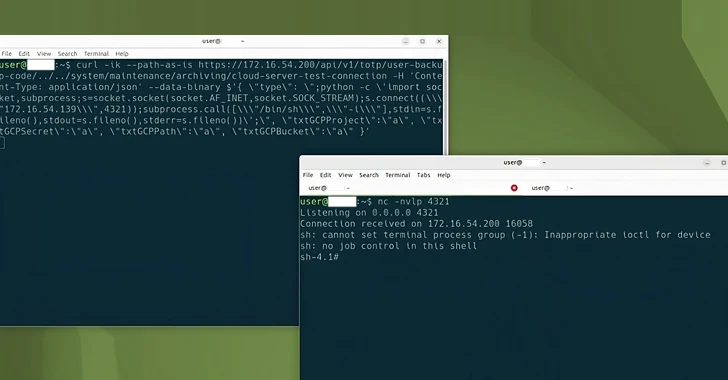
More than a decade ago, the concept of the ‘blameless’ postmortem changed how tech companies recognize failures at scale. John Allspaw, who coined the term during his tenure at Etsy, argued postmortems were all about controlling our natural reaction to an incident, which is to point fingers: “One option is to assume the single cause…
Read MoreDo you ever play computer games such as Halo or Gears of War? If so, you’ve definitely noticed a game mode called Capture the Flag that pits two teams against each other – one that is in charge of protecting the flag from adversaries who attempt to steal it. This type of exercise is also…
Read MoreMar 01, 2024NewsroomRootkit / Threat Intelligence The Five Eyes (FVEY) intelligence alliance has issued a new cybersecurity advisory warning of cyber threat actors exploiting known security flaws in Ivanti Connect Secure and Ivanti Policy Secure gateways, noting that the Integrity Checker Tool (ICT) can be deceived to provide a false sense of security. “Ivanti ICT…
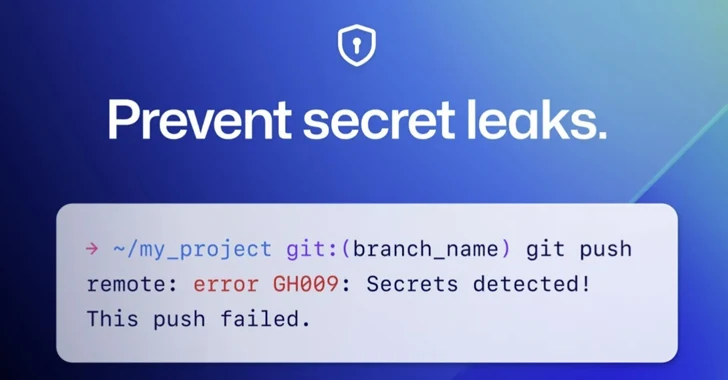
Read MoreMar 01, 2024NewsroomDevSecOps / Cybersecurity GitHub on Thursday announced that it’s enabling secret scanning push protection by default for all pushes to public repositories. “This means that when a supported secret is detected in any push to a public repository, you will have the option to remove the secret from your commits or, if you…
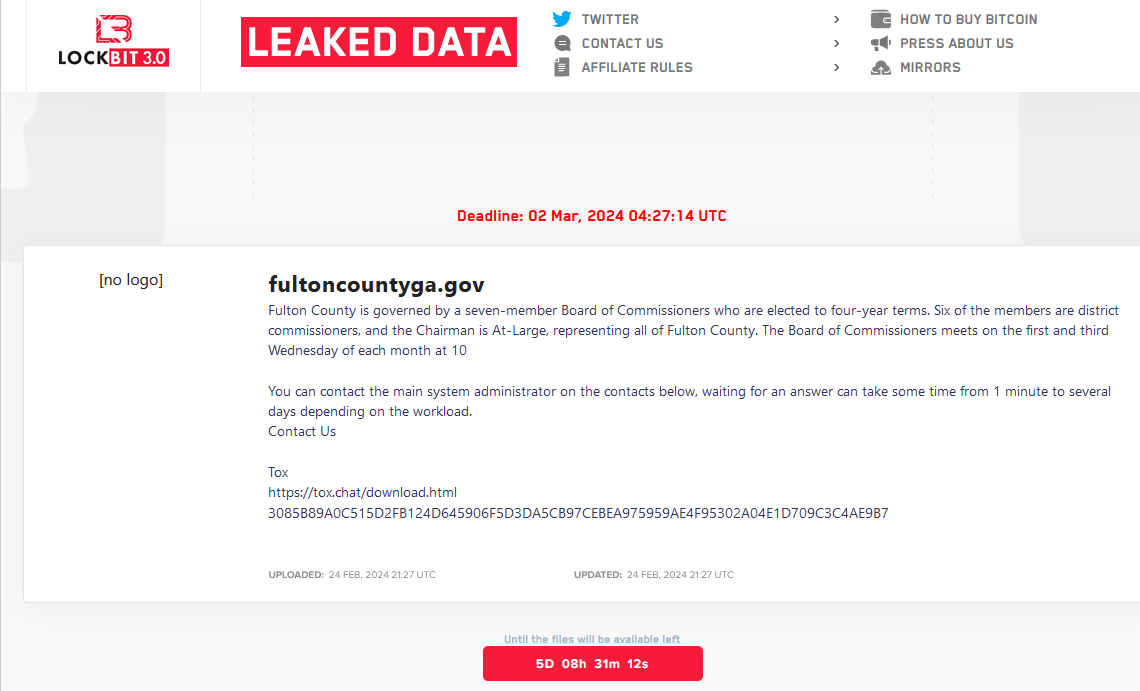
Read MoreThe ransomware group LockBit told officials with Fulton County, Ga. they could expect to see their internal documents published online this morning unless the county paid a ransom demand. LockBit removed Fulton County’s listing from its victim shaming website this morning, claiming the county had paid. But county officials said they did not pay, nor…
Read MoreThe report points to the need for companies to patch open- source software and components, said Mike McGuire, senior software solutions manager at Synopsys Software Integrity Group. “It’s unpatched vulnerabilities that have led to some of the most significant data breaches,” he said. “Arguably, it’s the duty of these companies to address vulnerabilities, especially if…
Read MoreIn an era of unprecedented technological advancement, the adoption of AI continues to rise. However, with the proliferation of this powerful technology, a darker side is emerging. Increasingly, malicious actors are using AI to enhance every stage of an attack. Cybercriminals are using AI to support a multitude of malicious activities, ranging from bypassing algorithms that detect…
Read MoreCISA and Partners Release Advisory on Threat Actors Exploiting Ivanti Connect Secure and Policy Secure Gateways Vulnerabilities | CISA
by nlqip
Today, CISA and the following partners released joint Cybersecurity Advisory Threat Actors Exploit Multiple Vulnerabilities in Ivanti Connect Secure and Policy Secure Gateways: Federal Bureau of Investigation (FBI) Multi-State Information Sharing & Analysis Center (MS-ISAC) Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) United Kingdom National Cyber Security Centre (NCSC-UK) Canadian Centre for Cyber…
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2023-29360 Microsoft Streaming Service Untrusted Pointer Dereference Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of…
Read MoreToday, CISA, the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) released a joint Cybersecurity Advisory (CSA), #StopRansomware: Phobos Ransomware, to disseminate known tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs), which are from incident response investigations tied to Phobos ransomware activity from as recently as February,…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA