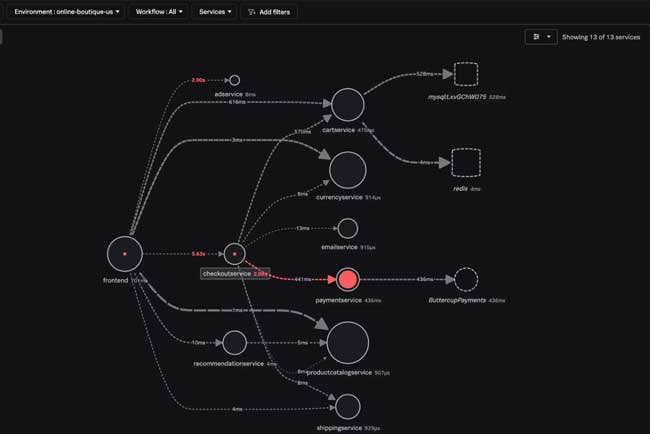
While Splunk-Cisco product integration was big news at this week’s .conf24 event, Splunk also debuted new products around AI, next-generation Security Operations Centers and data management. Splunk has unveiled a series of AI tools and assistants across its product portfolio that the company said are designed to help organizations speed up routine tasks, glean new…
Read MoreExperts agree that organisations need to conduct thorough audits and risk assessments. The best defences involve tight configuration management, software bill-of-materials tracking, security awareness training, and limiting what can be installed. “Understanding your attack surface and conducting regular external asset mapping exercises is critical,” Tim West, Director, Threat Intelligence at With Secure. “It is important…
Read MoreRecent Posts
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist
- Here Are The Stellar Startup Edge Computing/IoT Vendors To Know In 2024
- Five Companies That Came To Win This Week
- Microsoft pulls Exchange security updates over mail delivery issues
- Palo Alto Networks warns of critical RCE zero-day exploited in attacks