A new phishing kit has been released that allows red teamers and cybercriminals to create progressive web Apps (PWAs) that display convincing corporate login forms to steal credentials. A PWA is a web-based app created using HTML, CSS, and JavaScript that can be installed from a website like a regular desktop application. Once installed, the…
Read MoreThe report scores the world’s top 10 AI foundation models for language, including Google Gemini, Anthropic Claude, Amazon Bedrock, IBM Granite and OpenAI GPT-4. Forrester has reviewed, scored and ranked the world’s top AI foundation models for language—from Amazon Bedrock and Google Gemini to OpenAI GPT-4 and Anthropic Claude. AI startups like Cohere and Mistral…
Read MoreImage: Midjourney Today, the Cybersecurity and Infrastructure Security Agency (CISA) warned that criminals are impersonating its employees in phone calls and attempting to deceive potential victims into transferring money. This is part of a broader trend in which fraudsters are trying to legitimize their scams by using government employees’s titles and names. “The Cybersecurity and…
Read MoreSafety and location services company Life360 says it was the target of an extortion attempt after a threat actor breached and stole sensitive information from a Tile customer support platform. Life360 provides real-time location tracking, crash detection, and emergency roadside assistance services to more than 66 million members worldwide. In December 2021, it acquired Bluetooth…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. Maintaining an active social media presence can be a great way to improve brand visibility and generate leads, but it also opens the…
Read MoreCISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog…
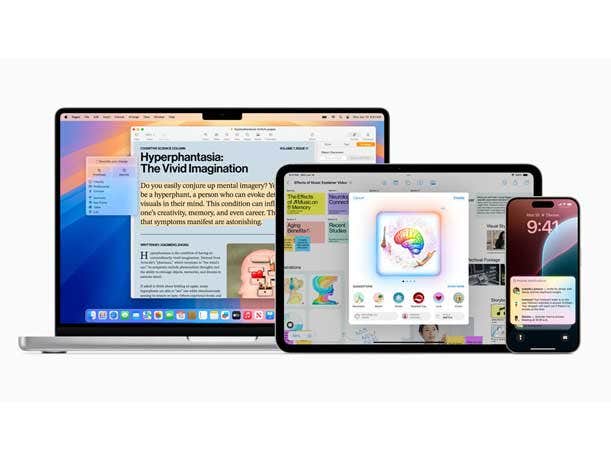
Read MoreApple’s much-anticipated upcoming suite of AI features for select iPhones, Macs and iPads is called Apple Intelligence, and it will include an enhanced Siri experience, systemwide Writing Tools, message and notification prioritization, call transcription and summarization, and ChatGPT integration. Apple Monday revealed Apple Intelligence, its much-anticipated suite of AI features that will enhance Siri’s natural…
Read MoreImpersonation scams are on the rise and often use the names and titles of government employees. The Cybersecurity and Infrastructure Security Agency (CISA) is aware of recent impersonation scammers claiming to represent the agency. As a reminder, CISA staff will never contact you with a request to wire money, cash, cryptocurrency, or use gift cards…
Read MoreThe multi-cloud networking upstart is partnering with the “de facto” security leader Palo Alto Networks. The new relationship will give enterprises new approach to securing applications and workloads across multi-cloud environments, Prosimo execs told CRN. Multi-cloud networking upstart Prosimo is joining forces with security specialist Palo Alto Networks to further secure application access at a…
Read MoreAs Oracle Inks Partnerships With OpenAI, Google Cloud, CTO Ellison Says ‘We Should Be Interconnected To Everybody’
by nlqip
‘That’s what we’re attempting to do within our multi-cloud strategy. I think that’s what customers want. So I’m optimistic that’s the way the world will settle out. We’ll get rid of these fees for moving data from cloud to cloud,’ says Oracle Chairman and CTO Larry Ellison on the company’s earnings call. Just prior to…
Read More