More than 60,000 D-Link network-attached storage devices that have reached end-of-life are vulnerable to a command injection vulnerability with a publicly available exploit. The flaw, tracked as CVE-2024-10914, has a critical 9.2 severity score and is present in the ‘cgi_user_add’ command where the name parameter is insufficiently sanitized. An unauthenticated attacker could exploit it to inject…
Read MoreFor the week ending Nov. 8, CRN takes a look at the companies that brought their ‘A’ game to the channel including Ingram Micro, CrowdStrike, Accenture, Cynomi and Nerdio. The Week Ending Nov. 8 Topping this week’s Came to Win list is distributor Ingram Micro for its latest steps to help solution providers work with…
Read MoreToday, cybersecurity company Palo Alto Networks warned customers to restrict access to their next-generation firewalls because of a potential remote code execution vulnerability in the PAN-OS management interface. In a security advisory published on Friday, the company said it doesn’t yet have additional information regarding this alleged security flaw and added that it has yet to…
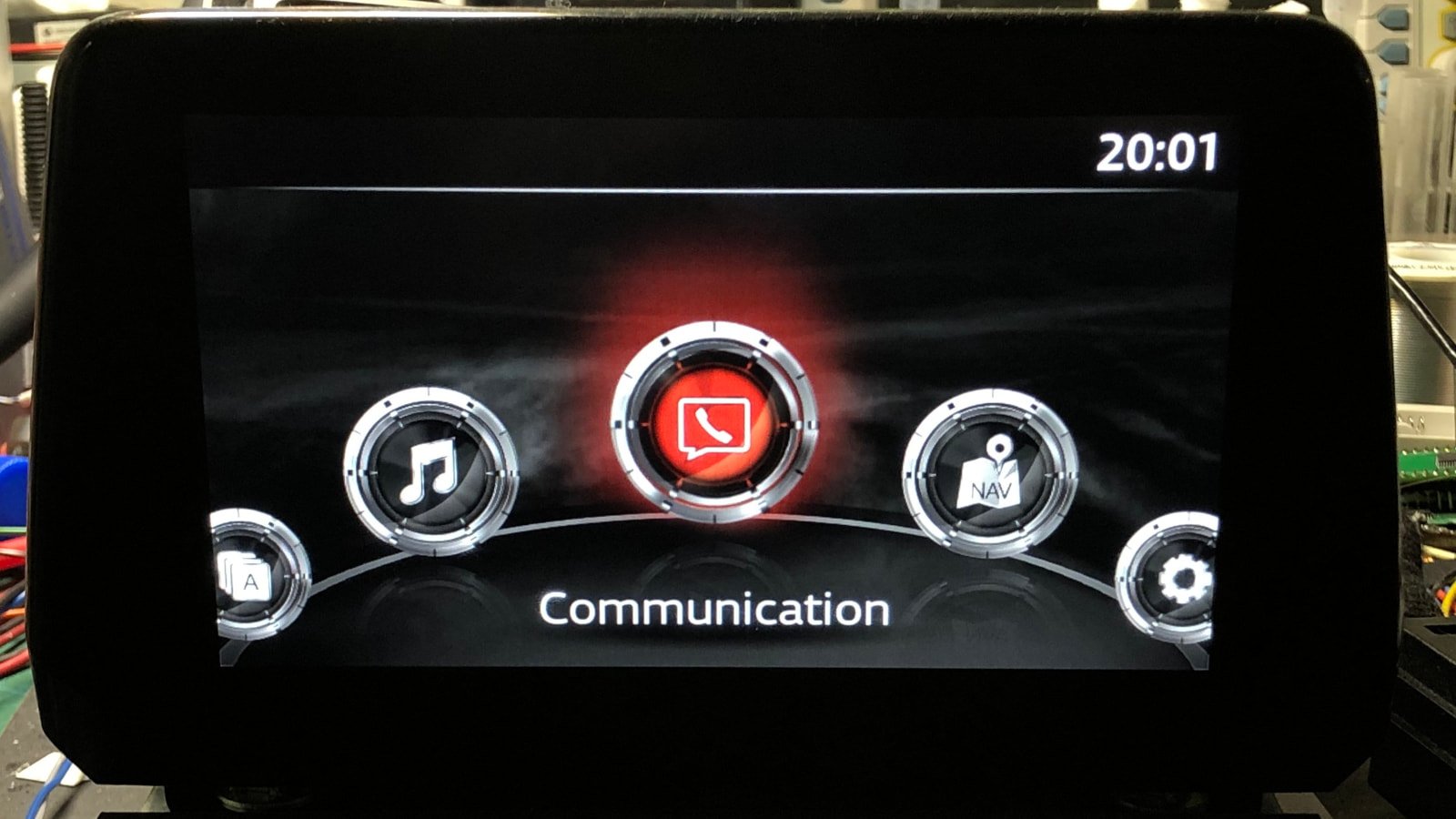
Read MoreAttackers could exploit several vulnerabilities in the Mazda Connect infotainment unit, present in multiple car models including Mazda 3 (2014-2021), to execute arbitrary code with root permission. The security issues remain unpatched and some of them are command injection flaws that could be leveraged to obtain unrestricted access to vehicle networks, potentially impacting the car’s…
Read MoreWith global spending on the technology industry expected to reach $5.74 trillion in 2025, CRN breaks down the five largest markets that will reap the most revenue next year, according to new data from Gartner. Worldwide spending on IT will hit a record $5.74 trillion in 2025 with all areas of technology—from software to communications…
Read More‘We’ve been talking about Asio for numerous years. We’ve been showing you glimpses of Asio. I’m here to tell you that we are at that tipping point. I’m here to tell you that it is ready for prime time,’ ConnectWise CEO Manny Rivelo told IT Nation 2024 ConnectWise CEO Manny Rivelo said the long-promised Asio…
Read MoreCybersecurity Snapshot: CISA Warns of Global Spear-Phishing Threat, While OWASP Releases AI Security Resources
by nlqip
CISA is warning about a spear-phishing campaign that spreads malicious RDP files. Plus, OWASP is offering guidance about deepfakes and AI security. Meanwhile, cybercriminals have amplified their use of malware for fake software-update attacks. And get the latest on CISA’s international plan, Interpol’s cyber crackdown and ransomware trends. Dive into six things that are top…
Read MoreGoogle has left Android users puzzled after the most recent update to the Google mobile app causes links shared from the app to now be prepended with a mysterious “search.app” domain. As the Google app is a popular portal for searching the web for Android users and delivers a personalized content news feed referred to…
Read MoreThe results from Q3 are ‘further validating our view that the firewall market is recovering,’ Fortinet CFO Keith Jensen said Thursday. Fortinet is once again seeing growth from its firewall business after several quarters of decline in the cybersecurity vendor’s largest segment, executives said Thursday. While specifics on the firewall growth were not disclosed, during…
Read MoreBy leading the expanded and rebranded HP Solutions group, former Poly CEO Dave Shull is set to play a bigger role in the PC and print giant’s growth strategy, which includes its growing portfolios of AI development solutions and videoconferencing products. A reorganization at HP Inc. has given the leader of its software and services…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm