The content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. We wanted to know what was going on within our vast networks; modern tools have made it possible for us to know too…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. No, I am not taking a photo of my nose hair! I am Snapping and sharing for my Snapgroup to keep my Snapstreak active while I see where they are…
Read MoreInterpol announced it arrested 41 individuals and taken down 1,037 servers and infrastructure running on 22,000 IP addresses facilitating cybercrime in an international law enforcement action titled Operation Synergia II. The operation took place between April and August 2024, spanning 95 countries and resulting in 41 arrests of those linked to various crimes, including ransomware,…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. Most companies have some cybersecurity protocols in place in case of a breach. They could be anything from antivirus software to spam filters.…
Read More‘I welcome Olivier Blum as our new CEO and I wish to thank Peter Herweck for leading Schneider Electric over the past 18 months,’ said Schneider Chairman Jean-Pascal Tricoire in a statement. Schneider Electric’s board of directors voted unanimously to fire Peter Herweck one year and nine months into his role as CEO of the…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. Cloud computing has become a boon to organizations due to its flexibility, scalability, and cost-effectiveness. However, without proper oversight, it evolves into an…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. From stolen personal data to entire corporate databases, Raid Forums was a digital black market where the most valuable commodities weren’t physical goods…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. As we gear up to celebrate Internet Day on October 29th, let’s take a moment to appreciate how much the Internet has revolutionized…
Read MoreWhen you think of a cyberattack, you probably envision a sophisticated hacker behind a Matrix-esque screen actively penetrating networks with their technical prowess. However, the reality of many attacks is far more mundane. A simple email with an innocent subject line such as “Missed delivery attempt” sits in an employee’s spam folder. They open it…
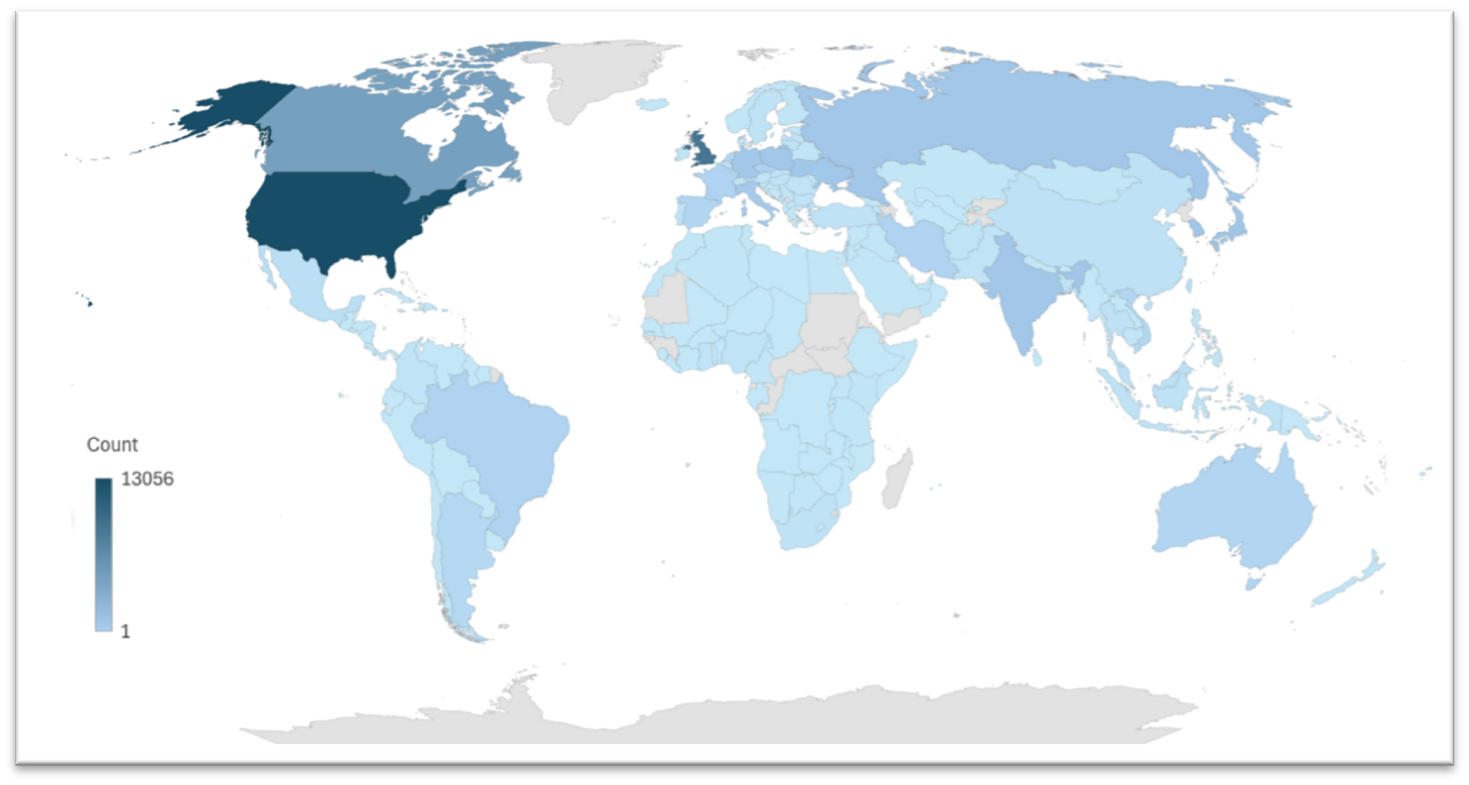
Read MoreExecutive Summary Seven years after its first appearance, the proxy server botnet Ngioweb continues its impactful presence on the internet with barely any relevant changes in its original code. Threat actors have continued to actively use Nbioweb extensively to scan for vulnerable devices (including a new arsenal of exploits) which can be turned into new…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm