Matthew Perry’s official Twitter account was hijacked by scammers this week who attempted to solicit donations from well-meaning fans of the much-loved late actor. The post, which has since been removed from Perry’s Twitter account, asked for cryptocurrency donations “to support our mission in battling addiction.” The tweet claimed to be signed by “The Matthew…
Read MoreToday, CISA released a Resource Guide for Cybersecurity Clinics to outline ways CISA can partner with and support cybersecurity clinics and their clients. University cybersecurity clinics train students from diverse backgrounds and academic expertise to strengthen the digital defenses of non-profits, hospitals, municipalities, small businesses, and other under-resourced organizations. They can help address the national…
Read MoreGraham Cluley Security News is sponsored this week by the folks at Cynet. Thanks to the great team there for their support! George Tubin, Director of Product Strategy, Cynet Thorough, independent tests are a vital resource as cybersecurity leaders and their teams evaluate vendors’ abilities to guard against increasingly sophisticated threats to their organization. And…
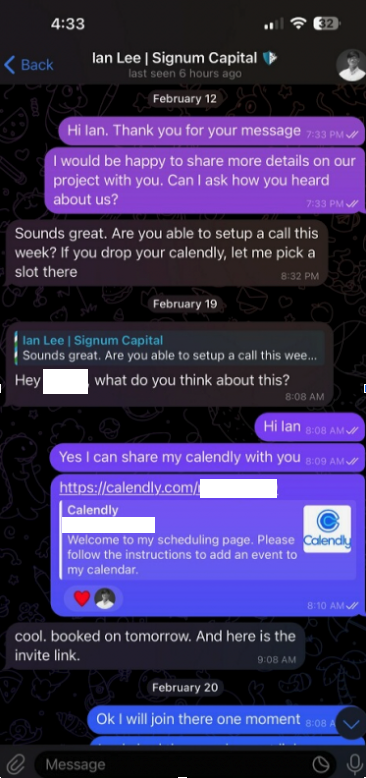
Read MoreMalicious hackers are targeting people in the cryptocurrency space in attacks that start with a link added to the target’s calendar at Calendly, a popular application for scheduling appointments and meetings. The attackers impersonate established cryptocurrency investors and ask to schedule a video conference call. But clicking the meeting link provided by the scammers prompts…
Read MoreFeb 28, 2024NewsroomCyber Espionage / Malware An Iran-nexus threat actor known as UNC1549 has been attributed with medium confidence to a new set of attacks targeting aerospace, aviation, and defense industries in the Middle East, including Israel and the U.A.E. Other targets of the cyber espionage activity likely include Turkey, India, and Albania, Google-owned Mandiant…
Read MoreA half-century ago, most corporations were paper-native: Their business processes all executed on paper from both back office (accounting) to go-to-market functions (sales and marketing). Their businesses were location-native: Revenue was often generated in some form of person-to-person transactions, supported by that paper-native back office. As first computers, and then networks, became popular and affordable,…
Read MoreFeb 28, 2024NewsroomRansomware / Healthcare The U.S. government is warning about the resurgence of BlackCat (aka ALPHV) ransomware attacks targeting the healthcare sector as recently as this month. “Since mid-December 2023, of the nearly 70 leaked victims, the healthcare sector has been the most commonly victimized,” the government said in an updated advisory. “This is…
Read MoreWe’re pleased to announce the availability of the 2023 AT&T Cybersecurity Insights Report: Focus on Energy and Utilities. The report examines the edge ecosystem, surveying energy and utilities IT leaders from around the world, and provides benchmarks for assessing your edge computing plans. This is the 12th edition of our vendor-neutral and forward-looking report. Last…
Read MoreFeb 28, 2024The Hacker NewsWebinar / Privacy In today’s digital era, data privacy isn’t just a concern; it’s a consumer demand. Businesses are grappling with the dual challenge of leveraging customer data for personalized experiences while navigating a maze of privacy regulations. The answer? A privacy-compliant Customer Data Platform (CDP). Join us for a transformative…
Read MoreA Cyber Insurance Backstop In the first week of January, the pharmaceutical giant Merck quietly settled its years-long lawsuit over whether or not its property and casualty insurers would cover a $700 million claim filed after the devastating NotPetya cyberattack in 2017. The malware ultimately infected more than 40,000 of Merck’s computers, which significantly disrupted…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA