The BBC has disclosed a data security incident that occurred on May 21, involving unauthorized access to files hosted on a cloud-based service, compromising the personal information of BBC Pension Scheme members. As per the reports, the incident impacted roughly 25,000 people, including current and former employees of Britain’s national public service broadcaster. The compromised…
Read More‘AI inevitably calls customers’ attention to the fragmented state of their data caused by their disparate data storage infrastructure. Data stored on widely diverse platforms, with different operating and management systems, which are siloed and individually managed, are unable to feed real-time data to AI inference engines. The Pure Storage platform strategy provides a unified…
Read MoreAnother 38% of apps inside government organizations have vulnerabilities that are not yet one-year old but can become security debt if left unfixed and only 3% are completely free of known flaws, compared to 6% across other sectors. “So, while (slightly) fewer public sector organizations have security debt, they tend to accumulate more of it,”…
Read MoreCheyenne, WY – May 30th, 2024 – BlackFog, the leader in ransomware protection and anti data exfiltration today announced it has been named a winner in the prestigious 2024 Fortress Cybersecurity Awards presented by the Business Intelligence Group. BlackFog received the Fortress Data Protection award for its pioneering anti data exfiltration (ADX) technology. By utilizing AI based algorithms,…
Read MoreSecurity leaders are in a tricky position trying to discern how much new AI-driven cybersecurity tools could actually benefit a security operations center (SOC). The hype about generative AI is still everywhere, but security teams have to live in reality. They face constantly incoming alerts from endpoint security platforms, SIEM tools, and phishing emails reported…
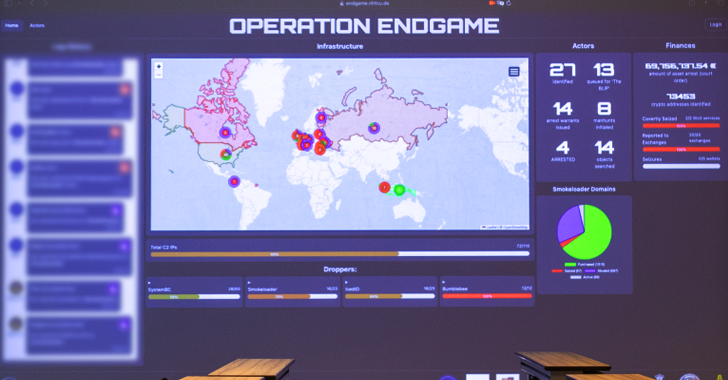
Read MoreMay 30, 2024NewsroomMalware / Cyber Crime Europol on Thursday said it shut down the infrastructure associated with several malware loader operations such as IcedID, SystemBC, PikaBot, SmokeLoader, Bumblebee, and TrickBot as part of a coordinated law enforcement effort codenamed Operation Endgame. “The actions focused on disrupting criminal services through arresting High Value Targets, taking down…
Read MoreSupply Chain Attack against Courtroom Software No word on how this backdoor was installed: A software maker serving more than 10,000 courtrooms throughout the world hosted an application update containing a hidden backdoor that maintained persistent communication with a malicious website, researchers reported Thursday, in the latest episode of a supply-chain attack. The software, known…
Read MoreA macOS version of the LightSpy surveillance framework has been discovered, confirming the extensive reach of a tool only previously known for targeting Android and iOS devices. LightSpy is a modular iOS and Android surveillance framework used to steal a wide variety of data from people’s mobile devices, including files, screenshots, location data (including building floor…
Read MoreWang allegedly managed approximately 150 dedicated servers worldwide, 76 of which he had leased from US-based service providers. “Using the dedicated servers, Wang deployed and managed applications, commanded and controlled the infected devices, operated his 911 S5 service, and provided paying customers with access to proxied IP addresses associated with the infected devices,” the Justice…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. In today’s digital world, businesses face the challenge of managing ever-expanding volumes of data efficiently and securely. Traditional on-premise storage solutions often come…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’