One Year Later, Dell’s Partner First For Storage Driving Engagement, Revenue Growth, Partners Say
by nlqip
‘We’re seeing some real focus from the Dell teams and much more in-person interactions. … Based on engagement and the Partner First For Storage, we expect to see significant growth within every business unit, with Dell, across the board,’ says CR Howdyshell, CEO of Dell Titanium partner Advizex. Dell Technologies channel partners told CRN that…
Read MoreOct 30, 2024Ravie LakshmananRansomware / Threat Intelligence Threat actors in North Korea have been implicated in a recent incident that deployed a known ransomware family called Play, underscoring their financial motivations. The activity, observed between May and September 2024, has been attributed to a threat actor tracked as Jumpy Pisces, which is also known as…
Read MoreThe North Korean state-sponsored hacking group tracked as ‘Andariel’ has been linked to the Play ransomware operation, using the RaaS to work behind the scenes and evade sanctions. A report from Palo Alto Networks and its Unit 42 researchers claims that Andariel might be either an affiliate of Play or acting as an initial access broker…
Read MoreLongtime Dell Technologies executive and general manager of Dell’s federal business, Jim Kelly, has jumped ship to lead Google’s public sector business. Dell Technologies’ general manager and senior vice president of the company’s federal business, Jim Kelly, has departed the infrastructure giant to help lead Google’s public sector business. “Today marks the beginning of my…
Read MoreThe $859 million deal seeks to enable MSPs to deliver improved detection and response to smaller customers, which are relentlessly targeted by cyberattacks, according to Levy and Secureworks CEO Wendy Thomas. The planned acquisition by Sophos of extended detection and response specialist Secureworks will accelerate the cybersecurity giant’s effort to bring improved XDR capabilities to…
Read MoreA new version of the FakeCall malware for Android hijacks outgoing calls from a user to their bank, redirecting them to the attacker’s phone number instead. The goal of the latest version remains to steal people’s sensitive information and money from their bank accounts. FakeCall (or FakeCalls) is a banking trojan with a focus on…
Read MoreCISA, through the Joint Cyber Defense Collaborative (JCDC), enabled swift, coordinated response and information sharing in the wake of a significant IT outage caused by a CrowdStrike software update. This outage, which impacted government, critical infrastructure, and industry across the globe, led to disruptions in essential services, including air travel, healthcare, and financial operations. Leveraging…
Read MoreCybersecurity researchers have uncovered an ongoing malvertising campaign that abuses Meta’s advertising platform and hijacked Facebook accounts to distribute information known as SYS01stealer. “The hackers behind the campaign use trusted brands to expand their reach,” Bitdefender Labs said in a report shared with The Hacker News. “The malvertising campaign leverages nearly a hundred malicious domains,…
Read MoreCRN staff compiled the top partner-friendly products that launched or were significantly updated over the last year. Now it’s up to solution providers to choose the winners. Application Performance and Observability As more applications run in hybrid-cloud and multi-cloud environments, maintaining application performance has becoming a more complex task. Application performance management and observability tools…
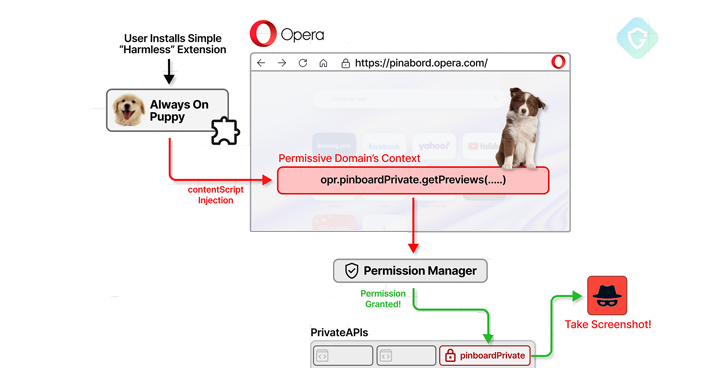
Read MoreOct 30, 2024Ravie Lakshmanan Browser Security / Vulnerability A now-patched security flaw in the Opera web browser could have enabled a malicious extension to gain unauthorized, full access to private APIs. The attack, codenamed CrossBarking, could have made it possible to conduct actions such as capturing screenshots, modifying browser settings, and account hijacking, Guardio Labs…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm