Microsoft released security updates to address vulnerabilities in multiple products. A cyber threat actor could exploit some of these vulnerabilities to take control of an affected system. Users and administrators are encouraged to review the following and apply the necessary updates: Source link lol
Read MoreAdobe has released security updates to address multiple vulnerabilities in Adobe software. A cyber threat actor could exploit some of these vulnerabilities to take control of an affected system. Users and administrators are encouraged to review the following Adobe Security Bulletins and apply the necessary updates: Source link lol
Read MoreIt’s no secret the internet doesn’t always bring out the best in people. The relative anonymity and global sprawl of digital life make it the ideal environment for scams, trolling and other kinds of bad behavior online. I host a podcast about cybersecurity, and was pondering how to put the issues we all face in…
Read MoreFortinet released security updates to address vulnerabilities in multiple products, including OS and FortiProxy. A cyber threat actor could exploit some of these vulnerabilities to take control of an affected system. CISA encourages users and administrators to review the following advisories and apply necessary updates: FR-IR-23-345 FortiClientMac – Lack of configuration file validation FG-IR-23-493 FortiOS…
Read MoreNo one’s too smart for a well-designed scam. Case in point, neuroscientist, triathlete Carina who thought the finance bro she met on Bumble was the one for her, but the only real thing was the money she lost. This week’s Tin Foil Swan dives into the sunk cost fallacy and the role it plays in…
Read MoreFortinet released security updates to address vulnerabilities in multiple products, including OS and FortiProxy. A cyber threat actor could exploit some of these vulnerabilities to take control of an affected system. CISA encourages users and administrators to review the following advisories and apply necessary updates: FR-IR-23-345 FortiClientMac – Lack of configuration file validation FG-IR-23-493…
Read MoreCISA released one Industrial Control Systems (ICS) advisory on April 9, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. CISA encourages users and administrators to review the newly released ICS advisory for technical details and mitigations. Source link lol
Read MoreThe implemented solution lowers the risk of data exfiltration by ensuring that, when data is processed in memory and encrypted, it remains inaccessible and unobtainable by any privileged accounts. In addition, the collaboration offers Cohesity customers a method to confirm the authenticity of their Intel SGX using the Intel Trust Authority. This system, equipped with…
Read MoreApr 09, 2024NewsroomCyber Espionage / Malware Human rights activists in Morocco and the Western Sahara region are the targets of a new threat actor that leverages phishing attacks to trick victims into installing bogus Android apps and serve credential harvesting pages for Windows users. Cisco Talos is tracking the activity cluster under the name Starry…
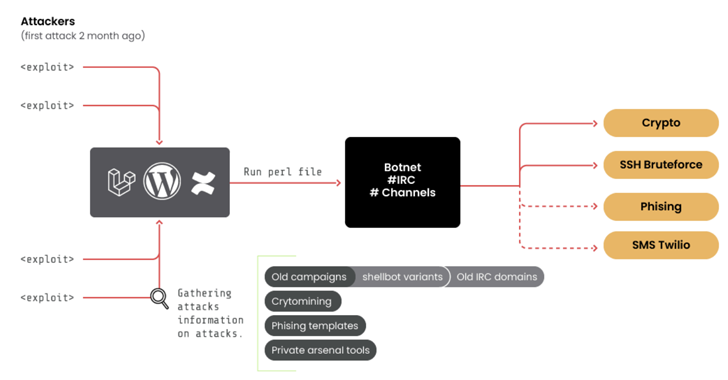
Read MoreApr 09, 2024NewsroomBotnet / Crypto Mining A threat group of suspected Romanian origin called RUBYCARP has been observed maintaining a long-running botnet for carrying out crypto mining, distributed denial-of-service (DDoS), and phishing attacks. The group, believed to be active for at least 10 years, employs the botnet for financial gain, Sysdig said in a report…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA