May 16, 2024NewsroomBrowser Security / Vulnerability Google has rolled out fixes to address a set of nine security issues in its Chrome browser, including a new zero-day that has been exploited in the wild. Assigned the CVE identifier CVE-2024-4947, the vulnerability relates to a type confusion bug in the V8 JavaScript and WebAssembly engine. It…
Read MoreMay 16, 2024NewsroomRansomware / Incident Response The Microsoft Threat Intelligence team said it has observed a threat it tracks under the name Storm-1811 abusing the client management tool Quick Assist to target users in social engineering attacks. “Storm-1811 is a financially motivated cybercriminal group known to deploy Black Basta ransomware,” the company said in a…
Read MoreThe companies say they will ‘facilitate the migration’ of QRadar SaaS customers to Palo Alto Networks’ Cortex XSIAM platform once the deal closes. Palo Alto Networks said Wednesday that it has reached a deal to acquire IBM’s QRadar software-as-a-service assets, as part of the cybersecurity giant’s drive to bring more customers onto its Cortex XSIAM…
Read More“We will deliver innovation at an unprecedented pace and scale to organizations around the globe,” Cisco CEO Chuck Robbins said on Wednesday’s earnings call. Cisco Systems CEO Chuck Robbins plans to leverage “Cisco’s robust partner and customer ecosystem in markets where Splunk had limited or no presence” to grow the business of his new security…
Read MoreWith the Series E financing round the company achieves “unicorn” status with a $1.6 billion valuation as data-intensive AI and generative AI applications boost demand for the company’s software. Data management platform developer WekaIO has raised $140 million in an oversubscribed Series E round of funding that boosts the company’s valuation to $1.6 billion, the…
Read MoreApply appropriate updates provided by Google to vulnerable systems immediately after appropriate testing. (M1051: Update Software) Safeguard 7.1: Establish and Maintain a Vulnerability Management Process: Establish and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this Safeguard. Safeguard 7.4: Perform…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-057 DATE(S) ISSUED: 05/15/2024 OVERVIEW: A vulnerability has been discovered in SolarWinds Access Rights Manager that could allow for privilege escalation. Successful exploitation of this vulnerability could allow for privilege escalation in the context of the affected service account. Depending on the privileges associated with the service account, an attacker could then…
Read MoreIn addition to QakBot, the Kaspersky researchers have seen other payloads deployed with the exploit for the new CVE-2024-30051 vulnerability, including the Cobalt Strike beacon. As a result, Kaspersky has concluded that the exploit is currently known and being used by multiple groups. It’s worth noting that CVE-2024-30051 cannot be used to gain initial access.…
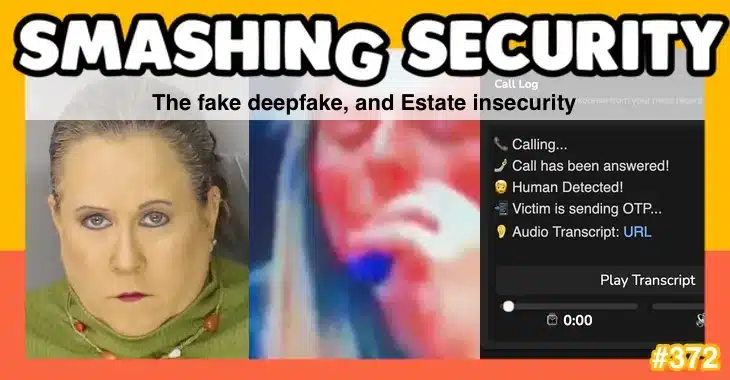
Read MoreRemember when a US mother was accused of distributing explicit deepfake photos and videos to try to get her teenage daughter’s cheerleading rivals kicked off the team? Well, there has been a surprising development. And learn how cybercriminals have been stealing boomers’ one-time-passcodes via a secretive online service. All this and more is discussed in…
Read MoreGoogle has released a new emergency Chrome security update to address the third zero-day vulnerability exploited in attacks within a week. “Google is aware that an exploit for CVE-2024-4947 exists in the wild,” the search giant said in a security advisory published on Wednesday. The company fixed the zero-day flaw with the release of 125.0.6422.60/.61…
Read MoreRecent Posts
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption