Advisory ID: VMSA-2024-0008 CVSSv3 Range: 7.4-4.8 Issue Date: 2024-04-02 Updated On: 2024-04-02 (Initial Advisory) CVE(s): CVE-2024-22246, CVE-2024-22247, CVE-2024-22248 Synopsis: VMware SD-WAN Edge and SD-WAN Orchestrator updates address multiple security vulnerabilities. Source link wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-040 DATE(S) ISSUED: 04/17/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, which could allow for remote code execution. Successful exploitation of these vulnerabilities could allow for remote code execution in the context of the logged on user. Depending on the privileges associated with the user an attacker could then install…
Read MoreWelcome to this week’s edition of the “Bi-Weekly Cyber Roundup” by Canary Trap. At Canary Trap, it is our mission to keep you up-to-date with the most crucial news in the world of cybersecurity and this bi-weekly publication is your gateway to the latest news. In this week’s roundup, we delve into the Palo Alto…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Software code is constantly growing and becoming more complex, and there is a worrying trend: an increasing number of open-source components are vulnerable…
Read MoreApr 17, 2024NewsroomRansomware / Cyber Espionage A previously undocumented “flexible” backdoor called Kapeka has been “sporadically” observed in cyber attacks targeting Eastern Europe, including Estonia and Ukraine, since at least mid-2022. The findings come from Finnish cybersecurity firm WithSecure, which attributed the malware to the Russia-linked advanced persistent threat (APT) group tracked as Sandworm (aka…
Read MoreThey are successful in doing this because the data these organizations exfiltrate are business sensitive to their business owners, and in some instances, impact the operations of those businesses that encourage ransom payment, according to Laudanski. In an analysis of ransomware data over the last three years and isolating incidents that directly involved compromise of…
Read MoreThe introduction of Open AI’s ChatGPT was a defining moment for the software industry, touching off a GenAI race with its November 2022 release. SaaS vendors are now rushing to upgrade tools with enhanced productivity capabilities that are driven by generative AI. Among a wide range of uses, GenAI tools make it easier for developers…
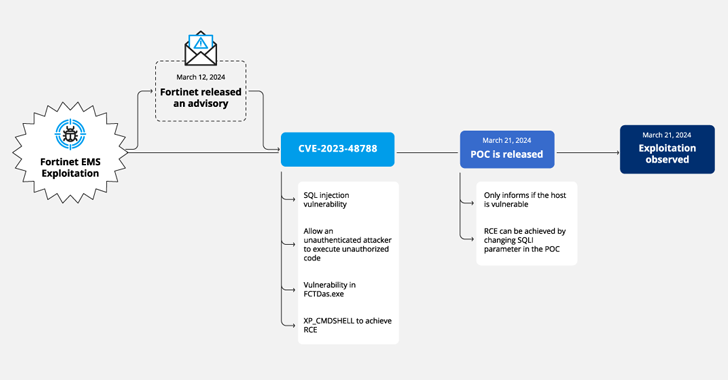
Read MoreApr 17, 2024NewsroomVulnerability / Web Application Firewall Cybersecurity researchers have discovered a new campaign that’s exploiting a recently disclosed security flaw in Fortinet FortiClient EMS devices to deliver ScreenConnect and Metasploit Powerfun payloads. The activity entails the exploitation of CVE-2023-48788 (CVSS score: 9.3), a critical SQL injection flaw that could permit an unauthenticated attacker to…
Read MoreApr 17, 2024NewsroomEncryption / Vulnerability Threat actors are exploiting unpatched Atlassian servers to deploy a Linux variant of Cerber (aka C3RB3R) ransomware. The attacks leverage CVE-2023-22518 (CVSS score: 9.1), a critical security vulnerability impacting the Atlassian Confluence Data Center and Server that allows an unauthenticated attacker to reset Confluence and create an administrator account. Armed…
Read MoreUsing AI-Generated Legislative Amendments as a Delaying Technique Canadian legislators proposed 19,600 amendments—almost certainly AI-generated—to a bill in an attempt to delay its adoption. I wrote about many different legislative delaying tactics in A Hacker’s Mind, but this is a new one. Tags: A Hacker’s Mind, artificial intelligence, laws, LLM, noncomputer hacks Posted on April…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA