The expanded Accelerate with Confluent initiative offers resources and expertise to help systems integrators develop repeatable services and solutions around the Confluent data streaming platform and help customers realize value more quickly. Data streaming technology developer Confluent has launched a revamped partner program to help systems integrators better develop and deliver solutions based on the…
Read MoreFrom Broadcom-VMware to Google Gemini, CRN breaks down the 12 biggest product launches and news from Google Cloud Next that partners and customers need to know about. Google Cloud ramped up its artificial intelligence and generative AI charge at Google Cloud Next 2024 last week with some huge product launches and news—including a new partnership…
Read MoreThe long-running struggle between cybersecurity and hackers has existed in computing since the beginning of the 1970s. Its impact on users and businesses has escalated over the past decades: the expansion of the internet to all corners of the world, and the ever-growing digitization of society, with all the benefits of the digital revolutions, has…
Read MoreApply appropriate updates provided by Google to vulnerable systems immediately after appropriate testing. (M1051: Update Software) Safeguard 7.1: Establish and Maintain a Vulnerability Management Process: Establish and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this Safeguard. Safeguard 7.4: Perform…
Read MoreFor the 2024 Internet of Things 50 CRN picked the coolest and most noteworthy channel-friendly vendors driving innovation forward and delivering real value, whether they’re focused on hardware, software, networking and connectivity, security or industrial solutions. There is continued demand to deploy sensors and connect machines so that data from the real world can be…
Read MoreThe massive amounts of data possessed by Google and Apple could make each company a strong contender in generative AI. Microsoft and OpenAI may have a first-mover advantage in the exploding market for AI chatbots, but don’t count out some of the other tech giants that have access to massive quantities of AI-training data, such…
Read MoreWhile ransomware attacks decreased after the LockBit and BlackCat disruptions, they have once again started to ramp up with other operations filling the void. A relatively new operation called RansomHub gained media attention this week after a BlackCat affiliate used the newer operation’s data leak site to extort Change HealthCare once again. Change HealthCare allegedly…
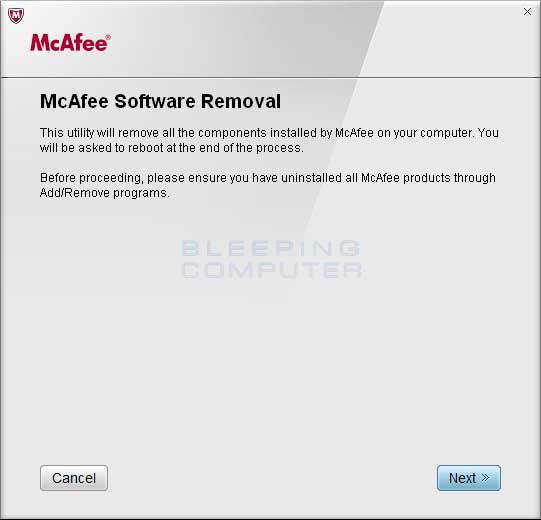
Read MoreScreenshots for McAfee Consumer Products Removal tool BleepingComputer Review: The McAfee Consumer Products Removal tool allows you to remove component data of McAfee consumer products listed below on your windows system. This tool is to be used after uninstalling McAfee software through the windows installer tool. This tool will not run on Windows 98 or ME. Please note, that…
Read MoreTenable Expands Generative AI Capabilities for Faster Attack Path Analysis and Mitigation Guidance
by nlqip
Tenable®, the Exposure Management company, today announced innovative enhancements to ExposureAI, the generative AI capabilities and services within its Tenable One Exposure Management Platform. The new features enable customers to quickly summarize relevant attack paths, ask questions of an AI assistant and receive specific mitigation guidance to act on intelligence and reduce risk. The platform’s generative AI-powered search…
Read MoreTry Tenable Web App Scanning Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA