The Housing Authority of the City of Los Angeles (HACLA), one of the largest public housing authorities in the United States, confirmed that a cyberattack hit its IT network after recent breach claims from the Cactus ransomware gang. HACLA provides affordable public housing and assistance programs to low-income families, children, and seniors in Los Angeles,…
Read MoreMicrosoft warned customers they might experience up to 30 minutes of black screens when logging into Azure Virtual Desktop (AVD) after installing the KB5040525 Windows 10 July 2024 preview update. Additional symptoms include single sign-on (SSO) failures (on Office applications such as Outlook and Teams) blocking connections to backend services or preventing data syncs and…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/labs-research/ngioweb-remains-active-7-years-later” on this server. Reference #18.c5d7ce17.1730496600.961d1ab https://errors.edgesuite.net/18.c5d7ce17.1730496600.961d1ab Source link lol
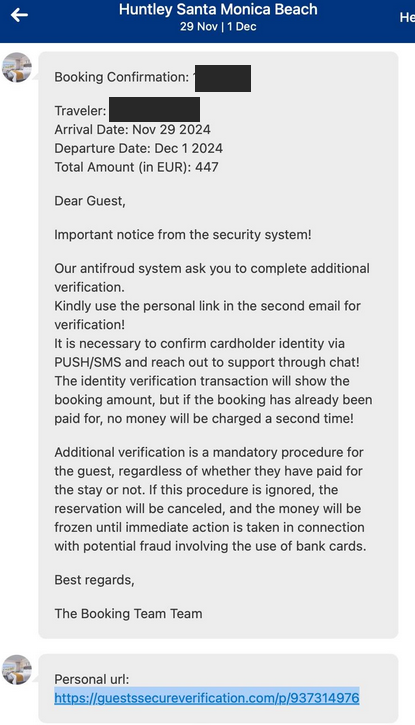
Read MoreA number of cybercriminal innovations are making it easier for scammers to cash in on your upcoming travel plans. This story examines a recent spear-phishing campaign that ensued when a California hotel had its booking.com credentials stolen. We’ll also explore an array of cybercrime services aimed at phishers who target hotels that rely on the…
Read MoreOpenAI’s new “ChatGPT search” Chrome extension feels like nothing more than a typical search hijacker, changing Chrome’s settings so your address bar searches go through ChatGPT Search instead. Yesterday, OpenAI launched its new AI search product “ChatGPT Search,” which provides real-time answers to conversational searches on the platform. “ChatGPT can now search the web in a…
Read MoreCisco CEO Chuck Robbins On Cisco 360, The ‘Holy Grail’ AI Networking, Security Opportunities, And Why The Data Center Isn’t Dead
by nlqip
‘When you look at the traditional Splunk platform and the Cisco security portfolio, and then you look at the networking infrastructure portfolio, partners who really spend the time to understand all of that will have a very unique differentiation in bringing all that together for a customer and helping them realize the benefits that we…
Read MoreVideo Election interference, American Water and the Internet Archive breaches, new cybersecurity laws, and more – October saw no shortage of impactful cybersecurity news stories 31 Oct 2024 With so much happening in the world of cybersecurity, staying on top of threats, breaches, scams, and industry insights can feel like a full-time job. So, let…
Read MoreAs Google Cloud’s operating income surged 632 percent in third quarter 2024, Google’s top executives say the company is hiring fewer employees compared to a few years ago. Top Google executives say they are hiring fewer employees compared to a few years ago as the $88 billion tech giant looks to drive operational efficiency as…
Read MoreLastPass is warning about an ongoing campaign where scammers are writing reviews for its Chrome extension to promote a fake customer support phone number. However, this phone number is part of a much larger campaign to trick callers into giving scammers remote access to their computers, as discovered by BleepingComputer. LastPass is a popular password…
Read More‘These are the most mission-critical applications with the highest performance requirements,’ Josh Lee, chief technology officer at Dell platinum partner VirtuIT, tells CRN. ‘With these boxes, any efficiencies to make the cost-per-terabyte and cost of input output lower is great news for customers.’ Dell Technologies’ newest upgrades to its PowerMax storage arrays give partners faster,…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm