The data showed a glass ceiling effect, with almost half (48%) of women experiencing issues related to career growth, such as getting passed over for promotion, significantly more than the 26% of men who reported similar problems. Women typically hit a glass ceiling blocking them from further promotion 6-10 years into their careers. Respect The…
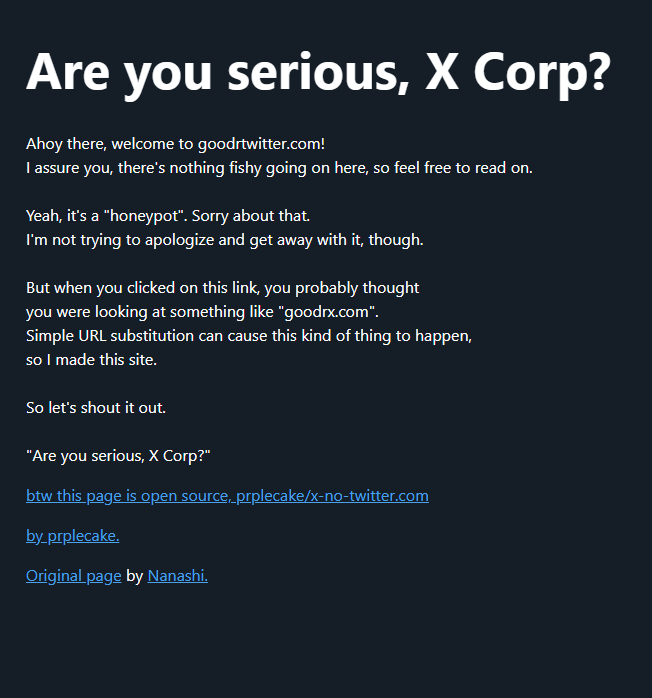
Read MoreOn April 9, Twitter/X began automatically modifying links that mention “twitter.com” to redirect to “x.com” instead. But over the past 48 hours, dozens of new domain names have been registered that demonstrate how this change could be used to craft convincing phishing links — such as fedetwitter[.]com, which is currently rendered as fedex.com in tweets.…
Read MoreApr 10, 2024NewsroomMobile Security / Spyware An active Android malware campaign dubbed eXotic Visit has been primarily targeting users in South Asia, particularly those in India and Pakistan, with malware distributed via dedicated websites and Google Play Store. Slovak cybersecurity firm said the activity, ongoing since November 2021, is not linked to any known threat…
Read MoreApr 10, 2024NewsroomCyber Crime / Malvertising Cybersecurity researchers have discovered a new Raspberry Robin campaign wave that propagates the malware through malicious Windows Script Files (WSFs) since March 2024. “Historically, Raspberry Robin was known to spread through removable media like USB drives, but over time its distributors have experimented with other initial infection vectors,” HP…
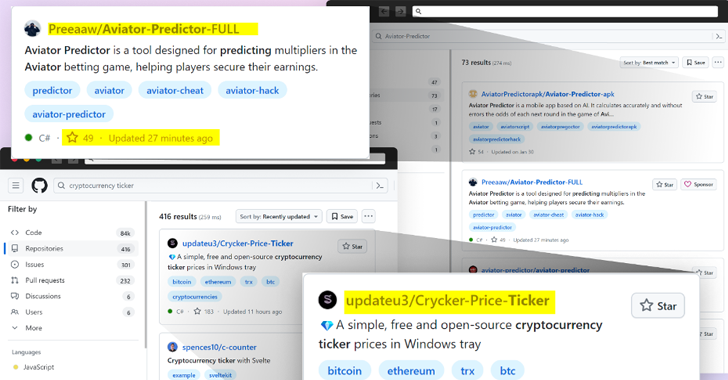
Read MoreApr 10, 2024NewsroomSoftware Security / Supply Chain Attack Threat actors are now taking advantage of GitHub’s search functionality to trick unsuspecting users looking for popular repositories into downloading spurious counterparts that serve malware. The latest assault on the open-source software supply chain involves concealing malicious code within Microsoft Visual Code project files that’s designed to…
Read MoreAdditionally, Gathid promises a seamless integration with an organization’s various systems. “Gathid offers a streamlined, easy-to-deploy solution that receives and models data from digital, operational technology (OT), and physical access control systems (PACS)_ without requiring admin rights or complex bi-directional integration,” the company said. The solution is designed to bridge the accessibility gap in identity…
Read MoreThe need for vCISO services is growing. SMBs and SMEs are dealing with more third-party risks, tightening regulatory demands and stringent cyber insurance requirements than ever before. However, they often lack the resources and expertise to hire an in-house security executive team. By outsourcing security and compliance leadership to a vCISO, these organizations can more…
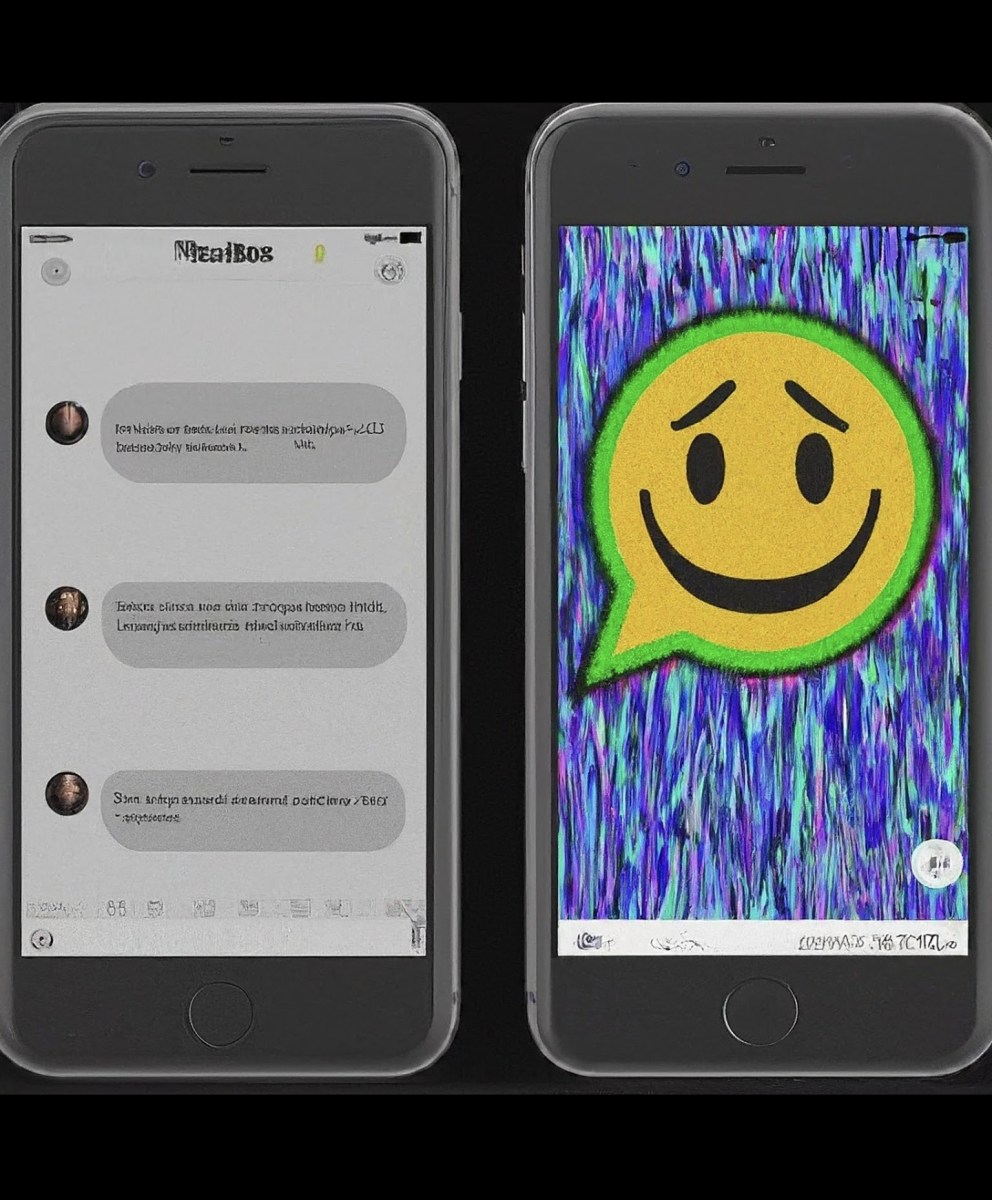
Read MoreWhatsApp mods have become increasingly popular in recent years, offering users a variety of features not available in the official app. However, these unauthorized modifications come with hidden risks that can compromise your privacy and security. A recent report by Kaspersky Lab revealed a malicious WhatsApp mod targeting Arabic-speaking users. This mod, spread through Telegram…
Read MoreLast week I posted a short memorial of Ross Anderson. The Communications of the ACM asked me to expand it. Here’s the longer version. Source link lol
Read MoreApr 10, 2024NewsroomHardware Security / Linux Cybersecurity researchers have disclosed what they say is the “first native Spectre v2 exploit” against the Linux kernel on Intel systems that could be exploited to read sensitive data from the memory. The exploit, called Native Branch History Injection (BHI), can be used to leak arbitrary kernel memory at…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA