In a major move within the cybersecurity sector, KnowBe4, a leading security awareness training platform, has announced the acquisition of Egress, a prominent cloud email security provider. This strategic partnership blends two powerful forces in the battle against cyber threats. Who are KnowBe4 and Egress? KnowBe4: A pioneer in security awareness training, KnowBe4 empowers organizations…
Read MoreApr 27, 2024NewsroomMalware / Software Security An ongoing social engineering campaign is targeting software developers with bogus npm packages under the guise of a job interview to trick them into downloading a Python backdoor. Cybersecurity firm Securonix is tracking the activity under the name DEV#POPPER, linking it to North Korean threat actors. “During these fraudulent…
Read MoreMicrosoft’s Earnings Results Say A Lot About Cloud And AI Growth, Google And AWS Competition
by nlqip
‘Azure could become the biggest and more important hyperscaler provider,’ according to one analyst report Friday. Microsoft’s latest quarterly results beat a variety of expectations from Wall Street, but of importance to its services partners is the tech giant’s expectation that not only can artificial intelligence grow, but its cloud offerings have not yet plateaued—with…
Read MoreFriday Squid Blogging: Searching for the Colossal Squid A cruise ship is searching for the colossal squid. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here. Tags: squid Posted on April 26, 2024 at 5:07 PM…
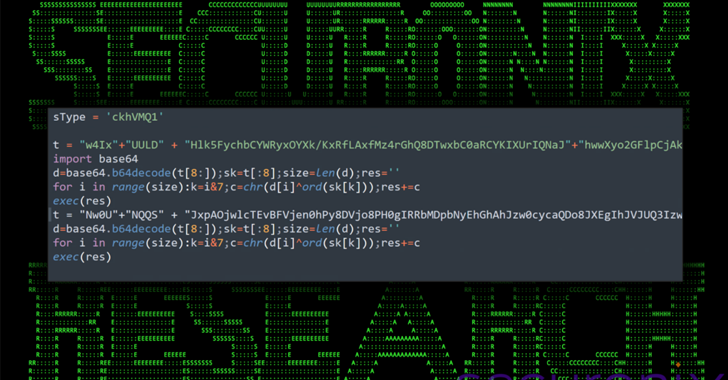
Read MoreSecure Coding Python’s versatility and short learning curve are just two factors that explain the language’s ‘grip’ on cybersecurity 25 Apr 2024 • , 3 min. read The Python programming language, born from the creative genius of Guido van Rossum as far back as some 35 years ago, has evolved into a crucial tool for…
Read MoreKaseya CEO Fred Voccola: ‘Struggling’ Silicon Valley, Boston Companies Lack ‘Grit,’ ‘Don’t Have To Work For What They Have’
by nlqip
‘When I look at companies coming out of [Silicon Valley] or out of Boston, even L.A., they don’t have the grit. They don’t have the edge. They don’t have to work for what they have, and that’s why you see a lot of them struggling,’ Voccola told attendees of the Miami Tech Summit last week.…
Read MoreTelegram users are currently experiencing issues worldwide, with users unable to use the website and mobile apps. […] Source link lol
Read More‘Semiconductors are the currency that will drive the global economy for decades to come. We are one of two, maybe three, companies in the world that can continue to enable next-generation chip technologies and the only one that has Western capacity and R&D, and we will participate in the entire AI market,’ says Intel CEO…
Read More‘What does it mean that Intel’s chip is AI-enabled? What does it mean that the Dell and Lenovo and HP laptops are AI-enabled? What does that do for me? … The more clarity that we can bring to our partners, the better,’ says Kirk Robinson, executive vice president and president of North America at Ingram…
Read MoreFor the week ending April 26, CRN takes a look at the companies that brought their ‘A’ game to the channel including IBM, Nvidia, ThreatLocker, HPE Aruba and FlexAI. The Week Ending April 26 Topping this week’s Came to Win is IBM for its blockbuster deal to acquire cloud infrastructure management tool developer HashiCorp. Also…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm