The company has already shifted to a ‘partner-first’ model and is now launching a three-tier program for solution and service providers, Silverfort Channel Chief Leslie Bois tells CRN. Silverfort announced its first formal channel program Wednesday as the identity security firm looks to work with partners to protect against the rising threat of identity-based attacks,…
Read MoreThe company says the addition of the MSSP-focused Pillr platform ‘accelerates OpenText’s cybersecurity product road map.’ OpenText said Wednesday it has acquired the Pillr managed detection and response (MDR) platform from cybersecurity services powerhouse Novacoast. The terms of the deal were not disclosed. The acquisition deal will see some employees joining OpenText along with the…
Read More23-year-old alleged founder of dark web Incognito Market arrested after FBI tracks cryptocurrency payments
by nlqip
The United States Department of Justice has dealt a blow to dark web drug traffickers by arresting a man alleged to operate the dark web drugs marketplace Incognito Market. According to a DOJ press release, the alleged operator of a darknet platform sold over $100 million worth of narcotics worldwide. 23-year-old Rui-Siang Lin (also known…
Read MoreA previously unknown threat actor dubbed “Unfading Sea Haze” has been targeting military and government entities in the South China Sea region since 2018, remaining undetected all this time. Bitdefender researchers who discovered the threat group report that its operations align with Chinese geo-political interests, focusing on intelligence collection and espionage. As is typical for…
Read MoreMay 22, 2024NewsroomICS Security / Vulnerability Rockwell Automation is urging its customers to disconnect all industrial control systems (ICSs) not meant to be connected to the public-facing internet to mitigate unauthorized or malicious cyber activity. The company said it’s issuing the advisory due to “heightened geopolitical tensions and adversarial cyber activity globally.” To that end,…
Read MoreUnredacting Pixelated Text Experiments in unredacting text that has been pixelated. Tags: redaction, steganography Posted on May 22, 2024 at 7:03 AM • 0 Comments Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreSince the first edition of The Ultimate SaaS Security Posture Management (SSPM) Checklist was released three years ago, the corporate SaaS sprawl has been growing at a double-digit pace. In large enterprises, the number of SaaS applications in use today is in the hundreds, spread across departmental stacks, complicating the job of security teams to…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. As the world becomes increasingly digital, our online lives have become an extension of our physical selves. We share our thoughts and experiences…
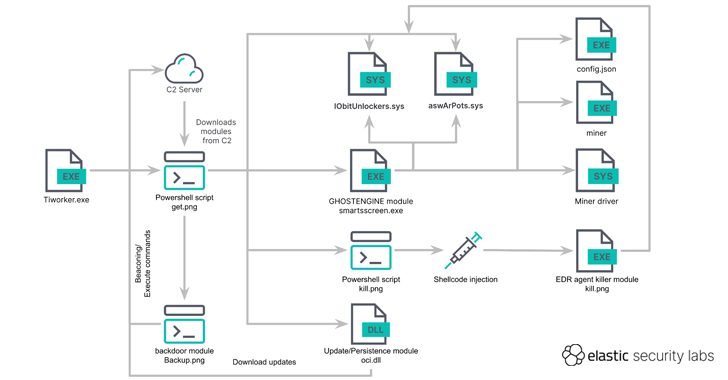
Read MoreCybersecurity researchers have discovered a new cryptojacking campaign that employs vulnerable drivers to disable known security solutions (EDRs) and thwart detection in what’s called a Bring Your Own Vulnerable Driver (BYOVD) attack. Elastic Security Labs is tracking the campaign under the name REF4578 and the primary payload as GHOSTENGINE. Previous research from Chinese cybersecurity firm…
Read MoreMay 22, 2024NewsroomVulnerability / Data Breach An unknown threat actor is exploiting known security flaws in Microsoft Exchange Server to deploy a keylogger malware in attacks targeting entities in Africa and the Middle East. Russian cybersecurity firm Positive Technologies said it identified over 30 victims spanning government agencies, banks, IT companies, and educational institutions. The…
Read MoreRecent Posts
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist