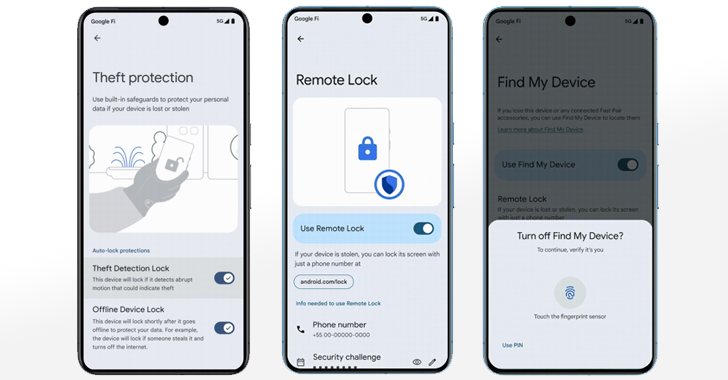
May 15, 2024NewsroomPrivacy / Data Protection Google has announced a slew of privacy and security features in Android, including a suite of advanced protection features to help secure users’ devices and data in the event of a theft. These features aim to help protect data before, during and after a theft attempt, the tech giant…
Read MoreMay 15, 2024NewsroomAndroid Security / Malware Google is unveiling a set of new features in Android 15 to prevent malicious apps installed on the device from capturing sensitive data. This constitutes an update to the Play Integrity API that third-party app developers can take advantage of to secure their applications against malware. “Developers can check…
Read MoreApple’s antifraud technology has blocked more than $7 billion in potentially fraudulent transactions in four years, the company states in its latest annual fraud prevention analysis. From 2020 through 2023, the company also detected more than 14 million stolen cards and blocked them from transacting on its platform along with 3.3 million accounts. Statistics for last…
Read MoreThe deal to bring together two players in the SIEM (security information and event management) space follows big moves in the market including Cisco’s $28 billion acquisition of Splunk. LogRhythm and Exabeam announced Wednesday that the two companies have reached an agreement to merge in a significant consolidation deal for the cybersecurity industry. The terms…
Read MoreFinancially motivated cybercriminals abuse the Windows Quick Assist feature in social engineering attacks to deploy Black Basta ransomware payloads on victims’ networks. Microsoft has been investigating this campaign since at least mid-April 2024, and, as they observed, the threat group (tracked as Storm-1811) started their attacks by email bombing the target after subscribing their addresses…
Read MoreIn an interview with CRN, Klarich says the company’s debut of new AI-powered products shows how Palo Alto Networks is combining GenAI with machine learning to make security more predictive and real time — compared to other offerings that are ‘too simplistic.’ The much-awaited debut by Palo Alto Networks of a new suite of AI-powered…
Read MoreA distribution executive weighs in on the potential impacts of President Joe Biden’s upcoming tariff increases for Chinese semiconductors and lithium-ion batteries on channel partners: ‘There could be enough of those things inside of something to raise the price enough to be painful.’ President Joe Biden’s administration announced on Tuesday that he will raise tariffs…
Read MoreThe FBI has seized the notorious BreachForums hacking forum used to leak and sell stolen corporate data to other cybercriminals. The seizure occurred on Wednesday morning, soon after the site was used last week to leak data stolen from a Europol law enforcement portal. The website is now displaying a message stating that the website and its backend…
Read MoreOn December 18, 2023, SRHS confirmed the breach compromised data of 252890 patients, all of whom were notified through mails on January 12, 2023. Similar notifications were sent on May 13, 2024, this time to the 25 Maine patients, confirming the new estimate. “Through the investigation, Singing River identified unauthorized access within its environment between August 16 and August 18,…
Read MoreSplunk, security and AI are likely to come up during Cisco’s latest quarterly earnings report. How Cisco Systems can benefit from the artificial intelligence explosion. Splunk integration. And overcoming hurdles in networking. These are among the likely subjects to come up when the San Jose, Calif.-based vendor reports its third fiscal quarter earnings Wednesday. The…
Read MoreRecent Posts
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption