The advisory recommends that Snowflake customers perform hunting activities for malicious activity in their systems. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning about the recent threat actor campaign targeting users of Snowflake and urging customers to proactively look for malicious activity. In the advisory, CISA pointed to a post from Snowflake on…
Read MoreMicrosoft has officially deprecated NTLM authentication on Windows and Windows servers, stating that developers should transition to Kerberos or Negotiation authentication to prevent problems in the future. New Technology LAN Manager, better known as NTLM, is an authentication protocol first released in 1993 as part of Windows NT 3.1 and as the successor to the LAN…
Read More‘[AI is] changing the way businesses communicate with each other. It’s changing the way they leverage technology. And at Cisco, we believe we have a very significant role to play here in really being the trusted partner to help our customers navigate this new era of AI,’ says Mark Patterson, Cisco’s executive vice president and…
Read MoreGrowing up in the shadow of child identity theft can be a struggle. For Axton Betz-Hamilton, her discovery of the culprit led to the shock of a lifetime. In the second installment of this two-part episode, we examine the massive financial and emotional toll of finding out a loved one wasn’t all that they seemed,…
Read MoreJun 04, 2024NewsroomServer Security / Vulnerability Progress Software has rolled out updates to address a critical security flaw impacting the Telerik Report Server that could be potentially exploited by a remote attacker to bypass authentication and create rogue administrator users. The issue, tracked as CVE-2024-4358, carries a CVSS score of 9.8 out of a maximum…
Read MoreHere are the five biggest new integrated product launches from SAP and Google Cloud unveiled at SAP Sapphire 2024 Tuesday that all partners and customers need to know about. SAP and Google Cloud launched a slew of new innovations together at SAP Sapphire 2024 Tuesday in Orlando, Fla., including a new AI-powered offering to enable…
Read MoreBy ARC Labs contributor, Shannon Mong ARC Labs recently analyzed a sample of the Wineloader backdoor for infection chain analysis and detection opportunities to help defenders protect their organizations. Through this analysis, ARC Labs is providing defenders with general detection guidance and specific KQL queries to detect Wineloader activity within Microsoft Sentinel. Additionally, ARC Labs has provided…
Read MoreCISA released four Industrial Control Systems (ICS) advisories on June 4, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. CISA encourages users and administrators to review the newly released ICS advisories for technical details and mitigations. Source link lol
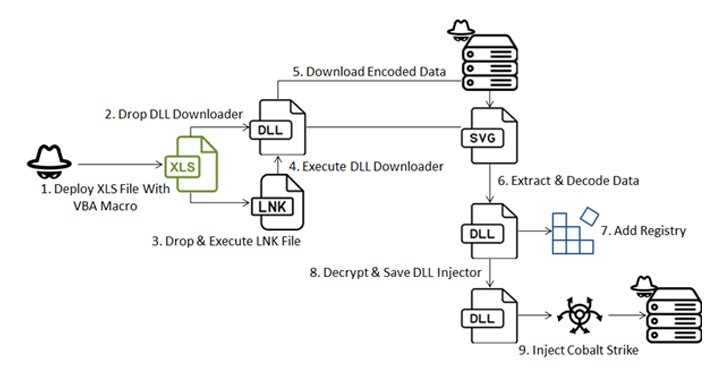
Read MoreJun 04, 2024NewsroomCyber Attack / Malware A new sophisticated cyber attack has been observed targeting endpoints geolocated to Ukraine with an aim to deploy Cobalt Strike and seize control of the compromised hosts. The attack chain, per Fortinet FortiGuard Labs, involves a Microsoft Excel file that carries an embedded VBA macro to initiate the infection,…
Read MoreJun 04, 2024The Hacker NewsBrowser Security / Enterprise Security The landscape of browser security has undergone significant changes over the past decade. While Browser Isolation was once considered the gold standard for protecting against browser exploits and malware downloads, it has become increasingly inadequate and insecure in today’s SaaS-centric world. The limitations of Browser Isolation,…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’