‘Pax8 recently made the difficult decision to conduct a reduction in workforce. This move primarily impacted North America and was less than five percent of our global workforce. Parting with valued teammates is never easy, but these actions will enable us to optimize operations, increase alignment, and position our business for long-term success,’ said a…
Read MoreThe departure of Sam Altman, Greg Brockman and, potentially, a large percentage of OpenAI employees to Microsoft may not ultimately be the best thing for the tech giant’s aspirations in GenAI. One of the biggest strengths of OpenAI has long been that it had backing, financial and otherwise, from Microsoft, without needing Microsoft to approve…
Read MorePRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure | CISA
by nlqip
SUMMARY The Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and Federal Bureau of Investigation (FBI) assess that People’s Republic of China (PRC) state-sponsored cyber actors are seeking to pre-position themselves on IT networks for disruptive or destructive cyberattacks against U.S. critical infrastructure in the event of a major crisis or conflict with…
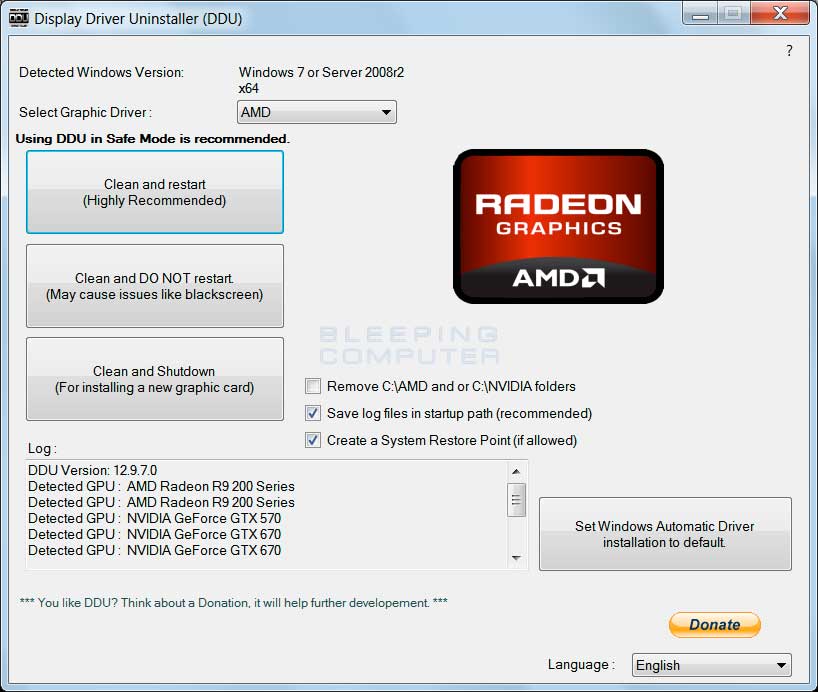
Read MoreScreenshots for Display Driver Uninstaller BleepingComputer Review: Display Driver Uninstaller, or DDU, is a driver utility programs that allows you to remove all traces of NVIDIA, AMD, and INTEL display and audio drivers from Windows. This allows you to perform a clean install of new drivers so that there are no potential issues with previous…
Read MoreIntroduction Once attackers have gained a foothold, perhaps by exploiting a remote code execution (RCE) vulnerability, leveraging a file upload, or some other tactic to gain execution on the target, they may end up using a web shell, as we described in a previous article. However, web shells are limited, and attackers may often want…
Read MoreAfter analyzing traffic from 159 bot defense customers, this review found that in the absence of a bot defense solution, Mobile APIs experience significantly more automation than Web applications. However, once a bot defense solution is deployed in mitigation/blocking mode, we see a reversal, with Web having higher levels of persistent attacks despite consistent mitigation.…
Read MoreMedia Room
by nlqip
https://www.thenationalnews.com/future/technology/2024/04/12/apple-sends-out-ip… Source link lol
Read MoreThe National Information Assurance (NIA) Policy v2.0 requires that agencies classify their assets. Tenable recommends using the Cyber Exposure Life Cycle model in conjunction with NIAv2 compliance efforts. The first stage, Discovery, of the Cyber Exposure lifecycle includes identifying and mapping assets across computing environments. In order to maintain a standardized method of classification of…
Read MoreTenable Research delivers world class exposure intelligence, data science insights, zero day research and security advisories. Our Security Response Team (SRT) in Tenable Research tracks threat and vulnerability intelligence feeds to make sure our research teams can deliver sensor coverage to our products as quickly as possible. The SRT also works to dig into technical…
Read More‘Gaudi 3 strengthens our partnership by addressing customer infrastructure needs, reducing [total cost of ownership] and easing deployment. And it’s all through an open ecosystem featuring AI frameworks optimized for Dell and Gaudi 3 along with scalable Ethernet-based AI fabrics,’ Michael Dell said at the Intel Vision event Tuesday. Dell Technologies founder, Chairman and CEO…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA