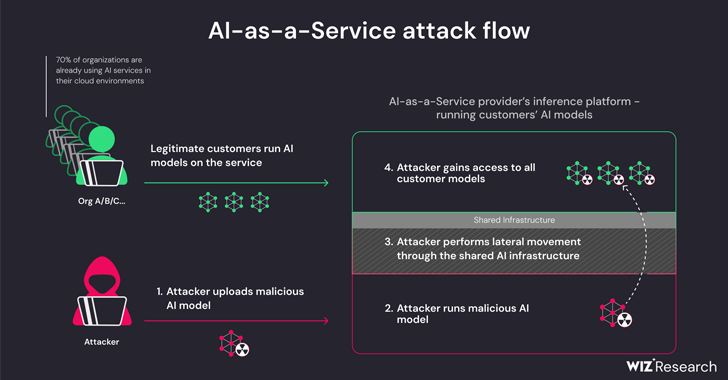
Apr 05, 2024NewsroomArtificial Intelligence / Supply Chain Attack New research has found that artificial intelligence (AI)-as-a-service providers such as Hugging Face are susceptible to two critical risks that could allow threat actors to escalate privileges, gain cross-tenant access to other customers’ models, and even take over the continuous integration and continuous deployment (CI/CD) pipelines. “Malicious…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-034 DATE(S) ISSUED: 04/05/2024 OVERVIEW: A vulnerability has been discovered in Broadcom Brocade Fabric OS that could allow for arbitrary code execution. Broadcom Brocade Fabric OS is the storage area networking firmware for Brocade Communications Systems’ Fibre Channel switch and Fibre Channel directors. Successful exploitation of this vulnerability could allow for arbitrary…
Read MoreA recent survey by Google and CSA (Cloud Security Alliance) has shed light on the evolving landscape of cybersecurity and the potential impact of Artificial Intelligence (AI). The survey targeted IT professionals, gauging their beliefs on how AI would influence corporate cybersecurity efforts. The findings revealed a spectrum of opinions, with a significant majority (63%)…
Read MoreThe IT security software vendor, on Wednesday, patched four critical vulnerabilities in Ivanti Connect Secure and Ivanti Policy Secure Gateways, the company’s flagship VPN solutions, capable of allowing remote code execution (RCE) and denial of service (DoS) attacks on the affected systems. Ivanti to undergo a security overhaul According to the open letter, published along…
Read MoreCompliance requirements are meant to increase cybersecurity transparency and accountability. As cyber threats increase, so do the number of compliance frameworks and the specificity of the security controls, policies, and activities they include. For CISOs and their teams, that means compliance is a time-consuming, high-stakes process that demands strong organizational and communication skills on top…
Read MoreMaybe the Phone System Surveillance Vulnerabilities Will Be Fixed It seems that the FCC might be fixing the vulnerabilities in SS7 and the Diameter protocol: On March 27 the commission asked telecommunications providers to weigh in and detail what they are doing to prevent SS7 and Diameter vulnerabilities from being misused to track consumers’ locations.…
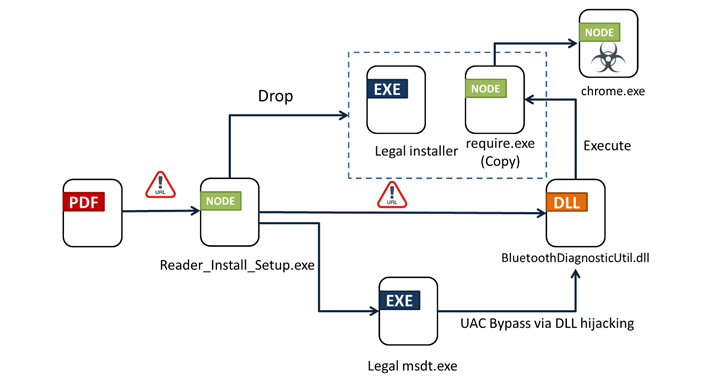
Read MoreApr 05, 2024NewsroomMalware / Endpoint Security Bogus installers for Adobe Acrobat Reader are being used to distribute a new multi-functional malware dubbed Byakugan. The starting point of the attack is a PDF file written in Portuguese that, when opened, shows a blurred image and asks the victim to click on a link to download the…
Read MoreApr 05, 2024NewsroomAdvanced Persistent Threat Multiple China-nexus threat actors have been linked to the zero-day exploitation of three security flaws impacting Ivanti appliances (CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893). The clusters are being tracked by Mandiant under the monikers UNC5221, UNC5266, UNC5291, UNC5325, UNC5330, and UNC5337. Another group linked to the exploitation spree is UNC3886. The Google…
Read MoreApr 05, 2024NewsroomCyber Espionage / Cybersecurity Financial organizations in the Asia-Pacific (APAC) and Middle East and North Africa (MENA) are being targeted by a new version of an “evolving threat” called JSOutProx. “JSOutProx is a sophisticated attack framework utilizing both JavaScript and .NET,” Resecurity said in a technical report published this week. “It employs the…
Read MoreApr 04, 2024NewsroomPhishing Attack / Malware An updated version of an information-stealing malware called Rhadamanthys is being used in phishing campaigns targeting the oil and gas sector. “The phishing emails use a unique vehicle incident lure and, in later stages of the infection chain, spoof the Federal Bureau of Transportation in a PDF that mentions…
Read MoreRecent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict