The U.S. Federal Bureau of Investigation (FBI) has sought assistance from the public in connection with an investigation involving the breach of edge devices and computer networks belonging to companies and government entities. “An Advanced Persistent Threat group allegedly created and deployed malware (CVE-2020-12271) as part of a widespread series of indiscriminate computer intrusions designed…
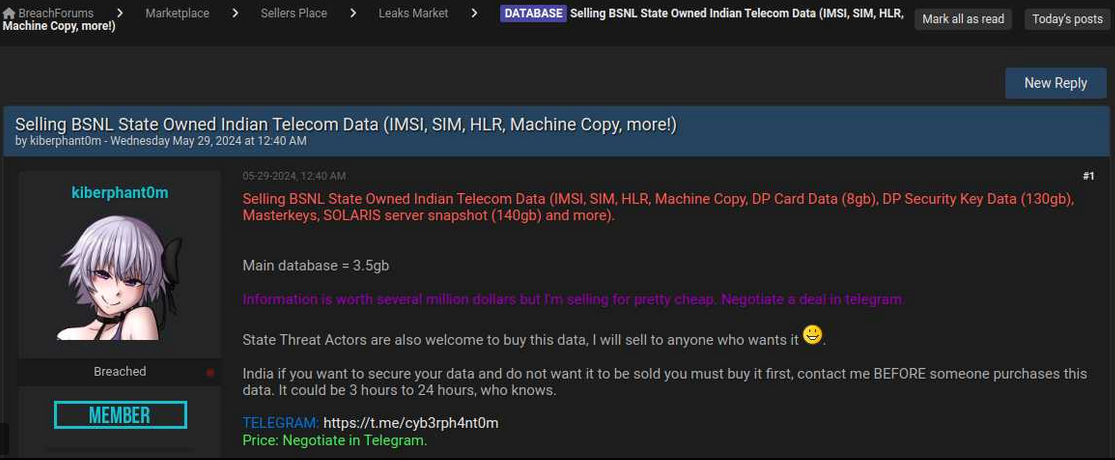
Read MoreA 26-year-old man in Ontario, Canada has been arrested for allegedly stealing data from and extorting more than 160 companies that used the cloud data service Snowflake. On October 30, Canadian authorities arrested Alexander Moucka, a.k.a. Connor Riley Moucka of Kitchener, Ontario, on a provisional arrest warrant from the United States. Bloomberg first reported Moucka’s…
Read MoreThe U.S. Cybersecurity & Infrastructure Security Agency is warning about last-minute influence operations conducted by Iranian and Russian actors to undermine the public trust in the integrity and fairness of the upcoming presidential election. In a joint statement, CISA, the Office of the Director of National Intelligence (ODNI), and the Federal Bureau of Investigation (FBI),…
Read MoreCanadian authorities have arrested a man suspected of having stolen the data of hundreds of millions after targeting over 165 organizations, all of them customers of cloud storage company Snowflake. According to Canada’s Department of Justice, Alexander “Connor” Moucka was taken into custody on Wednesday at the request of the United States and is scheduled to…
Read More‘Demand for connected enterprise planning is on the rise,’ says David Leckstein, senior managing director and lead of Americas Technology at Accenture. Accenture is growing its Anaplan capabilities with the acquisition of consulting company Allitix, adding new expertise in financial planning, financial analysis, sales performance management and supply chain. The consulting giant, No. 1 on…
Read MoreMarks, who was most recently vice president of global channels at SentinelOne, tells CRN that he sees a ‘tremendous’ opportunity ahead for MSP and MSSP partners working with the cybersecurity vendor. Cynomi, an MSP-focused startup whose vCISO platform is tailored toward securing small and medium-sized enterprises, announced Tuesday it has hired a veteran of the…
Read MoreGoogle fixed two actively exploited Android zero-day flaws as part of its November security updates, addressing a total of 51 vulnerabilities. Tracked as CVE-2024-43047 and CVE-2024-43093, the two issues are marked as exploited in limited, targeted attacks. “There are indications that the following may be under limited, targeted exploitation,” says Google’s advisory. The CVE-2024-43047 flaw…
Read MoreThe provider of power management technologies confirmed that a developer platform was impacted by ‘unauthorized access.’ Schneider Electric confirmed Monday that a developer platform used by the company was impacted by a “cybersecurity incident” that is now under investigation. According to a BleepingComputer report, a threat actor has claimed, during a conversation with the media…
Read MoreFrom elections to ransomware, CISA Director Jen Easterly breaks down the threats to America’s critical infrastructure and what’s being done to stop them, sharing along the way her journey from the real-life battlefield to the frontlines of cybersecurity. A rare glimpse into the most pressing threats America faces—and a compelling story about Director Easterly’s own…
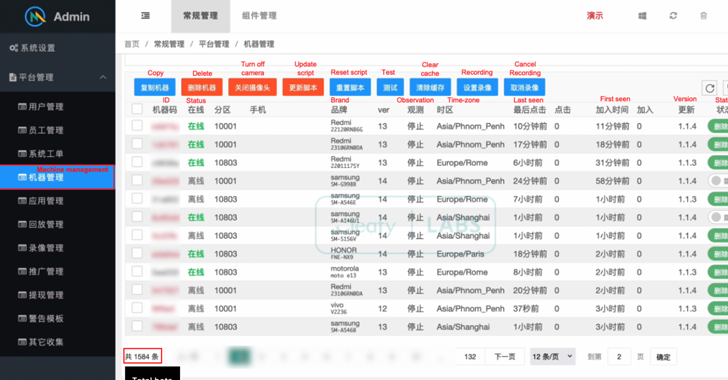
Read MoreNov 05, 2024Ravie LakshmananMobile Security / Cyber Attack Over 1,500 Android devices have been infected by a new strain of Android banking malware called ToxicPanda that allows threat actors to conduct fraudulent banking transactions. “ToxicPanda’s main goal is to initiate money transfers from compromised devices via account takeover (ATO) using a well-known technique called on-device…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm