‘I can’t imagine a better leader, he’s got terrific vision, he’s got the fire in his belly that I share with him and he’s ready to take it to a whole new level. I’m looking forward to plugging in and being on the ride, but I don’t need to steer the ship,’ Pax8’s John Street…
Read MoreNew Hewlett Packard Enterprise VP of Worldwide Distribution Michael Bernhardt told CRN among his top priorities will be to “increase engagement and participation” in the “under-utilized” HPE distribution led service provider program. Hewlett Packard Enterprise Director of Worldwide Distribution Michael Bernhardt, a 28-year HPE and HP channel veteran, has been promoted to vice president of…
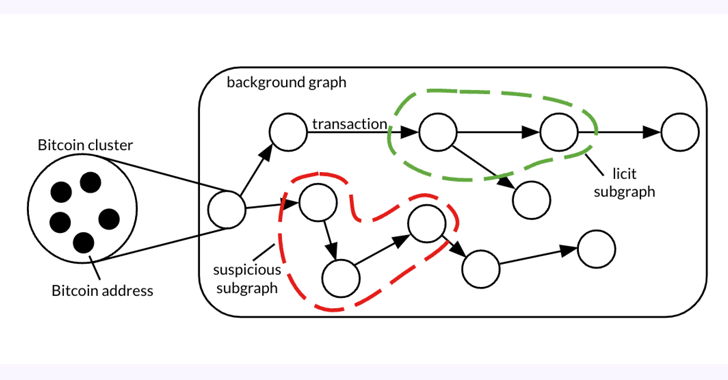
Read MoreMay 01, 2024NewsroomFinancial Crime / Forensic Analysis A forensic analysis of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters associated with illicit activity and money laundering, including detecting criminal proceeds sent to a crypto exchange and previously unknown wallets belonging to a Russian darknet market. The findings come from Elliptic in…
Read MoreMicrosoft has confirmed that the April 2024 Windows security updates break VPN connections across client and server platforms. The company explains on the Windows health dashboard that “Windows devices might face VPN connection failures after installing the April 2024 security update or the April 2024 non-security preview update.” “We are investigating user reports, and we…
Read MoreMay 01, 2024NewsroomMalware / Android Cybersecurity researchers have discovered a previously undocumented malware targeting Android devices that uses compromised WordPress sites as relays for its actual command-and-control (C2) servers for detection evasion. The malware, codenamed Wpeeper, is an ELF binary that leverages the HTTPS protocol to secure its C2 communications. “Wpeeper is a typical backdoor…
Read More‘For us, it’s about being focused on executing where there’s high demand in IT spend. And recovery, resilience, cyber, AI are the areas where companies are still spending, and that’s where we play,’ says Commvault CFO Gary Merrill. Growth in Commvault’s subscription business led to the data protection technology developer’s overall growth for fiscal 2024.…
Read MoreA new malware named ‘Cuttlefish’ has been spotted infecting enterprise-grade and small office/home office (SOHO) routers to monitor data that passes through them and steal authentication information. Lumen Technologies’ Black Lotus Labs examined the new malware and reports that Cuttlefish creates a proxy or VPN tunnel on the compromised router to exfiltrate data discreetly while…
Read MoreQantas Airways confirms that some of its customers were impacted by a misconfiguration in its app that exposed sensitive information and boarding passes to random users. Qantas is Australia’s flag carrier and the largest airline by fleet size, operating 125 aircraft and serving 104 destinations. Qantas has 23,500 employees and an annual revenue of almost $12.9 billion. Earlier today,…
Read MoreTenable Cloud Security is enhancing its capabilities with malware detection. Combined with its cutting-edge, agentless vulnerability-scanning technology, including its ability to detect anomalous behavior, this new capability makes Tenable Cloud Security a much more complete and effective solution. Read on to find out how. In the ever-evolving landscape of cloud computing, security remains paramount. Even…
Read MoreThese attacks were primarily leveraged by ransomware and other extortion-related threat actors, and the main entry point was web applications, the report noted. Analyzing the data also reveals a significant area of weakness among many organizations — bad actors are more quickly harnessing vulnerabilities than organizations can patch them. It takes organizations approximately 55 days…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm