“The customers that are coming from all of those competitors are saying the same thing, which is, ‘I want a beautifully well-engineered, elegantly written, modern architecture platform for my business,’” says Michael George, Syncro CEO. While Michael George knows competition is healthy, he believes Syncro’s toolset is perfectly aligned to help MSPs grow. “I’d like…
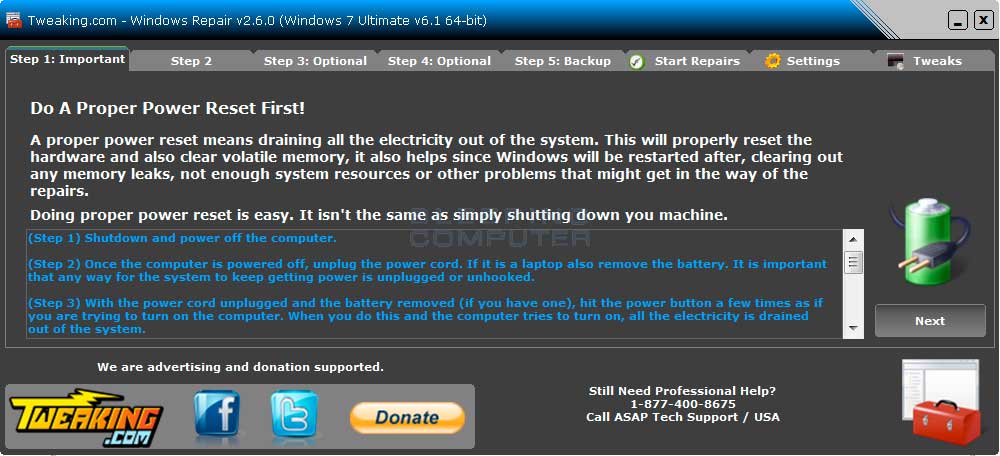
Read MoreScreenshots for Windows Repair (All In One) BleepingComputer Review: Windows Repair is a utility that contains numerous mini-fixes for Windows. This tool will allow you to repair common issues with your computer such as firewall, file permission, and Windows Update problems. When using this tool you can select the particular fixes you would like to…
Read MorePublished by Aghiath Chbib Results-oriented, adaptable, established executive equipped with 20 years of success driving global business in large, multimillion-dollar organizations and private start-ups. Extensive experience spearheading operations within complex, technology-driven environments ensuring adherence to organizational strategies and best practices. Expert at building and directing high- performing, cross-functional teams with a focus on leadership, collaboration,…
Read MoreApply appropriate updates provided by Ivanti to vulnerable systems immediately after appropriate testing. (M1051: Update Software) Safeguard 7.1 : Establish and Maintain a Vulnerability Management Process: Establish and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this Safeguard. Safeguard 7.2:…
Read MoreSUMMARY Note: This joint Cybersecurity Advisory (CSA) is part of an ongoing #StopRansomware effort to publish advisories for network defenders that detail various ransomware variants and ransomware threat actors. These #StopRansomware advisories include recently and historically observed tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to help organizations protect against ransomware. Visit stopransomware.gov…
Read MoreTo ensure they have the most complete information about the security posture of assets, organizations should deploy scans that use credentials. Scans that use credentials and successfully authenticate on a system (and run with Local Security Checks enabled) return a more comprehensive set of data about the system. This Assurance Report Card (ARC) provides the…
Read MoreA GitHub flaw, or possibly a design decision, is being abused by threat actors to distribute malware using URLs associated with a Microsoft repository, making the files appear trustworthy. While most of the malware activity has been based around the Microsoft GitHub URLs, this “flaw” could be abused with any public repository on GitHub, allowing…
Read MoreOracle addresses 239 CVEs in its second quarterly update of 2024 with 441 patches, including 38 critical updates. Background On April 16, Oracle released its Critical Patch Update (CPU) for April 2024, the second quarterly update of the year. This CPU contains fixes for 239 CVEs in 441 security updates across 30 Oracle product families.…
Read MoreCOLUMBIA, Md. and KubeCon Europe 2024 (March 19, 2024) — Tenable®, the Exposure Management company, today announced expanded Tenable Cloud Security cloud-native application protection platform (CNAPP) capabilities for Kubernetes on-premises and public cloud environments. These latest advancements extend Tenable’s CNAPP benefits, such as contextual risk visibility, preventive security controls, and zero trust / least privilege enforcement, to…
Read MoreTry Tenable Web App Scanning Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA