The acquisition is the largest in CyberArk’s history, according to an analyst. CyberArk announced a deal Monday to acquire machine identity specialist Venafi from private equity firm Thoma Bravo for $1.54 billion. The acquisition is the largest in the 25-year history of identity security and access management firm CyberArk, according to Shaul Eyal, managing director…
Read MoreDell Technologies At 40, ‘A Damn Fine Puzzle’: Five Questions With Its First President Lee Walker
by nlqip
‘We were up against IBM, up against Compaq. The competition was immense in size. They were sophisticated and they had tremendous resources,’ Lee Walker told CRN. “We had two board of directors. Michael and me.” The most powerful computers in the world, running the most demanding applications, for governments and enterprises are designed by the…
Read MoreMichael Dell: ‘Blizzard Of New’ AI Announcements Coming To Dell Technology World 2024 Amid Record Partner Sign-Ups
by nlqip
‘Never been a better time to be a Dell channel partner. We are fully committed to our channel as we have been. The record sign-ups that we have seen for Dell Tech World certainly indicate the continuing interest and passion from our channel partners and we’ll have a lot to say about how we can…
Read MoreAs part of Printer Week 2024, CRN takes a look at some of the latest multi-function printers that address a variety of business needs, whether they’re priced and sized for small teams, designed to reduce power consumption or crank out larger numbers of pages every month. As businesses settle into their new normal of where…
Read MoreLinguistic Lumberjack: Attacking Cloud Services via Logging Endpoints (Fluent Bit – CVE-2024-4323)
by nlqip
Tenable Research has discovered a critical memory corruption vulnerability dubbed Linguistic Lumberjack in Fluent Bit, a core component in the monitoring infrastructure of many cloud services. Key takeaways Fluent Bit is a logging utility heavily used by all major cloud providers. Tenable Research discovered a critical vulnerability dubbed Linguistic Lumberjack (CVE-2024-4323) within Fluent Bit’s built-in…
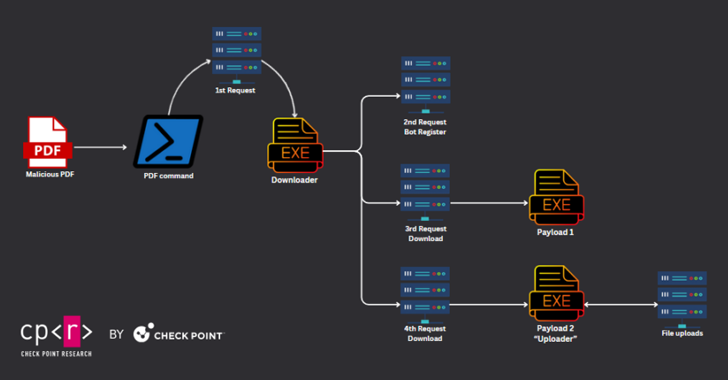
Read MoreMultiple threat actors are weaponizing a design flaw in Foxit PDF Reader to deliver a variety of malware such as Agent Tesla, AsyncRAT, DCRat, NanoCore RAT, NjRAT, Pony, Remcos RAT, and XWorm. “This exploit triggers security warnings that could deceive unsuspecting users into executing harmful commands,” Check Point said in a technical report. “This exploit…
Read MoreMay 20, 2024The Hacker NewsSoftware Security / Vulnerability All developers want to create secure and dependable software. They should feel proud to release their code with the full confidence they did not introduce any weaknesses or anti-patterns into their applications. Unfortunately, developers are not writing their own code for the most part these days. 96%…
Read MoreIBM Sells Cybersecurity Group IBM is selling its QRadar product suite to Palo Alto Networks, for an undisclosed—but probably surprisingly small—sum. I have a personal connection to this. In 2016, IBM bought Resilient Systems, the startup I was a part of. It became part if IBM’s cybersecurity offerings, mostly and weirdly subservient to QRadar. That…
Read MoreMay 20, 2024NewsroomMalvertising / Cryptocurrency A “multi-faceted campaign” has been observed abusing legitimate services like GitHub and FileZilla to deliver an array of stealer malware and banking trojans such as Atomic (aka AMOS), Vidar, Lumma (aka LummaC2), and Octo by impersonating credible software like 1Password, Bartender 5, and Pixelmator Pro. “The presence of multiple malware…
Read MorePhishing is one of the most common forms of cyber attack that organizations face nowadays. A 2024 risk report states that 94% of organizations fall victim to phishing attacks, and 96% are negatively impacted by them. However, phishing attacks are not only growing in number but are also more sophisticated and successful. This is owing…
Read MoreRecent Posts
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks