If you hear the term “microbranch,” you probably picture a small banking location with a handful of ATMs. For many years, this term was specific to the financial industry, but as remote work and internet-connected devices have grown more common, the definition has evolved to include any small remote office associated with a larger corporation.…
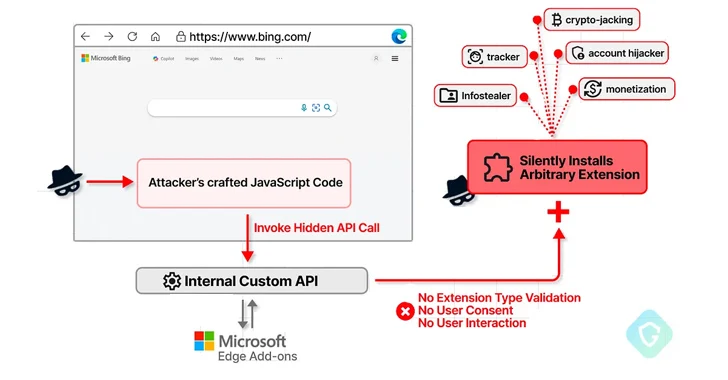
Read MoreMar 27, 2024NewsroomVulnerability / API Security A now-patched security flaw in the Microsoft Edge web browser could have been abused to install arbitrary extensions on users’ systems and carry out malicious actions. “This flaw could have allowed an attacker to exploit a private API, initially intended for marketing purposes, to covertly install additional browser extensions…
Read MoreScams Personal loan scams prey on your financial vulnerability and might even trap you in a vicious circle of debt. Here’s how to avoid being scammed when considering a loan. 26 Mar 2024 • , 6 min. read Times have been tough financially for many of us since the pandemic. Climate shocks, food and energy…
Read More“With Verify API, businesses can customize the verification and authentication experience by market needs, customer preferences, or business priorities with peace of mind—and with automatic multichannel fallback,” the company said in a press release. Verify API also allows custom routing to help customers build routing rules for tailored delivery across all channels and markets. Arms…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-032 DATE(S) ISSUED: 03/26/2024 OVERVIEW: Multiple Vulnerabilities have been discovered in Google Chrome, which could allow for arbitrary code execution. Successful exploitation of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user an attacker could then install…
Read MoreMar 27, 2024NewsroomVulnerability / Data Security Cybersecurity researchers are warning that threat actors are actively exploiting a “disputed” and unpatched vulnerability in an open-source artificial intelligence (AI) platform called Anyscale Ray to hijack computing power for illicit cryptocurrency mining. “This vulnerability allows attackers to take over the companies’ computing power and leak sensitive data,” Oligo…
Read MoreMar 27, 2024The Hacker NewsData Protection / Browser Security As SaaS applications dominate the business landscape, organizations need optimized network speed and robust security measures. Many of them have been turning to SASE, a product category that offers cloud-based network protection while enhancing network infrastructure performance. However, a new report: “Better Together: SASE and Enterprise…
Read MoreSecurity Vulnerability in Saflok’s RFID-Based Keycard Locks It’s pretty devastating: Today, Ian Carroll, Lennert Wouters, and a team of other security researchers are revealing a hotel keycard hacking technique they call Unsaflok. The technique is a collection of security vulnerabilities that would allow a hacker to almost instantly open several models of Saflok-brand RFID-based keycard…
Read MoreCompany: Lake Dallas Independent School District Industry: Education Country: Denton County, Texas Employees: 650 Students: 4000 Locations: 5 campuses, 4 faculty buildings Web: www.ldisd.net Download PDF Lake Dallas ISD serves about 4,000 students in Denton County with a focus on providing big-school opportunities while maintaining a small-town atmosphere. Located adjacent to Lewisville Lake in North Texas, approximately 30 miles…
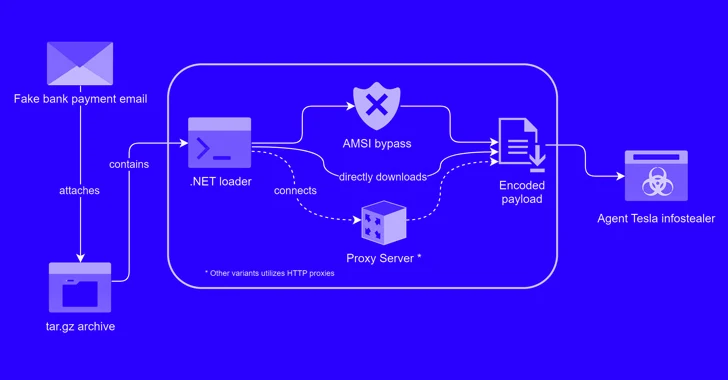
Read MoreMar 27, 2024NewsroomVulnerability / Cybercrime A new phishing campaign has been observed leveraging a novel loader malware to deliver an information stealer and keylogger called Agent Tesla. Trustwave SpiderLabs said it identified a phishing email bearing this attack chain on March 8, 2024. The message masquerades as a bank payment notification, urging the user to…
Read MoreRecent Posts
- IBM VP On Power11 Release: ‘It’s More Tools In Our Partners’ Belts’
- The Dark Side of Domain-Specific Languages: Uncovering New Attack Techniques in OPA and Terraform
- Microsoft 365 Admin portal abused to send sextortion emails
- Everything That You Need to Know About the Dark Web and Cybercrime | BlackFog
- Security plugin flaw in millions of WordPress sites gives admin access