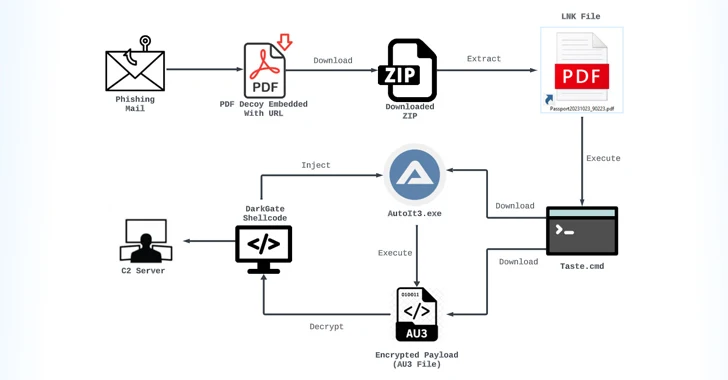
Apr 02, 2024NewsroomMalvertising / Threat Intelligence The threat actor known as TA558 has been attributed to a new massive phishing campaign that targets a wide range of sectors in Latin America with the goal of deploying Venom RAT. The attacks primarily singled out hotel, travel, trading, financial, manufacturing, industrial, and government verticals in Spain, Mexico,…
Read MoreAs we explore the trends of 2024, quantum computing emerges as a focal point, poised to revolutionize computational capabilities. Recent advancements, such as Atom Computing’s 1,225-qubit quantum computer, signal a transformative era. However, the emphasis shifts from sheer qubit count to the quality of qubits, highlighting the importance of error correction and practical applications. Quantum…
Read MoreApr 01, 2024NewsroomCryptocurrency / Financial Fraud The Indian government said it has rescued and repatriated about 250 citizens in Cambodia who were held captive and coerced into running cyber scams. The Indian nationals “were lured with employment opportunities to that country but were forced to undertake illegal cyber work,” the Ministry of External Affairs (MEA)…
Read MoreMagic Security Dust Adam Shostack is selling magic security dust. It’s about time someone is commercializing this essential technology. Posted on April 1, 2024 at 10:19 AM • 0 Comments Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreDespite a plethora of available security solutions, more and more organizations fall victim to Ransomware and other threats. These continued threats aren’t just an inconvenience that hurt businesses and end users – they damage the economy, endanger lives, destroy businesses and put national security at risk. But if that wasn’t enough – North Korea appears…
Read MoreIn the 2023 data breach, the attackers specifically accessed and exfiltrated the customer proprietary network information (CPNI) data which pertains to critical subscribers’ information maintained by the telecommunication companies in the US. The CPNI consists of information on the services used, the amount paid for the services, and the type of usage opted for. The…
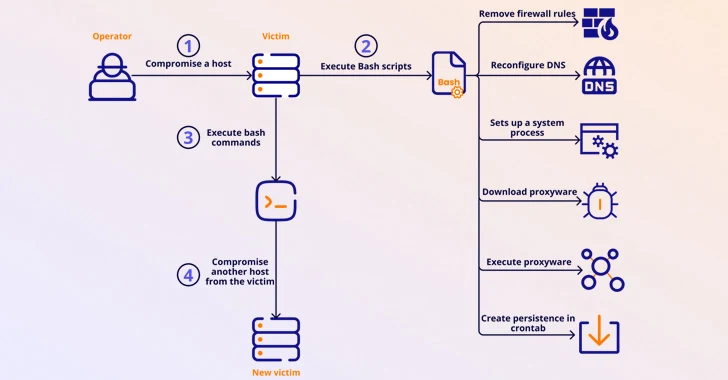
Read MoreApr 01, 2024NewsroomBotnet / Mobile Security Several malicious Android apps that turn mobile devices running the operating system into residential proxies (RESIPs) for other threat actors have been observed on the Google Play Store. The findings come from HUMAN’s Satori Threat Intelligence team, which said the cluster of VPN apps came fitted with a Golang…
Read MoreAI and machine learning (ML) optimizes processes by making recommendations for optimizing productivity, reducing cycles, and maximizing efficiency. AI also optimizes human capital by performing mundane & repetitive tasks 24×7 without the need for rest and minimizing human errors. There are numerous benefits as to how AI can benefit society. As much as AI can…
Read MoreIt’s just an unfortunate reality that it took a skills shortage for the cybersecurity industry to realize that bias recruitment has long been a problem and it needs to be addressed for the workforce to be more diverse, according to Michael Page Australia regional director George Kauye. “I think most of us in the workforce…
Read MoreGoogle recently announced the general availability of Duet AI for Developers and Duet AI in Security Operations, marking a significant advancement in the realm of artificial intelligence (AI) designed to bolster productivity for developers and security professionals. Let’s delve deeper into how these innovative AI tools can transform these respective fields. Duet AI for Developers:…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA