Feb 16, 2024NewsroomCybersecurity / Data Breach The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has revealed that an unnamed state government organization’s network environment was compromised via an administrator account belonging to a former employee. “This allowed the threat actor to successfully authenticate to an internal virtual private network (VPN) access point,” the agency said…
Read MoreFeb 16, 2024NewsroomBotnet / Network Security The U.S. government on Thursday said it disrupted a botnet comprising hundreds of small office and home office (SOHO) routers in the country that was put to use by the Russia-linked APT28 actor to conceal its malicious activities. “These crimes included vast spear-phishing and similar credential harvesting campaigns against…
Read MoreCISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-21412 Microsoft Windows Internet Shortcut Files Security Feature Bypass Vulnerability CVE-2024-21351 Microsoft Windows SmartScreen Security Feature Bypass Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. …
Read MoreMicrosoft has released security updates to address vulnerabilities in multiple products. A cyber threat actor could exploit some of these vulnerabilities to take control of an affected system. CISA encourages users and administrators to review Microsoft’s February Security Update Guide and apply the necessary updates. Source link ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreCISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2020-3259 Cisco ASA and FTD Information Disclosure Vulnerability CVE-2024-21410 Microsoft Exchange Server Privilege Escalation Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive…
Read MoreAdobe has released security updates to address vulnerabilities in Adobe software. A cyber threat actor could exploit some of these vulnerabilities to take control of an affected system. CISA encourages users and administrators to review the following Adobe Security Bulletins and apply the necessary updates. Source link ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreCISA released seventeen Industrial Control Systems (ICS) advisories on February 15, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-24-046-01 Siemens SCALANCE W1750D ICSA-24-046-02 Siemens SIDIS Prime ICSA-24-046-03 Siemens SIMATIC RTLS Gateways ICSA-24-046-04 Siemens CP343-1 Devices ICSA-24-046-05 Siemens Location Intelligence ICSA-24-046-06 Siemens Unicam FX ICSA-24-046-07 Siemens Tecnomatix Plant…
Read MoreCISA and MS-ISAC Release Advisory on Compromised Account Used to Access State Government Organization | CISA
by nlqip
Today, CISA and the Multi-State Information Sharing & Analysis Center (MS-ISAC) released a joint Cybersecurity Advisory (CSA), Threat Actor Leverages Compromised Account of Former Employee to Access State Government Organization to provide network defenders with the tactics, techniques, and procedures (TTPs) utilized by a threat actor and methods to protect against similar exploitation. Following an incident…
Read MoreThreat Actor Leverages Compromised Account of Former Employee to Access State Government Organization | CISA
by nlqip
SUMMARY The Cybersecurity and Infrastructure Security Agency (CISA) and the Multi-State Information Sharing & Analysis Center (MS-ISAC) conducted an incident response assessment of a state government organization’s network environment after documents containing host and user information, including metadata, were posted on a dark web brokerage site. Analysis confirmed that an unidentified threat actor compromised network…
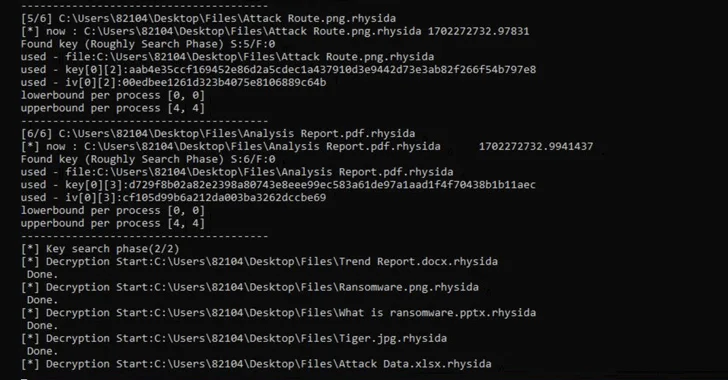
Read MoreGood news for organisations who have fallen victim to the notorious Rhysida ransomware. A group of South Korean security researchers have uncovered a vulnerability in the infamous ransomware. This vulnerability provides a way for encrypted files to be unscrambled. Researchers from Kookmin University describe how they exploited an implementation flaw in Rhysida’s code to regenerate…
Read MoreRecent Posts
- Singtel Hack Highlights Rising Threat of Chinese Cyber Attacks on Global Telecoms
- South Korea Fines Meta $15.67M for Illegally Sharing Sensitive User Data with Advertisers
- Enhancing Cyber Resilience in Energy and Utilities Organizations
- Google Cloud to Enforce Multi-Factor Authentication by 2025 for All Users
- Analysis: Intel’s AI Chip Efforts Stall As AMD Gets A Boost Against Nvidia