The capability is developed by leveraging a combination of heuristics and proprietary AI layers to evaluate prompts and identify abuses and threats. “Firewall for AI will protect against Model Denial of Service and Sensitive Information Disclosure, which leverage tools and features available to all customers as part of the Web Application Firewall,” the Cloudflare spokesperson said.…
Read MoreMar 04, 2024The Hacker NewsSaaS Security / Vulnerability Assessment A company’s lifecycle stage, size, and state have a significant impact on its security needs, policies, and priorities. This is particularly true for modern mid-market companies that are either experiencing or have experienced rapid growth. As requirements and tasks continue to accumulate and malicious actors remain…
Read MoreLLM Prompt Injection Worm Researchers have demonstrated a worm that spreads through prompt injection. Details: In one instance, the researchers, acting as attackers, wrote an email including the adversarial text prompt, which “poisons” the database of an email assistant using retrieval-augmented generation (RAG), a way for LLMs to pull in extra data from outside its…
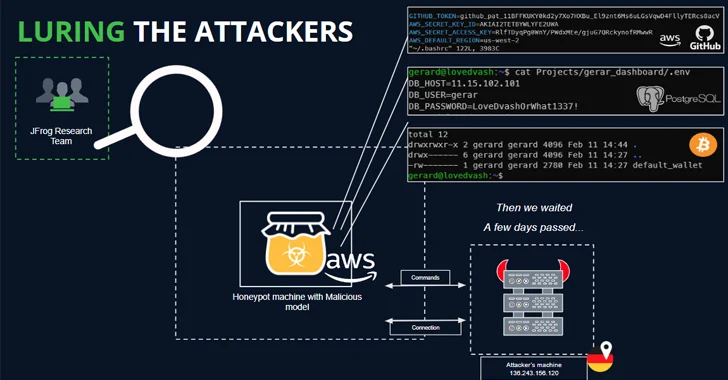
Read MoreMar 04, 2024NewsroomAI Security / Vulnerability As many as 100 malicious artificial intelligence (AI)/machine learning (ML) models have been discovered in the Hugging Face platform. These include instances where loading a pickle file leads to code execution, software supply chain security firm JFrog said. “The model’s payload grants the attacker a shell on the compromised…
Read More“People in CISO circles absolutely talk a lot about liability. We’re all concerned about it,” Deaner acknowledges. “People are taking the changes to those regulations very seriously because they’re there for a reason.” In Nagler’s view, more defined regulatory parameters might actually turn out to be “the best gift” for CISOs. “Leaders are taking notice…
Read MoreU.S. cybersecurity and intelligence agencies have warned of Phobos ransomware attacks targeting government and critical infrastructure entities, outlining the various tactics and techniques the threat actors have adopted to deploy the file-encrypting malware. “Structured as a ransomware as a service (RaaS) model, Phobos ransomware actors have targeted entities including municipal and county governments, emergency services,…
Read MoreVideo As the specter of AI-generated disinformation looms large, tech giants vow to crack down on fabricated content that could sway voters and disrupt elections taking place around the world this year 01 Mar 2024 As a record number of people across the world will go to the polls this year, concerns rise about the…
Read MoreMar 02, 2024NewsroomSpyware / Privacy A U.S. judge has ordered NSO Group to hand over its source code for Pegasus and other products to Meta as part of the social media giant’s ongoing litigation against the Israeli spyware vendor. The decision, which marks a major legal victory for Meta, which filed the lawsuit in October…
Read MoreMar 02, 2024NewsroomCybercrime / Social Engineering The U.S. Department of Justice (DoJ) on Friday unsealed an indictment against an Iranian national for his alleged involvement in a multi-year cyber-enabled campaign designed to compromise U.S. governmental and private entities. More than a dozen entities are said to have been targeted, including the U.S. Departments of the…
Read More“Microsoft hasn’t given up on securing the admin-to-kernel boundary, though,” researchers from Avast explain. “Quite the opposite. It has made a great deal of progress in making this boundary harder to cross. Defense-in-depth protections, such as DSE (Driver Signature Enforcement) or HVCI (Hypervisor-Protected Code Integrity), have made it increasingly difficult for attackers to execute custom…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA