‘We want to take the fear of adopting AI because of data leakage and data governance, compliance, we want to take that out of the equation,’ Bradley Reynolds, SVP for artificial intelligence at Expedient, tells CRN. To stop the secret sauce from leaking, don’t bring the data to the GenAI model, bring the GenAI model…
Read MoreBitwarden has just launched a new multi-factor authenticator app called Bitwarden Authenticator, which is available for iOS and Android devices. The app uses time-based one-time passwords (TOTPs) for accounts registered by scanning a QR code to provide users with an extra layer of security during authentication. “By leveraging widely adopted standards such as TOTP, Bitwarden…
Read More‘We talk internally a lot about being a $300 billion market cap company by the 2040s, and we don’t think that’s far-fetched,’ said John Street, Pax8 founder and former CEO. ‘We really are in good shape, the star of this show is the total addressable market.’ Scott Chasin taking over the helm as Pax8’s newest…
Read MoreCISA and the FBI urged software companies today to review their products and eliminate path traversal security vulnerabilities before shipping. Attackers can exploit path traversal vulnerabilities (also known as directory traversal) to create or overwrite critical files used to execute code or bypass security mechanisms like authentication. Such security flaws can also let threat actors…
Read MoreA CEO of a number of tech companies has been sentenced in federal court for running what officials are calling “one of the largest counterfeit-trafficking operations ever.” Onur Aksoy was convicted of selling counterfeit Cisco equipment, with some of the phony gear being deployed in classified information systems, combat and non-combat operations of the U.S.…
Read MoreLaw enforcement shut down 12 phone fraud call centers in Albania, Bosnia and Herzegovina, Kosovo, and Lebanon, behind thousands of scam calls daily. Dozens of German law enforcement officers, aided by hundreds of counterparts from other countries (i.e., Albania, Bosnia and Herzegovina, Kosovo, and Lebanon), carried out numerous raids on April 18, identifying 39 suspects…
Read MoreU.S. and international cybersecurity and law enforcement agencies this week issued a joint fact sheet to highlight and safeguard against the continued malicious cyber activity conducted by pro-Russia hacktivists against operational technology (OT) devices in North America and Europe. Read on to get all the details and learn what actions to take today. Against the…
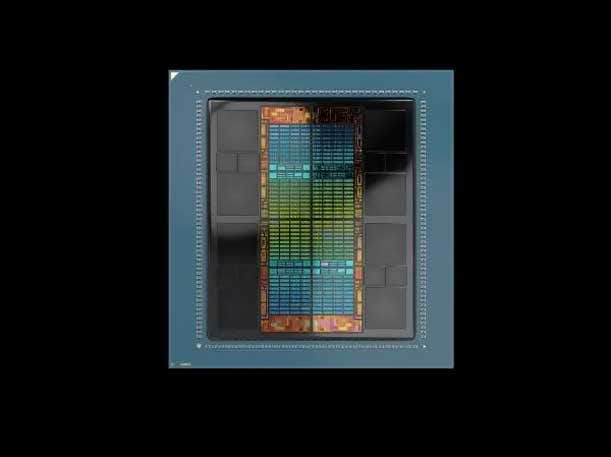
Read MoreCRN rounds up five cool AI and high-performance computing servers from Dell Technologies, Lenovo, Supermicro and Gigabyte that use AMD’s Instinct MI300 chips, which launched a few months ago to challenge Nvidia’s dominance in the AI computing space. AMD is making its biggest challenge yet to Nvidia’s dominance in the AI computing space with its…
Read MoreTony Safoian, CEO of Google Cloud all-star partner SADA, talks about winning new Google Workspace customers, Insight’s Microsoft practice and his bullish thoughts on Google’s AI strategy. After Insight Enterprises acquired Google Cloud superstar SADA for $410 million a few months ago, SADA CEO Tony Safoian said he is bullish about the new cloud customer…
Read MoreMicrosoft has highlighted a novel attack dubbed “Dirty Stream,” which could allow malicious Android apps to overwrite files in another application’s home directory, potentially leading to arbitrary code execution and secrets theft. The flaw arises from the improper use of Android’s content provider system, which manages access to structured data sets meant to be shared…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm