The UK Bans Default Passwords The UK is the first country to ban default passwords on IoT devices. On Monday, the United Kingdom became the first country in the world to ban default guessable usernames and passwords from these IoT devices. Unique passwords installed by default are still permitted. The Product Security and Telecommunications Infrastructure…
Read MoreA never-before-seen botnet called Goldoon has been observed targeting D-Link routers with a nearly decade-old critical security flaw with the goal of using the compromised devices for further attacks. The vulnerability in question is CVE-2015-2051 (CVSS score: 9.8), which affects D-Link DIR-645 routers and allows remote attackers to execute arbitrary commands by means of specially…
Read MoreMay 02, 2024NewsroomCyber Attack / Data Breach Cloud storage services provider Dropbox on Wednesday disclosed that Dropbox Sign (formerly HelloSign) was breached by unidentified threat actors, who accessed emails, usernames, and general account settings associated with all users of the digital signature product. The company, in a filing with the U.S. Securities and Exchange Commission…
Read MoreLike antivirus software, vulnerability scans rely on a database of known weaknesses. That’s why websites like VirusTotal exist, to give cyber practitioners a chance to see whether a malware sample is detected by multiple virus scanning engines, but this concept hasn’t existed in the vulnerability management space. The benefits of using multiple scanning engines Generally…
Read MoreCustomers express concerns Dropbox said it swung into action as soon as it discovered the breach and “launched an investigation with industry-leading forensic investigators to understand what happened and mitigate risks to our users.” Its investigation revealed that “a third party gained access to a Dropbox Sign automated system configuration tool.” “The actor compromised a…
Read MoreThe committee emphasized that MFA should be a fundamental expectation for an entity like Change Healthcare, given the vast amount of sensitive data it handles. Witty explained that Change Healthcare, which merged into UnitedHealth towards the end of 2022, utilized older technologies that the company had been updating since its acquisition. However, the timing proved…
Read MoreLegit Security software compliance attestation trust center Legit Security introduced a software compliance attestation trust center, which by using frameworks such as SLSA, PCI DSS, SOC2, and ISO 27001, helps teams quickly assess the state of a software security program to identify gaps that create risk. The trust center also supports new CISA requirements. It…
Read MoreMay 02, 2024NewsroomVulnerability / Data Breach The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical flaw impacting GitLab to its Known Exploited Vulnerabilities (KEV) catalog, owing to active exploitation in the wild. Tracked as CVE-2023-7028 (CVSS score: 10.0), the maximum severity vulnerability could facilitate account takeover by sending password reset emails to…
Read MorePrinciples and objectives driving the NSM The NSM cites eight core principles that drive the NSM. First among these is a sense of shared responsibility by government entities and the owners of critical to come together in a “national unity of effort.” Related to this united effort is the principle that government regulatory and oversight…
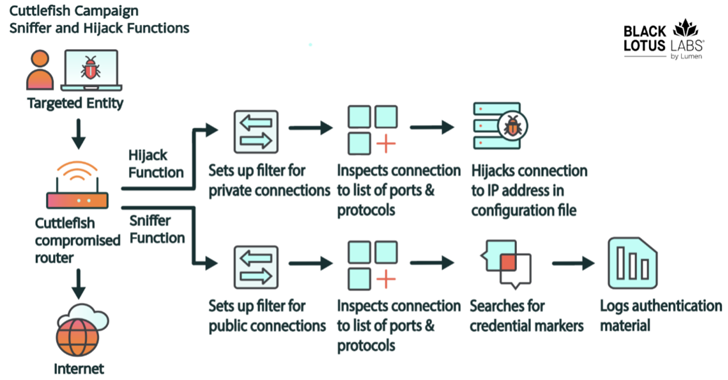
Read MoreMay 02, 2024NewsroomCyber Espionage / Network Security A new malware called Cuttlefish is targeting small office and home office (SOHO) routers with the goal of stealthily monitoring all traffic through the devices and gather authentication data from HTTP GET and POST requests. “This malware is modular, designed primarily to steal authentication material found in web…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm