“In terms of phishing, while I believe that the threat remains in the critical category for organizations, because many phishing campaigns seek account credentials as the primary outcome, if cybercriminals have access to valid account credentials via other means (as noted in the report), the need to run a phishing campaign will decline,” said Michael Sampson,…
Read MoreThis article looks at ransomware trends of 2023, such as an increase in supply chain attacks, the use of double extortion, law enforcement actions against large networks, a focus on small and medium-sized businesses more than ever and calls for payments to be banned in lieu of ransomware. 1. Double Extortion Became a Key Tactic…
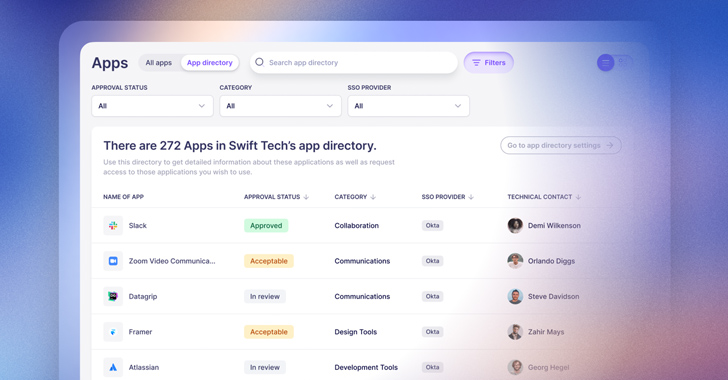
Read MoreWith SaaS applications now making up the vast majority of technology used by employees in most organizations, tasks related to identity governance need to happen across a myriad of individual SaaS apps. This presents a huge challenge for centralized IT teams who are ultimately held responsible for managing and securing app access, but can’t possibly…
Read MoreDetails of a Phone Scam First-person account of someone who fell for a scam, that started as a fake Amazon service rep and ended with a fake CIA agent, and lost $50,000 cash. And this is not a naive or stupid person. The details are fascinating. And if you think it couldn’t happen to you,…
Read MoreCompany: Bonanza CasinoIndustry: GamingCountry: Reno, NevadaEmployees: 150+Web: bonanzacasino.com Download PDF A favorite with Reno locals, the Bonanza Casino, a family owned and operated business, first opened its doors in 1973. The casino is home to two restaurants, the Cactus Creek Prime Steakhouse, ten-time “Best of Nevada” winner and the Branding Iron Café. As an independent boutique casino,…
Read MoreHow To Why and how are we subjected to so much disinformation nowadays, and is there a way to spot the fakes? 20 Feb 2024 • , 6 min. read One of the best things about the internet is that it’s an expansive repository of knowledge – and this wealth of knowledge is almost never…
Read More2024 has started out with the highest number of January attacks we’ve ever recorded, with 76 attacks representing a 130% increase compared to 2022’s figures. Education topped the list of targeted industries, followed by healthcare and manufacturing. LockBit was the most active ransomware group this month, with Akira knocking BlackCat off the second-place spot for…
Read MoreAI is among the most disruptive technologies of our time. While AI/ML has been around for decades, it has become a hot topic with continued innovations in generative AI (GenAI) from start-up OpenAI to tech giants like Microsoft, Google, and Meta. When large language models (LLMs) combined with big data and behavior analytics, AI/ML can…
Read MoreCybersecurity for Healthcare—Diagnosing the Threat Landscape and Prescribing Solutions for Recovery
by nlqip
On Thanksgiving Day 2023, while many Americans were celebrating, hospitals across the U.S. were doing quite the opposite. Systems were failing. Ambulances were diverted. Care was impaired. Hospitals in three states were hit by a ransomware attack, and in that moment, the real-world repercussions came to light—it wasn’t just computer networks that were brought to…
Read MoreMSP vs MSSP Solutions: Which Is Right For Your Business? Securing a business from cyberthreats is a vital activity for any organization, regardless of size or sector. But often, firms lack the necessary skills or resources to achieve this on their own. This is where turning to managed providers can prove hugely beneficial. Smaller companies…
Read MoreRecent Posts
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners