CISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-20767 Adobe ColdFusion Improper Access Control Vulnerability CVE-2024-35250 Microsoft Windows Kernel-Mode Driver Untrusted Pointer Dereference Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive…
Read MoreToday, CISA—through the Joint Cyber Defense Collaborative and in coordination with the Office of the National Cyber Director (ONCD)—released the National Cyber Incident Response Plan Update Public Comment Draft. The draft requests public comment on the National Cyber Incident Response Plan (NCIRP)—public comment period begins today and concludes on January 15, 2025. Since initial publication…
Read More‘We expect this to represent an AI revenue, serviceable addressable market, or SAM, for XPUs and network in a range of $60 [billion] to $90 billion in fiscal 2027 alone. We are very well positioned to achieve a leading market share in this opportunity and expect this will drive a strong ramp from our 2024,”…
Read More403 Forbidden WHAT? Why am I seeing this? Your access to this site was blocked by Wordfence, a security provider, who protects sites from malicious activity. If you believe Wordfence should be allowing you access to this site, please let them know using the steps below so they can investigate why this is happening. Reporting…
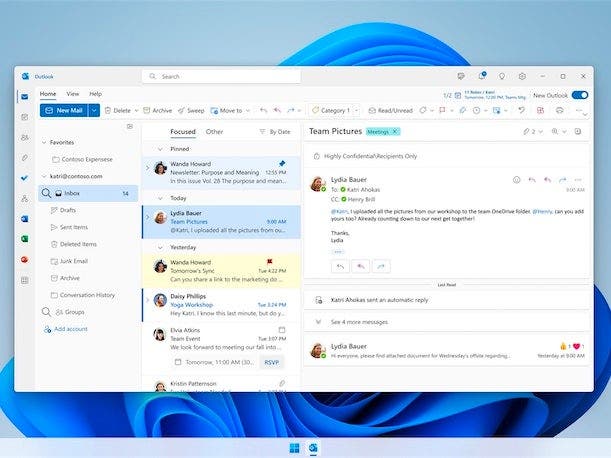
Read More‘Our goal with this change is to give users an opportunity to try new Outlook as millions of users already have,’ Microsoft says in a message to IT administrators reviewed by CRN. Microsoft solution providers tell CRN they are ready for the tech giant’s upcoming dates for automatically switching Outlook users to the new version…
Read MoreQualcomm provided the statement in response to a claim made by interim Intel co-CEO Michelle Johnston Holthaus on Thursday that many retailers are seeing a large percentage of Arm PCs being returned due to software compatibility issues. Qualcomm said return rates for PCs powered by its Arm-based Snapdragon X processors are “within industry norm” after…
Read MoreIn their first public appearance together, interim Intel co-CEOs David Zinsner and Michelle Johnston Holthaus give blunt assessments of the company’s accelerator chip and server CPU efforts while noting that more rivals are set to enter the PC market next year. Intel’s interim co-CEOs gave blunt assessments of the company’s accelerator chip and server CPU…
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-50623 Cleo Multiple Products Unrestricted File Upload Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known…
Read MoreCISA and EPA Release Joint Fact Sheet Detailing Risks Internet-Exposed HMIs Pose to WWS Sector | CISA
by nlqip
Today, CISA and the Environmental Protection Agency (EPA) released Internet-Exposed HMIs Pose Cybersecurity Risks to Water and Wastewater Systems. This joint fact sheet provides Water and Wastewater Systems (WWS) facilities with recommendations for limiting the exposure of Human Machine Interfaces (HMIs) and securing them against malicious cyber activity. HMIs enable operational technology owners and operators…
Read MoreCybersecurity Snapshot: Telecoms May Face Tougher Regulations After Salt Typhoon Hacks, as Study Finds Cyber Pros More Stressed at Work
by nlqip
The FCC wants stronger cyber regulations for telecoms after cyber espionage breaches. Meanwhile, find out why cyber pros say work has become more difficult. Plus, check out tips to prevent AI-boosted financial fraud. And get the latest on vulnerability management, EU cyber challenges and CIS predictions for 2025. Dive into six things that are top…
Read MoreRecent Posts
- The Most Scary, Interesting, and Important Stories of 2024
- Choosing the Right CNAPP: Six Considerations for Mid-Sized Enterprises
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Vulnerability Summary for the Week of December 23, 2024 | CISA
- Navigating the SEC’s Cybersecurity Disclosure Rules: One Year On