10up–ElasticPress Cross-Site Request Forgery (CSRF) vulnerability in 10up ElasticPress.This issue affects ElasticPress: from n/a through 5.1.0. 2024-06-08 4.3 CVE-2024-35684audit@patchstack.com 10up–Restricted Site Access Authentication Bypass by Spoofing vulnerability in 10up Restricted Site Access allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Restricted Site Access: from n/a through 7.4.1. 2024-06-04 5.3 CVE-2023-48753audit@patchstack.com 10Web Form Builder…
Read MoreTerms of the acquisition deal for Lacework, which had once been valued at $8.3 billion, weren’t disclosed. Fortinet announced Monday it has reached an agreement to acquire cloud security firm Lacework in a significant consolidation deal for the cybersecurity industry. The terms of the deal, which is expected to be completed in the second half…
Read MorePrivacy authorities in Canada and the United Kingdom have launched a joint investigation to assess the scope of sensitive customer information exposed in last year’s 23andMe data breach. The Privacy Commissioner of Canada and The Information Commissioner’s Office (ICO) will also look into whether the company had adequate safeguards to secure customer data stored on…
Read MoreThe company has become one of the few pure-play cybersecurity vendors to join the benchmark index. CrowdStrike shares surged Monday after the cybersecurity giant was added to the S&P 500 index. As of this writing Monday morning, CrowdStrike’s stock price was up 8 percent to $376.96 a share. [Related: Analysis: CrowdStrike Strikes Back In Platform,…
Read MoreGoogle has revealed that it took down 1,320 YouTube channels and 1,177 Blogger blogs as part of a coordinated influence operation connected to the People’s Republic of China (PRC). “The coordinated inauthentic network uploaded content in Chinese and English about China and U.S. foreign affairs,” Google Threat Analysis Group (TAG) researcher Billy Leonard said in…
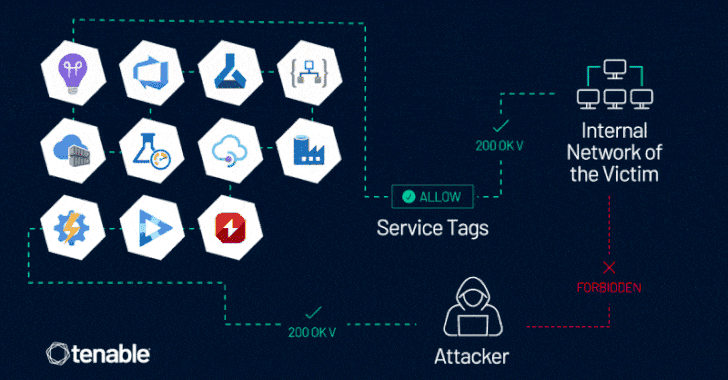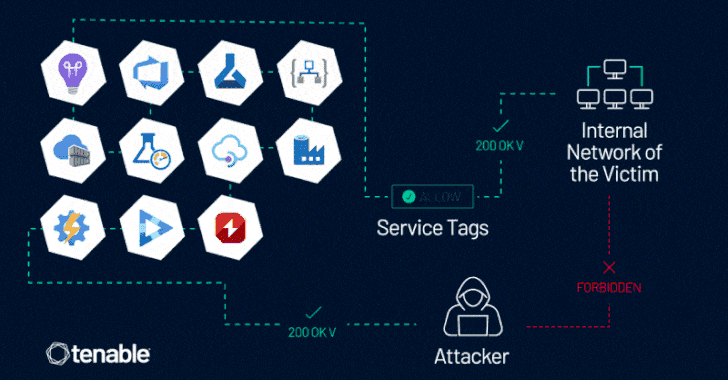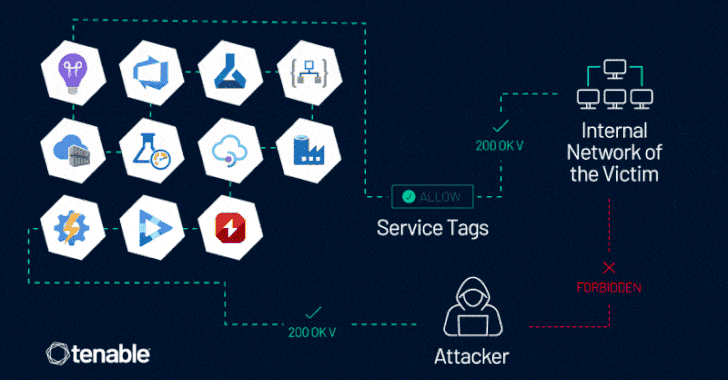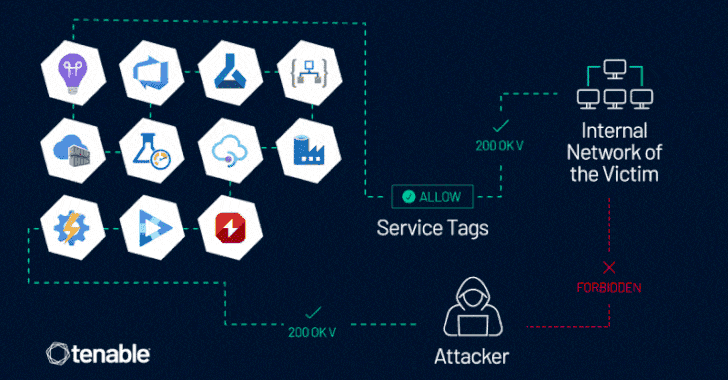
Read MoreJun 10, 2024NewsroomCloud Security / Vulnerability Microsoft is warning about the potential abuse of Azure Service Tags by malicious actors to forge requests from a trusted service and get around firewall rules, thereby allowing them to gain unauthorized access to cloud resources. “This case does highlight an inherent risk in using service tags as a…
Read MoreStaying Sharp: Cybersecurity CPEs Explained Perhaps even more so than in other professional domains, cybersecurity professionals constantly face new threats. To ensure you stay on top of your game, many certification programs require earning Continuing Professional Education (CPE) credits. CPEs are essentially units of measurement used to quantify the time and effort professionals spend on…
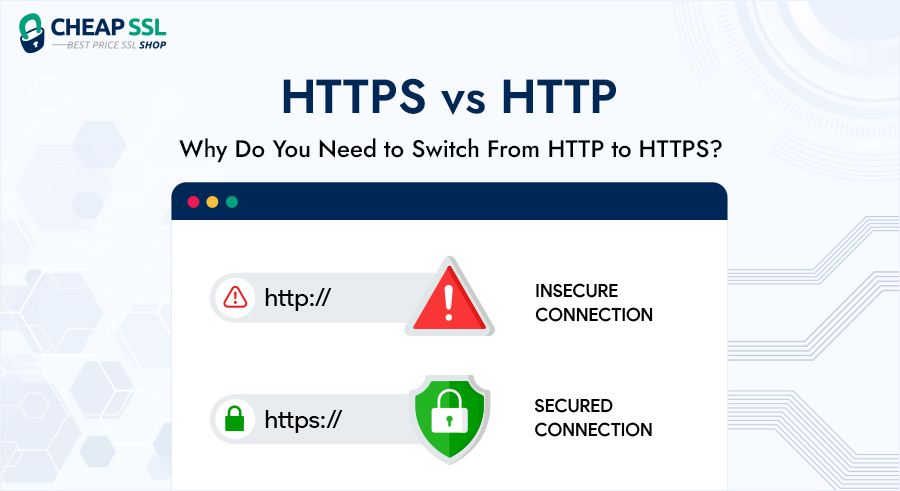
Read MoreHTTPS vs HTTP: Know the difference between secure and non-secure web protocols At a glance, HTTP and HTTPs may seem similar but they are different. HTTP transmits data in plain text, whereas HTTPS utilizes TLS/SSL encryption to secure communication. Let’s crack the code on HTTP vs HTTPS in this article. You will discover the stark…
Read MoreExploiting Mistyped URLs Interesting research: “Hyperlink Hijacking: Exploiting Erroneous URL Links to Phantom Domains“: Abstract: Web users often follow hyperlinks hastily, expecting them to be correctly programmed. However, it is possible those links contain typos or other mistakes. By discovering active but erroneous hyperlinks, a malicious actor can spoof a website or service, impersonating the…
Read MoreWhat is Operational Technology? Operational Technology (OT) is the backbone of our modern world as we know it today. Think about the daily operations of a factory, the precise control of our power grids, and even the supply of clean water to our homes. All of these modern capabilities are made possible and efficient due…
Read MoreRecent Posts
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist