What are the risks and consequences of having your health data exposed and what are the steps to take if it happens to you? Source link wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3…
Read MoreApr 20, 2024NewsroomVulnerability / Endpoint Security Users of the CrushFTP enterprise file transfer software are being urged to update to the latest version following the discovery of a security flaw that has come under targeted exploitation in the wild. “CrushFTP v11 versions below 11.1 have a vulnerability where users can escape their VFS and download…
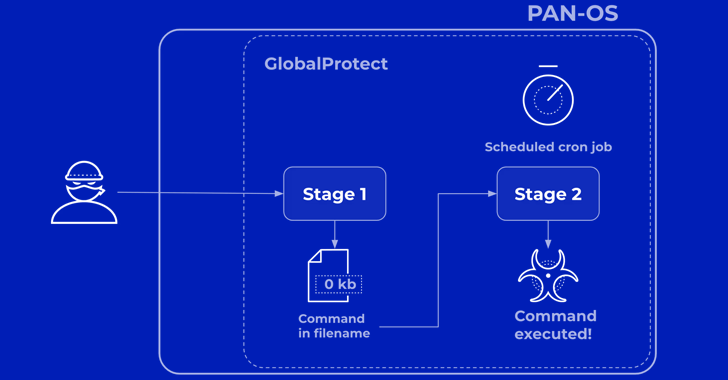
Read MoreApr 20, 2024NewsroomVulnerability / Network Security Palo Alto Networks has shared more details of a critical security flaw impacting PAN-OS that has come under active exploitation in the wild by malicious actors. The company described the vulnerability, tracked as CVE-2024-3400 (CVSS score: 10.0), as “intricate” and a combination of two bugs in versions PAN-OS 10.2,…
Read MoreChief information security officers (CISOs) understand the importance of having an incident response plan in place to help decrease the impact of a cyberattack. That’s because despite increased awareness and evolving security technology and practices, cyber threats continue to grow in both volume and sophistication. Microsoft security researchers have seen a 130.4% increase in organizations that have…
Read MoreFriday Squid Blogging: Squid Trackers A new bioadhesive makes it easier to attach trackers to squid. Note: the article does not discuss squid privacy rights. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here. Tags: privacy,…
Read MoreVulnerability exploits the difference between DOS and NT paths When someone is asked to type the path to a file on a Windows system, they are likely to type something of the form C:directorysubdirectoryfile.txt. This is known as a DOS-style file path and has been the most common way to represent a file’s location ever…
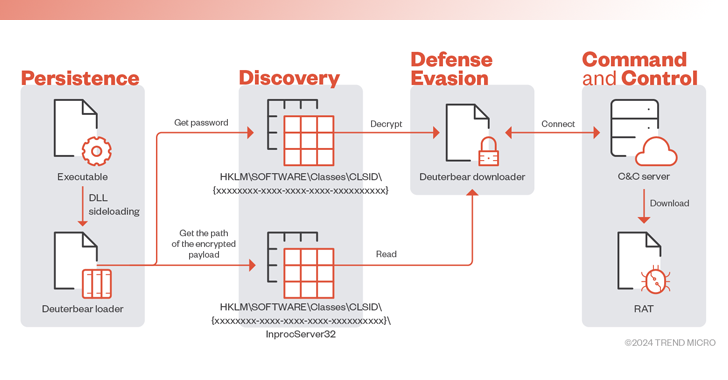
Read MoreApr 19, 2024NewsroomNetwork Security / Firmware Security Technology, research, and government sectors in the Asia-Pacific region have been targeted by a threat actor called BlackTech as part of a recent cyber attack wave. The intrusions pave the way for an updated version of modular backdoor dubbed Waterbear as well as its enhanced successor referred to…
Read MoreIn the fast-paced realm of modern business, adaptation is key. As organizations transition to hybrid work models and embrace cloud-based operations, the very fabric of how we work has transformed – opening doors to more security risks. With more freelancers, contractors, and BYOD programs accessing corporate applications (like web and SaaS applications) via their own…
Read MoreCisco has released security advisories for vulnerabilities in the Cisco integrated management controller. A remote cyber threat actor could exploit one of these vulnerabilities to take control of an affected system. Users and administrators are encouraged to review the following advisories and apply the necessary updates: Cisco Integrated Management Controller CLI Command Injection Vulnerability Cisco…
Read MoreThreat actors behind the Akira ransomware group have extorted approximately $42 million in illicit proceeds after breaching the networks of more than 250 victims as of January 1, 2024. “Since March 2023, Akira ransomware has impacted a wide range of businesses and critical infrastructure entities in North America, Europe, and Australia,” cybersecurity agencies from the…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA