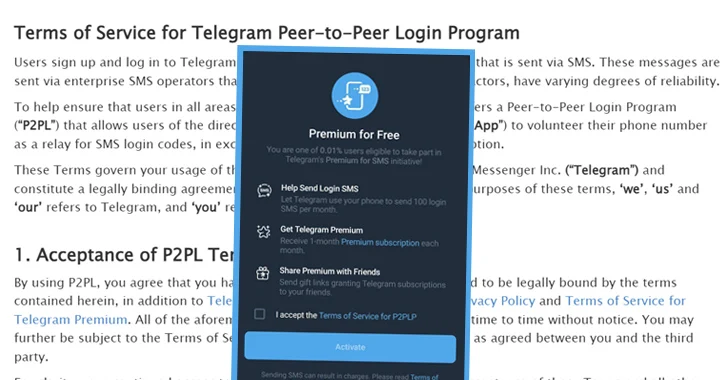
“Firstly, people may have both personal devices and work devices but device management or policy from the IT team might mean each device is equally able to access corporate resources, or there is no such policy, so employees would just use whichever is most convenient,” Lohokare said. “The second big reason would be the continued…
Read MoreMar 28, 2024NewsroomHardware Security / Vulnerability Cybersecurity researchers from ETH Zurich have developed a new variant of the RowHammer DRAM (dynamic random-access memory) attack that, for the first time, successfully works against AMD Zen 2 and Zen 3 systems despite mitigations such as Target Row Refresh (TRR). “This result proves that AMD systems are equally…
Read MoreMar 28, 2024The Hacker NewsSecrets Management / Zero Trust In the whirlwind of modern software development, teams race against time, constantly pushing the boundaries of innovation and efficiency. This relentless pace is fueled by an evolving tech landscape, where SaaS domination, the proliferation of microservices, and the ubiquity of CI/CD pipelines are not just trends…
Read MoreHowever, the latest court documents indicate that Meta’s IAAP program expanded to target encrypted analytics traffic from competitors beyond Snapchat, including YouTube and Amazon. Allegations suggest that Facebook employees developed customized client and server-side code based on Onavo’s VPN proxy app and server stack. The code included a client-side “kit” that installed a “root” certificate…
Read MoreHardware Vulnerability in Apple’s M-Series Chips It’s yet another hardware side-channel attack: The threat resides in the chips’ data memory-dependent prefetcher, a hardware optimization that predicts the memory addresses of data that running code is likely to access in the near future. By loading the contents into the CPU cache before it’s actually needed, the…
Read MoreMar 28, 2024NewsroomTechnology / Data Privacy In June 2017, a study of more than 3,000 Massachusetts Institute of Technology (MIT) students published by the National Bureau for Economic Research (NBER) found that 98% of them were willing to give away their friends’ email addresses in exchange for free pizza. “Whereas people say they care about…
Read MoreSimilarly, business or resource decisions, often made outside the realm of the cybersecurity team, sometimes lead to vulnerabilities or compromises. Accepting accountability in such scenarios is a part of our job, but it doesn’t make it any less challenging. It requires a delicate balance of maintaining a strong security posture while navigating the complexities of…
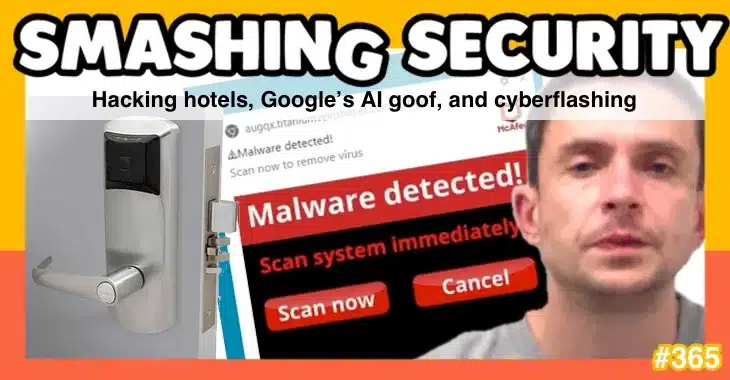
Read MoreSecurity researchers find a way to unlock millions of hotel rooms, the UK introduces cyberflashing laws, and Google’s AI search pushes malware and scams. All this and much much more is discussed in the latest edition of the “Smashing Security” podcast by cybersecurity veterans Graham Cluley and Carole Theriault, joined this week by T-Minus’s Maria…
Read MoreYou encounter the love of your life online, never meeting them in person. Or you get an email about an inheritance from a distant relative you didn’t know existed. Maybe it’s an attractive gig at a company you’ve never heard of before. Whatever the initial beat of this crime, when you go to meet your…
Read MoreThe Qilin ransomware group has targeted The Big Issue, a street newspaper sold by the homeless and vulnerable. As The Record reports, a post on Qilin’s dark web leak site claimed the gang has stolen 550 GB of confidential data from Qilin has published photographs of what seems to be the driving license and salary…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA