If you read much about cyberattacks or data breaches, you’ve surely run across the terms vulnerabilities, threats, and exploits. Unfortunately, these terms are often left undefined, used incorrectly or, worse, interchangeably. That’s a problem, because misunderstanding these terms (and a few other key ones) can lead organizations to make incorrect security assumptions, focus on the…
Read More‘A lot of the initial focus of AI was on public cloud, training these large language models. But when it comes to real applications, they’re going to be deployed where the data is and a lot of data is on-prem, it’s at the edge,’ Nutanix CEO Rajiv Ramaswami tells CRN. For partners who want to…
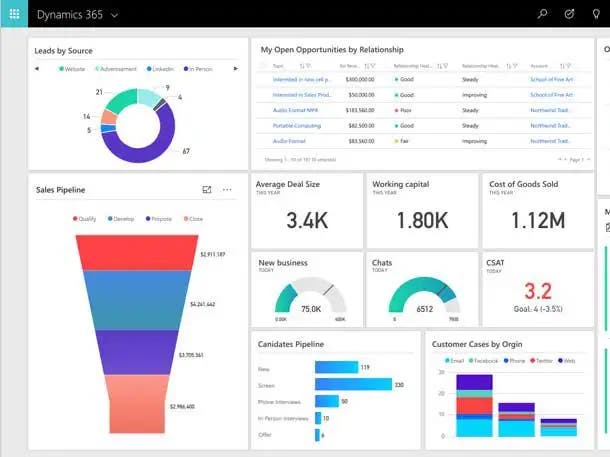
Read MoreOfferings will increase by as much as 17 percent and as little as 9 percent. Microsoft plans to increase prices for a variety of Dynamics 365 offerings on Oct. 1 by an average of 12 percent or $17 per user or per device per month as the vendor adds more generative artificial intelligence functionality and…
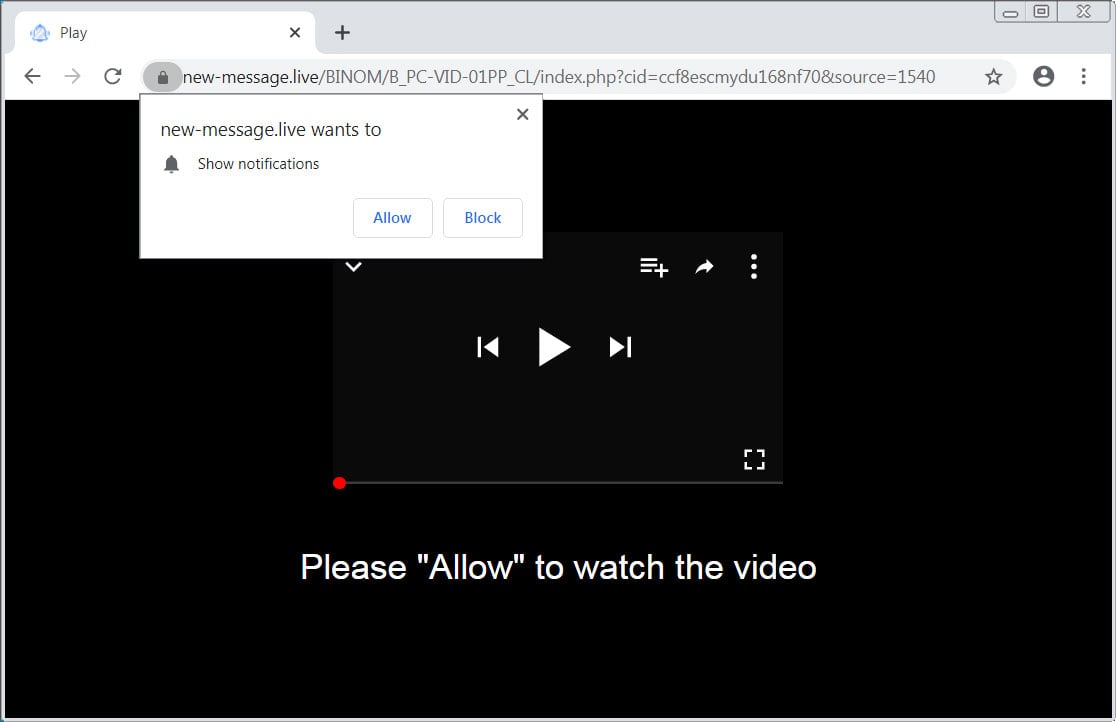
Read MoreIn order to remove Please Allow to watch the video Notification Page completely you will need to reset Chrome back to its initial settings. Doing these steps will erase all configuration information from Chrome such as your home page, tab settings, saved form information, browsing history, and cookies. This process will also disable any installed…
Read MoreHere are the 50 hottest data center companies in the world—which includes tech giants, colocation specialists and edge providers—that made CRN’s 2024 Data Center 50 list. Data center innovation is being taken to the next level in the new era of artificial intelligence as chipmakers such as AMD and Nvidia, hardware leaders such as Cisco…
Read MoreCisco’s Talos research team says it’s monitoring a ‘global increase in brute-force attacks’ against targets including VPN services, while an exploit has been released for a critical vulnerability in Palo Alto Networks’ PAN-OS firewall software. Hackers continue to escalate their targeting of network security devices and remote access services as a means of breaching customer…
Read More‘I have a client waiting on a solution, a service, a product or an opportunity and I can’t wait,’ Sam Heard, owner of MSP Data Integrity Services, tells CRN. ‘The faster I can get that information effectively from Climb, the better I can take care of my client. That’s the partnership that I love.’ From…
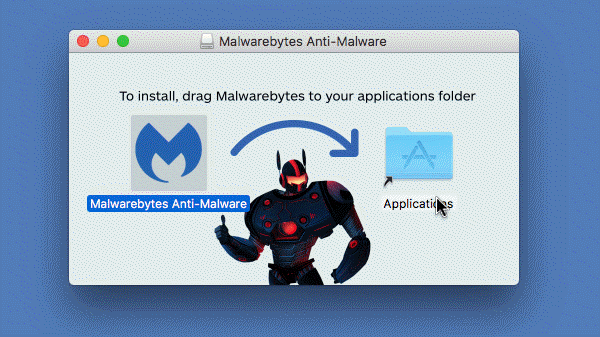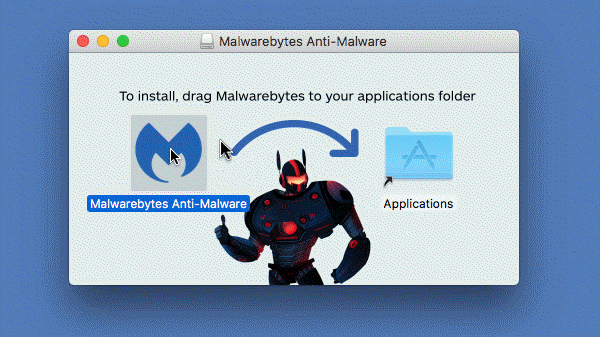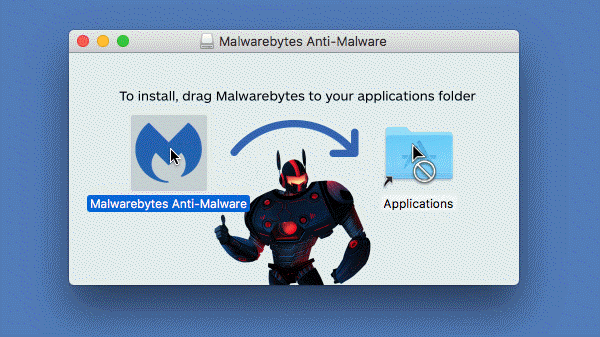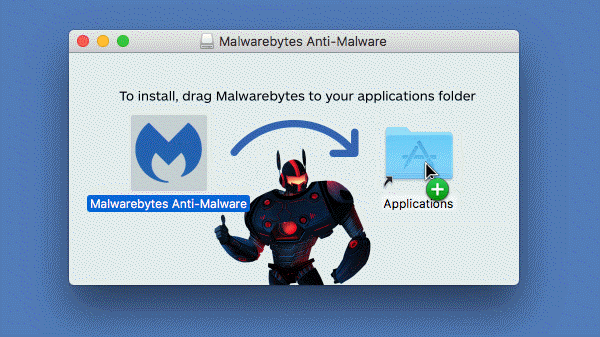
Read MoreScreenshots for Malwarebytes for Mac BleepingComputer Review: Malwarebytes Anti-Malware for Mac is a free security tool that allows you to scan your computer for common macOS infections and remove them. While focusing on adware infections, Malwarebytes for Mac will also scan for other known infections that are being released for the macOS operaitng system. With…
Read MoreCyber security breaches have become rapidly one of the main concerns among all kinds of organizations. Even though companies are investing in complex new solutions against undesired guests, the task has never been easier. The various backdoors, loose ends and interconnected computer systems, mean that these intrusions are sometimes… inevitable. If unfortunately that happens, companies…
Read MorePCOPTIMIZE.EXE Information This is an undesirable program. This file has been identified as a program that is undesirable to have running on your computer. This consists of programs that are misleading, harmful, or undesirable. If the description states that it is a piece of malware, you should immediately run an antivirus and antispyware program. If…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA