AT&T Cybersecurity featured a dynamic cyber mashup panel with Akamai, Palo Alto Networks, SentinelOne, and the Cloud Security Alliance. We discussed some provocative topics around Artificial Intelligence (AI) and Machine Learning (ML) including responsible AI and securing AI. There were some good examples of best practices shared in an emerging AI world like implementing Zero Trust architecture and…
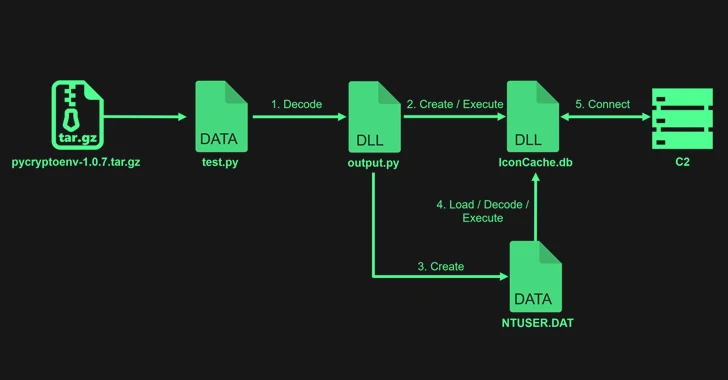
Read MoreFeb 29, 2024NewsroomMalware / Endpoint Security The notorious North Korean state-backed hacking group Lazarus uploaded four packages to the Python Package Index (PyPI) repository with the goal of infecting developer systems with malware. The packages, now taken down, are pycryptoenv, pycryptoconf, quasarlib, and swapmempool. They have been collectively downloaded 3,269 times, with pycryptoconf accounting for…
Read MoreFeb 29, 2024NewsroomCyber Espionage / Malware A previously undocumented threat actor dubbed SPIKEDWINE has been observed targeting officials in European countries with Indian diplomatic missions using a new backdoor called WINELOADER. The adversary, according to a report from Zscaler ThreatLabz, used a PDF file in emails that purported to come from the Ambassador of India,…
Read MoreHowever, with many CISOs and their teams already feeling under pressure from the mounting responsibilities of protecting organizations, coming to grips with the growing raft of regulations and requirements, can be overwhelming, said Insight Enterprises’ Rader. “There’s a lot to ingest from multiple agencies in the US, EU requirements and disclosure requirements and even certain…
Read MoreAt least two different suspected China-linked cyber espionage clusters, tracked as UNC5325 and UNC3886, have been attributed to the exploitation of security flaws in Ivanti Connect Secure VPN appliances. UNC5325 abused CVE-2024-21893 to deliver a wide range of new malware called LITTLELAMB.WOOLTEA, PITSTOP, PITDOG, PITJET, and PITHOOK, as well as maintain persistent access to compromised…
Read MoreU.S. President Joe Biden has issued an Executive Order that prohibits the mass transfer of citizens’ personal data to countries of concern. The Executive Order also “provides safeguards around other activities that can give those countries access to Americans’ sensitive data,” the White House said in a statement. This includes sensitive information such as genomic…
Read MoreSmashing Security podcast #361: Wireless charging woe, AI romance apps, and ransomware revisited
by nlqip
Your smartphone may be toast – if you use a hacked wireless charger, we take a closer look at the latest developments in the unfolding LockBit ransomware drama, and Carole dips her toe into online AI romance apps. All this and much much more is discussed in the latest edition of the “Smashing Security” podcast…
Read MoreVOLTZITE relies heavily on living-off-the-land techniques and hands-on post-compromise actions with the goal of expanding their access from the IT network perimeter to the OT network. The group is believed to be in operation since at least 2021 and has targeted critical infrastructure entities in Guam, the United States, and other countries with a focus…
Read MoreCovered persons: The program will be defined categorically to include certain classes of entities and individuals subject to the jurisdiction, direction, ownership, or control of countries of concern, if data to these persons will place that data within the reach of the countries of concern. The EO defines four categories of covered persons: “An entity…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-024 DATE(S) ISSUED: 02/28/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, which could allow for arbitrary code execution. Successful exploitation of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user an attacker could then install…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA